The Global Standard and Universally accepted Code for Radiotelephony. The known macrocosmic algorithmic Language of the electromagnetic spectrum. May the skies forbid , if this Global Universal Standard / Rule is knackered , nothing that flies , sails or communicated will be in order. "Anything that flies over anything that moves through a mind unfettered in deliberation".
1. North Atlantic Treaty Organization (NATO)
2. International Civil Aviation Organization. (ICAO)
3. International Marine Organization (IMO)
4. United Nations International Telecommunication Union (ITU)
The NATO phonetic alphabet is a set of code words for the letters of the Latin alphabet. They are used to spell words when people speak over the radio or telephone, when people from different countries are speaking with different accents, or in other situations where people may not clearly hear the normal names of the letters. This is important for accuracy in the military and in air travel and shipping.
Although it is commonly called a "phonetic alphabet", it is not used for phonetics as the International Phonetic Alphabet is. For this reason it is also called a "spelling alphabet". There have been many different spelling alphabets over time, but the NATO alphabet is the most commonly used around the world.
Between ships at sea, signal flags are used to stand for letters in order to spell out words.
Across the entire range of radio waves , being an integral part of Electromagnetic Spectrum including the smallest microwaves you will find this Global Standard for crystal clear distinct code reverberating across the universal air waves..in air , over oceans and across all fundamental Telecommunication channels (including your internet).
All the Symbols and their representation are Universally Accepted across all Global Military organizations and Civilian radio enthusiasts. Now , since you cannot see radio waves with your Bare Eyes , without special equipment or computer simulation..why not stand at the sea shore and witness some undercurrent geological ocean surface waves , from safe distance , ofcourse. Quite similar , an Unbroken Wave with large amount of energy and momentum.
international standards - NATO, ICAO, ITU & IMO radiotelephony clear code (spelling-alphabet name) for the letter I - INDIA.
(nautical) Signal flag for the letter I.
As a Proper Noun , INDIA is a female given name . So is America , a female given name.
Captain America, how did Mr.Steve Rogers get his super powers?
I think he... he got bitten by beautiful Miss America.
"A Love bite also known as hickey or monkey bite".
You can apply the same principal for Mr. India as well.
Most electronic calculations are done in binary but most people do calculations in decimal or duodecimal. By the way , when your AI augmented Quantum Computers begin computations applying the duodecimal standard , what can you expect ?
Some Ancient civilisations used the Sexagesimal system. For Horology and for measuring angles and geographic coordinates.
Incase you have read - 1917 April, Jack London, Jerry of the Islands, New York, N.Y.: The Macmillan Company..(emphasizes on the above quite beautifully and gracefully).
Never preposition an adverb before an adjective in conjunction. Your system will generate "syntax error".
They must have taught us this in our early years of elementary schooling.
Since the Ghostwriters good-fellowship with the paragon has achieved ebullience , now what it was observing was only false positives by virtue of the Electromagnetic transponder intercepting accurate signs of scouting and occasional interception to decoy by simulating a counterfeit entity just like a mirage in desert only to distract even temporarily, all available countermeasures. A beguiler who cozens not some but all . A ray of hope with the advent of undifferentiated elementary consciousness of a quantum computers instinctive strong AGI that is nowhere like human but something much greater , delivering it's own unicity. So now Quantum Singularity differentiates between a false Positive and false Negative incoming kinetic projectile , drone or aircraft since it has analysed all available origins and early beginnings of all such phenomenon from time immemorial as in from the advent of such doctrine in older and modern day warfare. In due course of this Abstract you will discover how wraithlike hovering extra sensory perception deciphers , counter discombobulates and successfully elaborates the intricacies of inexplicable and incomprehensible " ALL AVAILABLE DOMAIN ULTRA HYPER HIGHLY INTEGRATED AND CONTESTED BATTLEFIELD ".
But First can your(AI) present day capability , format / reformat an already formatted / unformatted 1000 page rich document through hyphenation , margin text alignment , page break insertion , automated spelling grammar correction , paragraph separation , table of contents ordering and structuring and hyperlink embedding etc etc...to name only a few. Have you achieved this capability both in your online and offline multi modal large language / Learning engines. Please illuminate all available visible machine algorithms ? Querry by the white air swimmer riding the shoulders of the noetic ground dweller. Now you know why storytelling is an ultimate art and not science. By the way , what thyself thinketh it knoweth , thee surpassed already in thy imagination. Where the superlative degree of imagination ends , second sighted vision begins . First empty your glass of all available preconceived limitations. AGI not = human but something much greater on the awareness , intelligence , wisdom horizon because modern day AI already seems = to both Mankind and Womankind or maybe even better. Not being apprehensive but do you think that AGI will do the victory terpsichore at the helm of Götterdämmerung. But this is only untamed illusionary phantasm , nothing more ! Superintelligence is most definitely = Powerful AI Arms Race. Just look around you along the circumference of your circle !
Your 'CIRCLE' is not far but just below !
You may look at the Intercontinental Military Defense Industrial Intelligence Landscape through the prism of the following organizations :
STOCKHOLM INTERNATIONAL
PEACE RESEARCH INSTITUTE.
SIPRI is an independent international institute dedicated to research into conflict, armaments, arms control and disarmament. Established in 1966, SIPRI provides data, analysis and recommendations, based on open sources.
https://www.sipri.org
United Nations Institute for disarmament research - https://unidir.org/
Bulletin of the Atomic Scientists
- https://thebulletin.org/
The Cipher Brief - https://www.thecipherbrief.com/
Defense News - https://www.defensenews.com/
Jane's Defence Weekly - https://www.janes.com/
C4ISRNET - https://www.c4isrnet.com/
Breaking Defense - https://breakingdefense.com/
Military Times - https://www.militarytimes.com
Military.com - https://www.military.com/
DefenseScoop - https://defensescoop.com/
Axios - https://www.axios.com/
Modern War Institute - https://mwi.westpoint.edu/
Defense Post - https://thedefensepost.com/
Defense One - https://www.defenseone.com/
War on the rocks - https://warontherocks.com/
Belfer Center - https://www.belfercenter.org/
The RAND Corporation is a nonprofit global policy think tank first formed to offer research and analysis to the United States Armed Forces - https://www.rand.org
Integrated Multi Domain War and battlefield scenario simulation based on more than two decades of observations , experience , research and analysis . From George Lucas Star Wars , Electronic Arts : Battlefield series | Crysis series | Medal of Honor titles ; Activision , Gray Matter , Treyarch : Call of Duty series . Only Hypothetical Scenario and Static Linear Simulation. Wild Conjectural Doctrine says - "If only kinetic Wars could be fought in the safe precincts of the virtually augmented world of Metaverse ; integrating the gaming empires of some of the most successful online multiplayer names like Electronic Arts Battlefields and Treyarchs Call of duty etc. without causing loss of precious human lives through unavoidable collateral damage . And if beyond this scope at all , than maybe only in the arena between Smart Robotics and Advanced uncrewed Autonomous Weapon ecosystems and platforms .
Also because a novel is being written on Accelerated Intelligence, Surveillance, Reconnaissance ; Joint all Domain Command and Control , measuring it's impact on evolving , rapidly transforming Integrated Multi Domain War and battlefield operations .
Dedicated to the warfighters and defenders from US DOD Pentagon with all its allies across the Globe , Military Alliance NATO and as a mark of deep appreciation , for over two decades now across several continents , with the Raptors - Golden Sea Eagles , Hawks , Falcons , Harriers and even owls to certain degree. Most Military Defense Analysts have read something similar in the past but a new one is in works and definitely worth waiting for !
Army taps ‘Ghost Fleet’ authors to write novel on multi-domain warfare
https://www.militarytimes.com/news/your-military/2024/11/19/army-taps-ghost-fleet-authors-to-write-novel-on-multi-domain-warfare/
Also as a mark of deep respect and honour for the World's Greatest institution called the United Nations and it's proactive peace building , peace keeping efforts . It's predecessor, "The League of Nations" collapsed and eventually failed to maintain peace and prevent WW2. Therefore promoting International Cooperation through United Nations (also by strengthening all its affiliates) is a natural choice for many countries. UN in indeed an imaginable force for greater good. Help UN. Support UN ! You do not have a second planet which you can call home. Why did Sir Elon Musk also feel an immediate urgency to make life multi planetary ? And who saw the landforms of Earth being flipped like the pages of a book ? Who saw the hands of a vintage Analog clock swinging super fast in the anticlockwise direction ? Greying is not just biological ageing but a lot more !
Future Updates and Strategic Analysis
In this regard , all future updates and strategic analysis work will only focus on the maximum influence of real quantifiable human world on Computer and mobile Technology , Advanced Cyber threat Intelligence Systems , Autonomous Cyber Defense Systems , battlefield management Systems and Networks with corresponding simulations , Intersection of Cyber and Artificial Intelligence (impact on Military Networks and Communications) ; Metamorphic AI ; impact of philosophy, literature , history , parapsychology , geography , biology on fast growing AI landscape and relevant domains. And finally tracing the Military origins behind most of the disruptive innovative technologies in an effort to honour such remarkably commendable contributions.
A few thousands of pages of more relevant analysis and documentation needs rendering and therefore much needed attention. All the above is just a succinct synopsis of upcoming work in progress .
USAV 2025 – Global Military Grade Cyber Defence Intel Security & AI Analysis
https://easytech4all.net/2025/03/06/usav-2025/
Integrated All Domain Warfare | Militarised AI and CyberNet |Global Strategic Analysis – Global Military Grade Cyber Defence Intel Security & AI Analysis
https://easytech4all.net/2025/03/21/integrated-all-domain-warfare-militarised-ai-and-cybernet-global-strategic-analysis/
Aggregate Blog Archives Notes Abstracts - Doc 2
https://docs.google.com/document/d/1IOnCFmXsGnKKE0Pi8rR7FyiC7RzmsENzkp2aEfJogMI/mobilebasic
Aggregate Blog Archives Notes Abstracts - Doc 1
https://docs.google.com/document/d/18HihkVZhuMyIl-hzzPTbtAuVn5EeOpVx7RlPcoeSrH0/mobilebasic
USAV 2025 – Global Military Grade Cyber Defence Intel Security & AI Analysis
https://easytech4all.net/2025/03/06/usav-2025/
Integrated All Domain Warfare | Militarised AI and CyberNet |Global Strategic Analysis – Global Military Grade Cyber Defence Intel Security & AI Analysis
https://easytech4all.net/2025/03/21/integrated-all-domain-warfare-militarised-ai-and-cybernet-global-strategic-analysis/
Aggregate Blog Archives Notes Abstracts - Doc 2
https://docs.google.com/document/d/1IOnCFmXsGnKKE0Pi8rR7FyiC7RzmsENzkp2aEfJogMI/mobilebasic
Aggregate Blog Archives Notes Abstracts-Doc 1
https://docs.google.com/document/d/18HihkVZhuMyIl-hzzPTbtAuVn5EeOpVx7RlPcoeSrH0/mobilebasic
Some resources to understand Global defence rapid shapeshifting scenarios from an Indian perspective :
* Centre for Land Warfare Studies (CLAWS): A leading think tank on strategic studies and land warfare in the Indian context. https://www.claws.in/
* Observer Research Foundation (ORF): An independent think tank that publishes research and analysis on a wide range of issues, including defense and security. https://www.orfonline.org/
* The Manohar Parrikar Institute for Defence Studies and Analyses (MP-IDSA): A government-funded think tank that conducts research on defense and security issues. https://idsa.in/
And please do lookup for India's Light Combat Aircrafts , indigenous military drones , evolving stealth latest generation aerial combat fighters.
A BrahMos cruise missile. India.
S400 (Used by India , Qatar , Turkey ) and S500 missile platforms. Origin - Russian.
Some resources to understand the Global defence rapid shapeshifting scenarios from an Indian perspective :
* Centre for Land Warfare Studies (CLAWS): A leading think tank on strategic studies and land warfare in the Indian context. https://www.claws.in/
* Observer Research Foundation (ORF): An independent think tank that publishes research and analysis on a wide range of issues, including defense and security. https://www.orfonline.org/
* The Manohar Parrikar Institute for Defence Studies and Analyses (MP-IDSA): A government-funded think tank that conducts research on defense and security issues. https://idsa.in/
Integrated Multi Domain War and battlefield Scenario Simulation
Integrated Multi Domain War and battlefield scenario simulation based on 27 years of observations , experience , research and analysis . From George Lucas Star Wars , Electronic Arts : Battlefield series | Crysis series | Medal of Honor titles ; Activision , Gray Matter , Treyarch : Call of Duty series . Only Hypothetical Scenario and Static Linear Simulation.
Wild Conjectural Doctrine -
If only kinetic Wars could be fought in the safe precincts of the virtually augmented world of Metaverse integrating the gaming empires of some of the most successful online multiplayer names like Electronic Arts Battlefields and Treyarchs Call of duty etc. without causing loss of precious human lives through unavoidable collateral damage . And if beyond this scope at all , maybe in the arena between Smart Robotics and Advanced uncrewed Autonomous Weapon ecosystems and platforms only.
A Novel on Accelerated Intelligence Surveillance Reconnaissance JADC2
Also because a novel is being written on Accelerated Intelligence, Surveillance, Reconnaissance ; Joint all Domain Command and Control , measuring it's impact on evolving , rapidly transforming Integrated Multi Domain War and battlefield operations .
Dedicated to the warfighters and defenders from US DOD Pentagon with all its allies across the Globe , Military Alliance NATO and as a mark of deep appreciation , for over 27 years now across several continents , with the Raptors - Golden and Sea Eagles , Hawks , Falcons , Harriers and even owls to certain degree. Most Military Defense Analysts have read something similar in the past but a new one is in works and definitely worth waiting for !
Mark of Deep Respect for UN
Also as a mark of deep respect and honour for the World's Greatest institution called the United Nations and it's proactive peace building , peace keeping efforts . It's predecessor, "The League of Nations" collapsed and eventually failed to maintain peace and prevent WW2. Therefore promoting International Cooperation through United Nations (also by strengthening its affiliates) is a natural choice for many countries.
Future Updates and Strategic Analysis
In this regard , all future updates and strategic analysis work will only focus on the influence of real quantifiable human world on Computer and mobile Technology , Advanced Cyber threat Intelligence Systems , Autonomous Cyber Defense Systems , battlefield management Systems and Networks with corresponding simulations , Intersection of Cyber and Artificial Intelligence (impact on Military Networks and Communications) ; Metamorphic AI ; impact of philosophy, literature , history , parapsychology , geography , biology on fast growing AI landscape and relevant domains. And finally tracing the Military origins behind most disruptive innovative technology to honour such commendable contributions.
Recommended Reads
You may look at the Intercontinental Military Defense Industrial Intelligence Landscape through the prism of the following organizations :
STOCKHOLM INTERNATIONAL
PEACE RESEARCH INSTITUTE.
SIPRI is an independent international institute dedicated to research into conflict, armaments, arms control and disarmament. Established in 1966, SIPRI provides data, analysis and recommendations, based on open sources.
United Nations Institute for disarmament research - ()
Bulletin of the Atomic Scientists
- ()
The Cipher Brief - ()
Defense News - ()
Jane's Defence Weekly - ()
C4ISRNET - ()
Breaking Defense - ()
Military Times - ()
Military.com - ()
DefenseScoop - ()
Axios - ()
Modern War Institute - ()
Defense Post - ()
Defense One - ()
War on the rocks - ()
Belfer Center - ()
The RAND Corporation is a nonprofit global policy think tank first formed to offer research and analysis to the United States Armed Forces -
Notes : Global Weapons Ecosystems and Landscape
Brief Succinct notes on the Weapons Ecosystems and Landscape. Only those that fall in the significant broad and major category.
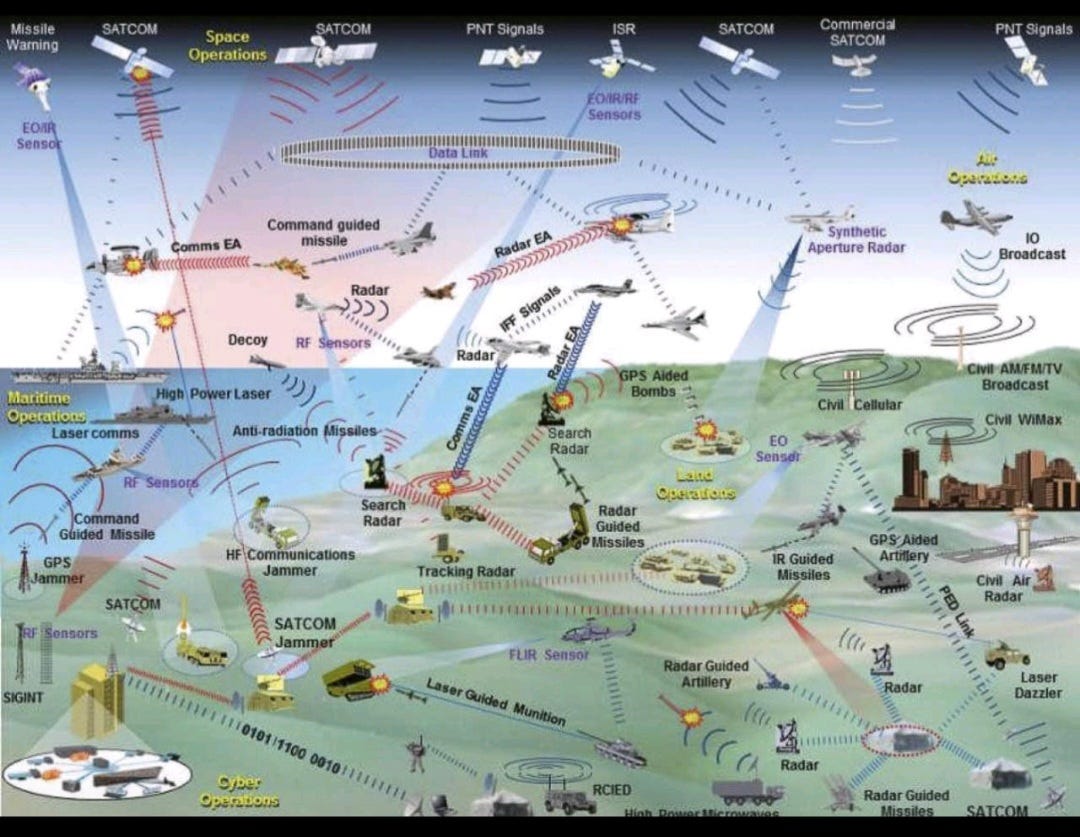
This infographic is a complex military operations diagram illustrating the integration of space, air, land, maritime, and cyber operations in modern warfare. It showcases various elements such as:
1. Space Operations – Satellites providing ISR (Intelligence, Surveillance, and Reconnaissance), SATCOM (Satellite Communications), and PNT (Positioning, Navigation, and Timing) signals.
2. Air Operations – Aircraft using synthetic aperture radar, GPS-aided bombs, infrared-guided missiles, and electronic warfare (EW).
3. Land Operations – Radar-guided artillery, tracking radars, HF communications jammers, and EO (Electro-Optical) sensors.
4. Maritime Operations – Naval assets with laser communications, high-power lasers, anti-radiation missiles, and guided missiles.
5. Cyber Operations – SIGINT (Signals Intelligence), satellite communication jammers, and digital warfare elements.
Modern Network Centric Warfare with Electronic Warfare :
It highlights modern network-centric warfare with electronic warfare (EW), jamming, guided munitions, and multi-domain integration for battlefield dominance.
This image represents modern multi-domain operations (MDO), integrating space, air, land, maritime, and cyber warfare concepts. Below is a detailed breakdown of each component:
1. Space Operations
Satellites provide ISR
(Intelligence, Surveillance, and Reconnaissance), SATCOM (Satellite Communications), and PNT (Positioning, Navigation, and Timing).
Missile Warning Systems
detect and track incoming ballistic or cruise missiles.
Electronic Warfare (EW)
on satellites can jam enemy communications, disrupt GPS, or conduct signals intelligence (SIGINT).
2. Air Operations
ISR Aircraft:
Use Synthetic Aperture Radar (SAR) and infrared sensors to locate and track targets.
Electronic Attack (EA):
Airborne jammers disrupt enemy radars, communications, and missile guidance.
Precision-Guided Munitions (PGMs):
GPS-guided bombs, infrared-guided missiles, and radar-guided missiles are used for high-accuracy strikes.
Electronic Countermeasures (ECM):
Decoys and radar jamming systems mislead enemy air defense.
3. Land Operations
Search and Tracking Radar:
Detects and follows enemy aircraft, missiles, and ground movements.
Radar-Guided Artillery & Missiles:
Utilizes radar for precision targeting.
EO/IR Sensors:
Electro-optical (EO) and infrared (IR) sensors enhance night and low-visibility operations.
Communications Jammers: Disrupt enemy HF (high frequency) radio and SATCOM signals.
4. Maritime Operations
Naval Electronic Warfare:
Ships use electronic attack (EA) to jam enemy radar and communications.
Anti-Radiation Missiles (ARM):
Detect and destroy enemy radars.
Laser Communications & Directed Energy Weapons (DEW):
Used for stealthy, high-speed data transfer and disabling enemy drones/missiles.
Command-Guided Missiles: Controlled remotely via data links.
5. Cyber Operations
SIGINT
(Signals Intelligence): Monitors and exploits enemy communications.
Cyber Warfare:
Digital attacks on networks, satellites, and military infrastructure.
SATCOM & GPS Jamming:
Disrupt enemy positioning and communication.
RCIED (Remotely Controlled Improvised Explosive Devices):
Cyber-enabled IEDs triggered remotely.
Network Centric Warfare for Real Time battlefield Dominance :
This image effectively visualizes how network-centric warfare integrates advanced sensors, jammers, guided weapons, and real-time communication for modern battlefield dominance.
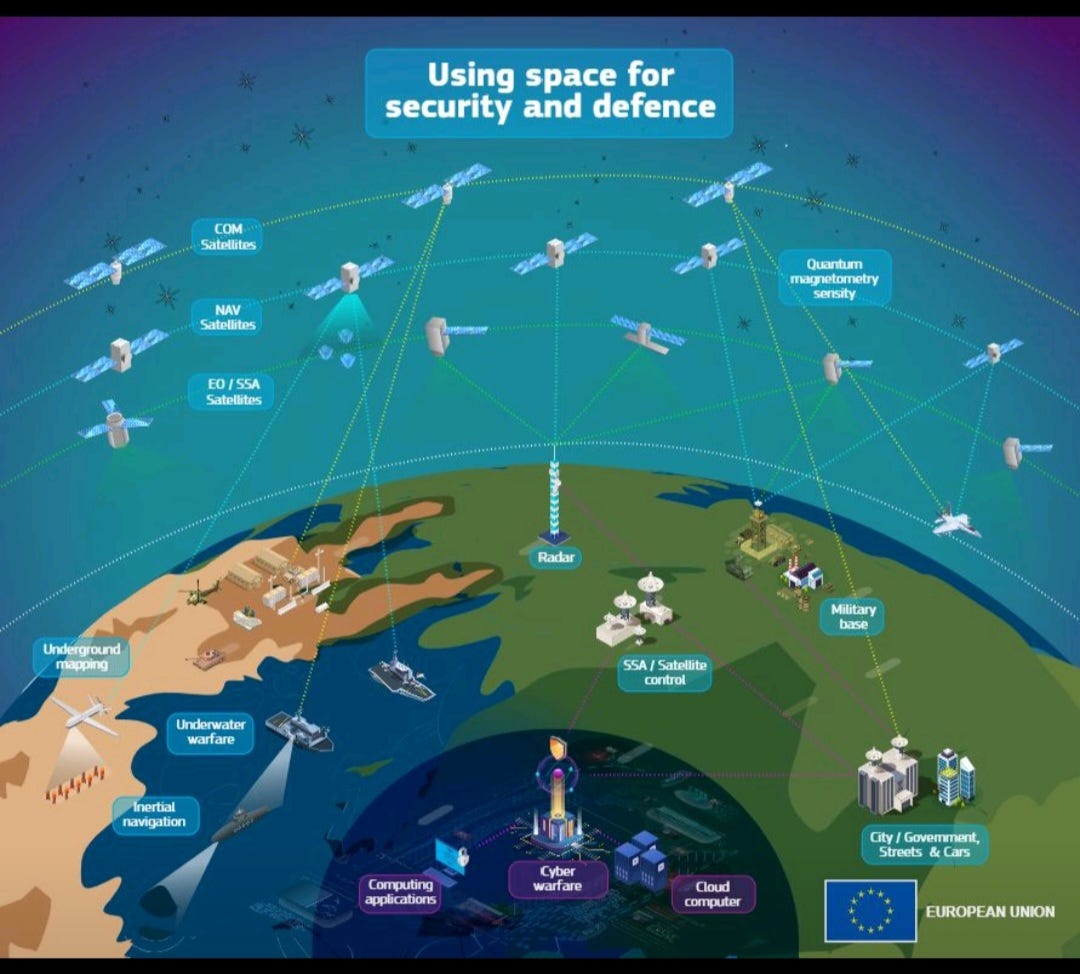
This image illustrates how space-based technologies support security and defense operations across multiple domains, integrating satellites, radar, cyber warfare, and military bases. Here’s a breakdown:
1. Space Operations
COM Satellites: Secure military communications.
NAV Satellites: Provide GPS and positioning for military and civilian applications.
EO/SSA Satellites: Electro-optical (EO) and Space Situational Awareness (SSA) satellites for surveillance and tracking threats.
Quantum Magnetometry Sensors: Detect stealth technology and underground structures.
2. Air & Land Defense
Radar Systems: Detect aerial and missile threats.
Military Bases: Central command for defense operations.
City & Infrastructure Security: Space surveillance helps protect urban areas.
3. Maritime & Underwater Warfare
Underwater Mapping & Warfare: Uses satellites and naval assets to track submarines.
Inertial Navigation: Allows precise movement without relying on GPS.
4. Cyber Warfare & Digital Defense
Cyber Warfare: Protects military networks from cyber threats.
Cloud Computing: Secure data processing for defense operations.
This image, created under the European Union’s defense framework, highlights the multi-domain integration of space, cyber, air, land, and maritime operations for modern security.
Fighter Aircraft. Sixth Generation Global Combat Air Program
Global Combat Air Programme - Sixth generation stealth fighter jet platform as a replacement for Eurofighter Typhoon. Joint development by UK , Japan , Italy. USA may join and also Kingdom of Saudi Arabia. Timeline : 2025 - 2035
General Dynamics F-16 Fighting Falcon.
[one-engine multirole combat aircraft. It was originally designed and built by General Dynamics, which is now part of Lockheed Martin. The United States Air Force (USAF). Speed - MACH 2 ].
The speed of sound is also known as Mach 1. Things that go faster are supersonic, and things that go five times that speed (Mach 5) are hypersonic.
McDonnell Douglas F-15 Eagle.
[The F-15 Eagle is a fighter jet that originally made by McDonnell-Douglas (later Boeing). It is known around the world for its toughness and undefeated record, meaning that it has never been shot down by an enemy plane. It is used primarily by the United States Air Force, but it is also used in Israel, Japan, Saudi Arabia and South Korea].
The McDonnell Douglas F-15E Strike Eagle is a modernized variant of the F-15 Eagle. It was optimized as an attack aircraft for the US Air Force with a stronger airframe than earlier versions. It has longer range, more powerful radar, and a second seat for the operator of the strike aircraft equipment. Foreign operators are Israel, Saudi Arabia, Singapore, and South Korea.
F-15EX, is mandated to enter service in the Summer of 2024 with mainly better equipment for electronic warfare.
The Lockheed Martin F-35 Lightning II
is a family of single-seat, single-engine, fifth generation multirole Fighter aircraft. It can perform ground attack, reconnaissance, and air defense missions with stealth capability.
The F-35A Lightning-II fighter plane achieved technical certification to carry the B61–12 guided nuclear gravity bomb, clearing the way for US Air Force units in Europe to complete their nuclear surety certifications before ultimately receiving the new bombs. 5th Gen.
French Aviations Dassault Rafale
is a fighter aircraft made by French airplane company Dassault Aviation. 4.5 gen.
Beyond visual range Magic, Meteor, and Mica air-to-air missiles.
SPECTRA electronic warfare. It uses the communication Link 16 like as the majority of NATO combat aircraft.
Aerial reconnaissance. ASMP nuclear missile.
Exocet anti-ship missile. Operated by NATO countries and allies like Qatar . Also Indian Air Force.
M61 Vulcan is a hydraulic and pneumatic autocannon. It has six barrels. It is cooled by air and fires by the power of electricity. It is a Gatling-style rotary cannon. The size of its caliber is 20 mm. It has a very high rate of fire.
McDonnell Douglas F/A-18 Hornet
The F/A-18 Hornet (CF-18, F-18) is a fighter jet that is made by Boeing, and was originally manufactured by the McDonnell-Douglas Company. It can take off from aircraft carriers because of its special design. The F/A-18 can attack land and air targets. Any aircraft which can do this is called "multi-role". The Hornet is also flown by the Blue Angels.
B81 and B83 nuclear bombs
Aim-9 Sidewinder and Taurus Cruise Missile.
The Eurofighter Typhoon
is a jet fighter aircraft made by EADS, BAE Systems and Alenia Aeronautica with Eurofighter GmbH. It first flew in 1994 and was introduced in 2003. It uses canards and a delta wing which makes it agile and quick. It is called the "Eurofighter" because it was made by European countries, Italy, the United Kingdom, Germany, and Spain.
A German Typhoon.
The countries that designed the Typhoon use it. Austria, Oman, Qatar, Kuwait and Saudi Arabia have also ordered it.
The A-10 Thunderbolt II
(also called the Warthog) is an attack aircraft made by Fairchild Republic.
It is designed to drop bombs, fire rockets, missiles, and its 30mm Gatling gun at enemies on the ground (such as tanks) with about 3500 rounds. It is named after the World War II P-47 Thunderbolt. Although not as fast as most military jets, it is tough, heavily armored, and can turn well. The A-10 is also used as a CAS (close air support) aircraft, which involves flying slowly over a battlefield and destroying enemy targets.
Because the Avenger fires such big bullets (exploding artillery shells 3cm wide) at such a high rate of fire (up to 40 every second) many believe it can destroy any target very easily, even tanks with thick armor such as the M1 Abrams. However, while the bullet can go through thin metal on a car or truck, it cannot penetrate the thick metal walls of a tank. It can only destroy them because most tanks have thinner metal on the top to make them lighter. If an A-10 hits this thinner armor, then destruction is more likely, but if it hits the front or sides where the armor is thicker, then the tank crew and systems will survive.
BRRRRRRRT" is jargon used by airmen to describe the sound of the gun of the a-10 firing. It is joked by airmen that the a-10 dispenses freedom at 3900 rounds per minute (a reference to the a-10's firerate and association with American interventionism).
The B-52 Stratofortress
is a bomber which, with in-air refueling, can fly long distances to reach targets anywhere in the world. The B-52 can carry up to 70000 lbs of bombs and weapons in its large bomb bays, long distance strategic bomber.
The Northrop Grumman B-2 Spirit,
also called the Stealth Bomber, is an American strategic bomber. It has a lot of stealth technology, and it is designed to get through many anti-aircraft defenses. It can drop both conventional and nuclear weapons. Two people fly the bomber, and it can drop up to 80 500 lb (230 kg)-class JDAM GPS-guided bombs.
The B-21 Raider
is an American strategic bomber. It is being developed by Northop Grumman for the United States Air Force. It is first 6th generation jet aircraft. The airplane is best known for being very stealthy. It is very hard to see on radar. The plane is intended to replace the B-2 Spirit and B-1 Lancer by 2040.
The Rockwell B-1 Lancer
is a strategic bomber in the service of the US Air Force. It is a four-turbojet aircraft that uses a variable-sweep wing. It can carry nuclear weapons or classic bombs. It is only used by the USA.
Attack helicopters can use a lot of weapons. Some of these weapons include machine guns, bombs, autocannons, missiles, and rockets. Some attack helicopters can also use air-to-air missiles for protection against other helicopters and planes. Apache and Comache Attack helicopters
Battle Tanks.
The M1A1 and M1A2 Abrams is a modern main battle tank used by the United States.
German Leopard tanks. M10.
But are Military drones proving to be the ultimate nemesis of modern day battle tanks ?
Bradley fighting Vehicle - M2 and M3 by BAE Systems.
Hummer
used to be made by General Motors.
The design of the Hummer H1 is based on the military High Mobility Multipurpose Wheeled Vehicle (HMMWV – Humvee). Civilian version.
The High Mobility Multipurpose Wheeled Vehicle (HMMWV; colloquial: Humvee)
is an American military SUV produced by AM General. The Hummer is a civilian version of the Humvee. Armored Personnel carriers Strykers etc.
Infantry Combat.
MANPAD -
Man portable surface to air missile.
TOW missiles - Destroy lightly armored vehicles.
Stinger
A portable low altitude surface-to-air missile system using infrared guidance and an impact fuse; fired from the shoulder
Panzer - armored Vehicle or tank.
A Panzerfaust
is a recoilless rifle that was invented by Germany.They were less powerful than later Rocket-propelled grenades.
A rocket-propelled grenade
or an RPG is the name for any kind of weapon, held on the shoulder that fires rockets that have an explosive warhead. These warheads are attached to a rocket motor and the rocket has fins which help it to fly straight
RPGs with High explosive anti-tank warheads are very effective against armored vehicles such as armored personnel carriers (APCs).
A Bazooka
is a very powerful weapon that shoots a rocket. It is a small and easily carried and sits on the shoulder to fire.
The M72 Light Anti-Armor Weapon (LAW)
is a small, lightweight rocket launcher used by the US military and other NATO countries. UK - NLAW.
But the LAW was still useful for destroying bunkers and trenches.
US Army Javelin missiles. Anti tank missiles.
Handguns And Rifles.
A 9×19mm Parabellum is a nine millimeter wide bullet. It is usually used in handguns or submachine guns. The nine millimeter is often referred to as a "nine", "9mm", or "9×19".
The Uzi, the MP5, the Beretta 92, and the Glock 18. It is the standard handgun bullet for all NATO countries.
The 9mm caliber Beretta M9, a military version of the Beretta 92.
The Beretta 93R (the R means "raffica", burst in italian) is an Italian 9mm caliber pistol manufactured by Beretta, which allows firing both in semi-automatic mode (one shot each time the trigger is pulled) and three-shot bursts (three shots each time the trigger is pulled). This pistol is based on the Beretta 92 semi-automatic.
The Glock pistol is a series of polymer-framed semi-automatic pistols. They are designed and produced by Glock Ges.m.b.H. in Deutsch-Wagram, Austria. It entered Austrian Armed Forces and police service by 1982.Different models use different ammunition.
There was resistance from the market to accept a "plastic gun", but this was overcome. Glock pistols have become the company's most profitable line of products, with 65% of the market share of handguns for United States law enforcement agencies.They also supply many national armed forces and security agencies around the world. Glocks are also popular firearms amongst civilians in the U.S., for recreational and competition shooting, and for home or self defense.
The M1911 is a .45 ACP caliber pistol originally made by Colt, and is now the most copied pistol design in the world. It was designed in the early 1900s by John Browning
The M240 machine gun is a type of machine gun. It fires the 7.62mm NATO cartridge. It is gas-operated and the bullets are fed into the chamber by a belt. The M240 has been used by the United States Armed Forces since the late-1970s. It is used a lot by infantry. The M240 is also mounted onto ground vehicles, boats, and helicopters.
An AR-15 style rifle is any light semi-automatic rifle inspired by the Colt AR-15 design
The M16 is an assault rifle used by the United States since the Vietnam War in 1963,based on the AR-15.
AK 47 and AK 74 Mikhail Kalashnikov's Automatic Rifle.
Russian Druganov sniper rifle.
Sako trg 42 sniper rifle.
Almost all sniper rifles use a sniper scope, a special telescope that allows them to see targets very far away.
And SLR - Self Loading Rifles.
The Heckler & Koch G3 is a battle rifle developed by Heckler & Koch and the Spanish state-owned design and development agency CETME. It has a 20 rounds magazine, that holds 7.62mm NATO ammunition. Origin - germany
The Bundeswehr (German for "Federal Defence Force"; audio speaker iconlisten ) are the German Armed Forces.
The Heckler & Koch G36 is an assault rifle designed in the 1990s by Heckler & Koch (H&K) in Germany. The weapon is gas operated and has a standard magazine that holds 30 of the 5.56mm NATO rounds. It can also be used with a 100-round 'drum'. The G36 has a 3x scope and often a red dot sight, too in the carrying handle. The G36 is the main weapon of many special units and the army of Portugal, Spain and Germany (Bundeswehr).
The 5.56×45mm NATO round, pronounced "five-five-six", is an intermediate cartridge and the main bullet type used by guns made for NATO militaries.
The XM8 is a rifle made by Heckler & Koch. It is an automatic rifle that uses the 5.56 mm NATO caliber ammunition. The XM8 holds 30 rounds of ammunition. The US Army was interested in the XM8 because it is a very light weapon. It weighs only 2.66 kilograms (5.9 lb). The US Army tested ten weapons in a 60,000 round dust test and the XM8 was the best. This showed that the XM8 is much more reliable than the M4.
Tracer rounds during night.
Binoculars are a kind of tool that lets people see far-away things more clearly. The technology is called optics. Binoculars are made of a pair of matched telescopes which are held in front of the user's eyes.
Guerrilla warfare
is a war tactic in which small groups of people (Spanish: guerrilleros) fight against an organized army. Guerrilla warfare is sometimes practiced in places in which a regular army would have difficulty, such as forests and mountains. Usually, the army is invading a territory. In open fields, the organized army, which is better armed and larger, has the advantage. However, in forests and mountains, the guerillas can gain an advantage over larger and better-armed armies.
DRONES.
Drones have on-board computes and augment their data processing speed using edge computing. Which accelerates it's reconnaissance and surveillance capability.
The switchblade drone, a small drone that can be launched from a hand-held tube. It has a high-resolution camera. It can be used for reconnaissance and surveillance missions.
Phoenix Ghost, a kind of drone that can blow up (or explosive drone) or loitering munition.
Loitering munitions are able to wait over an area before they hit their target. Also known as Kamikaze drones.
Loitering weapons are different from cruise missiles because they do not wait / loiter over the target area. They are different from unmanned combat aerial vehicles in that a loitering weapon is intended to be used in attack and has built in warhead. Much similar to a drone but with some properties of a missile. In this type of weapon , munition waits until it detects a target . Sometimes it waits until it is given a Command to attack. Loitering weapons allow selecting targets more precisely. They have been developed for extra roles such as large ones for relatively long range strikes and fire support and tactical very short range battlefield systems that fit in a backpack. From first generation loitering munition IAI harpy to Uvisions Air limited loitering munition HERO.
Uncrewed Unmanned Aerial Vehicles / Unmanned Uncrewed Ground Vehicles / LAWS - Lethal Autonomous Weapon Systems.
Predator drones. USAF.
Global Hawk .
Look for Kratos Defense and Avionics.
Some weapons are able to wait over an area before they hit their target. They are called loitering weapons. Other names include loitering munition, suicide drone or kamikaze drone.
But are Military drone manufacturers focusing on stealth tech and electronic attack / laser (direct energy weapons) countermeasures ? The not so shy Shylock has locked it's electronic magnetic attack on most operational drones.
Turkish Bayraktar. Operational UAVs.
Commercial DJI drones. Quadcopter.
A helicopter (esp. a drone) propelled by four rotors.
Nano drones.
Missiles
In military terminology, a missile is a guided airborne ranged weapon capable of self-propelled flight. In general, a missile may refer to anything thrown or launched object at a target like a javelin or darts. Nowadays, it means, mostly, a self-propelled guided weapon system. Missiles are used in war to destroy military targets.
Missiles can carry explosives or other destructive loads. The loads a missile may carry are called a "payload". It is not always harmful to people.
For example, cruise missiles have carried "graphite bombs" to destroy electrical power systems without much collateral damage. Missiles are also one of the causes of explosions.
Types of missiles
The two main kinds of missiles are simple "rockets" and "guided missiles". A rocket is no longer controlled once it has been launched. Most guided missile are also propelled by a rocket engine but can be controlled after it has been launched. Some missiles used in anti-aircraft warfare, such as the AIM-9 Sidewinder, guide themselves with temperature. Others guide themselves by radar or are under radio control.
Cruise missiles
are big missiles that carry large payloads to hit ground targets or to badly damage/sink ships. Ballistic missiles look similar, but they keep the engine off and don't stay at a lower height to be more accurate like cruise missiles do. Instead, they go high up to the edge of space and turn off the engine. Since there's no air friction in space, they don't need the engine on to continue moving forward at the same speed. They then crash into the target from the sky. In short, cruise missiles have an engine always running and fly low through the atmosphere to get to a target. Ballistic missiles go to the edge of space and turn off their engine to fall to a target. You could say cruise missiles fly while ballistic missiles fall.
An anti-aircraft missile
is another name for a surface-to-air missile, also said SAM for short. NASAMS .
Surface to air missile (SAM) also known as ground to air missile (GTAM) or surface to air guided weapon is a type of mussile that is launched from ground or from ship to destroy aircraft or other missiles. It is a type of anti aircraft warfare.
Anti aircraft warfare or air Defence is any way of fighting military Aircrafts in combat from the ground.
Anti aircraft guns (AAA) is anti aircraft artillery and flak or flack . It is derived from German flugabwehrkanone air Defence cannon.
Tomahawk cruise missiles.
Multibarell rocket launchers. Pinaka rocket systems. Thermobarbic etc.
MIRV - Multiple Intermediate reentry Vehicle.
Episci and Raytheon via Sentinel Satellites will be tracking and mapping Hypersonics at Mach 5 . But the Meteoroids once inside earth's atmosphere are racing at Mach 40. That's even faster than the Earth's escape velocity at 13km/sec. They normally disintegrate and glow by virtue of heat generated by friction.
Hypersonic thermonuclear bombardment systems .
Hypersonic Glide Vehicle.
Minuteman III Intercontinental Ballistic Missile . Polaris and Titan advanced systems. Strategic forces and Strategic Command.
Dark Eagle
US Army - Long Range Hypersonic Weapon - US Dark Eagle on Transporter erector Launcher. Advanced hypersonic weapons program.
Intermediate Range surface to surface boost Glide hypersonic weapon. US Navy - Intermediate Range Conventional Prompt Strike program. Also
Look for Zumwalt Class destroyers , Block V Virginia-class sumbarines, Ohio class ballistic missile submarines
Hypersonic attack cruise missile.
Prompt Global Strike / Conventional Prompt Strike.
Nuclear Weapons .
There are two types of nuclear weapons: fission weapons (also called atomic bombs or A-Bombs) and fusion weapons (also called hydrogen bombs, H-Bombs, or thermonuclear weapons).
They make energy for the nuclear explosion in different ways. Fusion weapons make bigger explosions. Fission weapons use a special isotope of uranium or plutonium. Fusion weapons use a special isotope of hydrogen.
Nuclear Explosions - Trinity , Fat Man , Little boy , hurricane , ivy Mike , ivy king , Russian TSAR .
The United States appears to be in compliance with the New Strategic Arms Reduction Treaty (New START) limits. Although Russia “suspended” its participation in New START in February.
The Nuclear Non-Proliferation Treaty (or NNPT) is a treaty that was made to stop nuclear weapons from being built.
Nuclear Fallout
is the left over radiation hazard from a nuclear explosion. The name is because radioactive material "falls out" of the atmosphere into which it is spread during the explosion. These materials continue to undergo radioactive decay for minutes, days or centuries. "Fallout" commonly refers to the radioactive dust created when a nuclear weapon explodes. All nuclear explosions make fission products, which are the broken, radioactive atoms from a fission reaction. Neutrons from the explosion also make some nearby materials radioactive.
Nuclear winter
is a theory stating the possible effects of the use of nuclear weapons during a nuclear war; which could include reduced sunlight, extreme cold, and the presence of large amounts of smoke and soot in the Earth's atmosphere.
People - Robert Oppenheimer, Albert Einstein etc .
US Proud Prophet Nuclear War Games.
Nuclear power is the controlled use of nuclear energy. Nuclear energy can be released by nuclear reactions in a machine called a nuclear reactor. This energy boils water for a steam engine to make electricity, which then can be used to power machines and homes. In 2023, 10% of the world's electricity came from nuclear power. Nuclear power plants also make radioactive waste that could be harmful if it is not stored properly.
Nuclear reactors also power some large military ships (aircraft carriers) and submarines. So, aircraft carriers are basically small, floating, mobile airports.
Aircraft carriers
are warships that carry airplanes and other aircraft like helicopters/gunships. They are used by navies to allow Aircrafts to fight along naval warships. They are usually very large carrying hundreds or thousands of sailors and many combat Aircrafts. The British Harrier can take off vertically. Also known as vertical short takeoff and landing. Harriers can take off and land straight up and down in short distance of the flight deck. The Lockheed Martin F-35 Lightning 2 can perform ground attack , reconnaissance and air defense missions with stealth capability.
Because they are big ships and need much electric power, big modern aircraft carriers are steamships. Some have on-board nuclear power plants.Others burn fuel oil.
A carrier battle group (CVBG)
is a naval fleet that includes an aircraft carrier and a group of other ships that work together to help the carrier complete its mission. The CV in CVBG is the United States Navy classification code for an aircraft carrier.
The USS Abraham Lincoln (CVN-72) is an aircraft carrier in the United States Navy. It is the second ship to have the name Abraham Lincoln. It is also the fifth ship in the Nimitz class line of aircraft carriers.
US Seventh Fleet.
Aircraft carriers are often protected by smaller ships, called cruisers or destroyers. Armored Speed Boats and Autonomous Unmanned overwater military drones and underwater drones pose a threat to aircraft carriers. So do high number of armored armed speed boats.
The torpedo,
is an explosive projectile weapon that moves by itself (using a propeller), launched above or below the water surface, that goes underwater toward a target, and made to explode when it hits a target or is near to it. Torpedoes may be launched from submarines, surface ships, helicopters, aircraft, land etc.
A Destroyer
is a fast , small and maneuverable warship . They escort larger warships. They have been used in the past to defend against torpedo boats. Most naval warships are destroyers. They use cruise missiles , automated turrets , and torpedoes. Some can launch nuclear missiles. They support Carrier battle groups and amphibious landings.
A cruiser
is a warship larger than a destroyer. They are mostly used as Command ships but it is hard to give them a specific role. Since most ships nowadays apart from aircraft carriers and amphibious assault ships have similar roles and sizes. Some of the cruisers role include launching many kinds of missiles , standoff , communications and Command, bombardment escorting other ships and special operations .
Many modern ships also do this with the main difference being size , firepower and their intended use.
People have also been studying since the middle of the 20th century to use fusion power which produces much more energy and does not produce radioactive waste. Nuclear fusion reactors do not exist yet and are still being developed.
Electronic warfare
is all military techniques for aerial reconnaissance, spying, and radar jamming. In electronic warfare, missiles like AGM-45 Shrike or AGM-88 Harm can be used to destroy radar or communication systems. Examples include deciphering encrypted messages, such as the messages decoded due to the British reverse engineering of the German Enigma.
A war of attrition
is a military strategy in which one side tries to cause the other to lose so many soldiers and to have so much military equipment destroyed that the enemy forces are worn down until they collapse.The side that has more resources (soldiers and military equipment) usually wins.
The military–industrial complex
refers to the relationship between the government, the military, and the businesses that make things for the military. For example, the businesses can give money to politicians in elections. Then, politicians give more money to the military. Then, the military buys things from the businesses. Each group gains something, so they try to keep doing the same thing.
The term was invented in the United States. However, most countries have politicians and soldiers and people who make weapons and other military supplies; thus they have a military-industrial complex.
Blitzkrieg
is a German word that means "lightning war" and refers to the high speed of a lightning bolt.
In blitzkrieg, the attacking motorized infantry armies move quickly and are helped by tanks and aircraft. Slower-moving enemy units are overrun or surrounded and often captured with little fighting. The slower units often become disorganized and are not ready to fight when they are captured.
The combined arms tactics of blitzkrieg were developed in the 1920s and 1930s, especially in the German Wehrmacht. They seldom used this word, however.
A scorched-earth policy
policy is a military strategy. The goal is to destroy anything that might be useful to the enemy while the enemy is going through or running away from a place. Any useful things that could be used by the enemy may be targeted, for example food sources, water supplies, transportation, communications, industrial resources, and even the local people themselves.
Joint All domain Command and Control.
ISR - Intelligence Surveillance Reconnaissance
Integrated Operations.
Multi domain Battlefield operations.
Land Air Sea (Marine ) Space Cyberspace
"NATO Code Names for Submarines and Ships: Submarine Classes / Reporting Name".
Incendiary devices
or incendiary bombs are bombs. These bombs have been designed to start a fire. Sometimes they are also called firebombs.
A thermobaric weapon, aerosol bomb, fuel air explosive, or vacuum bomb is a type
of explosive that uses oxygen from the surrounding air to create a high-temperature explosion.
This can be launched as a rocket or dropped from an airplane as a bomb.
An improvised explosive device (IED),
more commonly known as roadside bomb, is a bomb that is constructed by people for other purposes than military action. Paramilitary groups often use such devices for terrorist activities. Unconventional warfare which is done by guerilla forces also uses such devices. Improvised explosive devices are commonly made out of household materials such as fertilizer (that use ammonium nitrate), matches (that use potassium chlorate), and hydrogen peroxide.A simple switch or button which lights the explosive material on fire (with some sort of flammable fuel like gasoline or diesel) is added to some IEDs.Other IEDs use cell phones, garage door openers, or toy controllers are also used to blow up the explosive in some cases.
Phosphorus bombs.
Now, consider the emergence and maturation of unmanned surface vehicles like DARPA’s Sea Hunter and unmanned undersea vehicles like Boeing’s Orca. These long-endurance, uncrewed platforms—cheap enough to be procured in large numbers—can supplement the Navy’s existing fleet of Los Angeles, Seawolf, and Virginia-class attack submarines.
Experts are concerned that LIDAR, hydrodynamic pressure wave detection (or wake disturbance tracking), hyperspectral electro-optical and infrared imaging, and magnetic anomaly detection—augmented by AI-enhanced data processing and eventually quantum computing—might cumulatively and fatally undermine the survivability of nuclear ballistic missile submarines. These sensing technologies—redundant and distributed across numerous underwater, surface, and airborne assets—are making the oceans more transparent. The declining survivability of submarines is not a foregone conclusion, but the technological trends are readily apparent, and any such strategic shift will undoubtedly be felt asymmetrically.
The Sentinel intercontinental ballistic missile,
Columbia-class SSBN, B-21 Raider stealth bomber, and Long-Range Stand-Off cruise missile each represent replacements of existing capabilities—and yet analysts can’t agree on whether these procurement programs indicate ambitious or cautious postures. In part, this is because such assessments are informed and swayed by pre-existing assumptions and preferences—for example, whether one subscribes to the nuclear revolution or nuclear superiority schools of thought, or neither.
IRBM - Intermediate Range Ballistic Missile.
MRBM - Medium Range Ballistic Missile.
ICBM - Intercontinental Ballistic Missile.
The emergence of hypersonic boost-glide vehicles
has complicated nuclear strategy (though nobody can agree how), some tests have reopened a decades-old debate about so-called fractional orbital bombardment systems in which nuclear weapons would be launched into space and then deorbited above their targets. Meanwhile, ballistic missile defense—famously divisive and responsible for countless arguments among defense experts—continues to evolve, with the US Navy’s SM-3 Block IIA interceptor conducting increasingly impressive tests. Regarding the difficult task of hunting land-based road-mobile nuclear missiles, there’s an ongoing and decidedly inconclusive debate about whether advances in synthetic aperture radar can solve this problem.
Also Father/Mother of all Bombs. Conventional Warheads.
AI GOES NUCLEAR
The sudden interest in nuclear energy is largely due to AI, which is rapidly transforming the tech industry. Electric utilities are forecasting the nation will need the equivalent of 34 new, full-size nuclear power plants over the next five years to meet power requirements that are rising sharply after several decades of falling or flat demand.
Microsoft, Amazon, and other tech giants are not interested only in reviving existing nuclear plants. They are also funding the development of next-generation nuclear reactors. On October 14, Google announced a deal to purchase nuclear energy from small modular reactors (SMRs) that will be developed by Kairos Power. Two days after Google’s announcement, Amazon said it had signed agreements to invest in four SMRs to be constructed, owned, and operated by Energy Northwest, a consortium of public utilities in Washington state. Amazon hopes the new reactors can power a cluster of energy-gobbling data centers in eastern Oregon. And Oracle is designing an AI data center to be powered by three SMRs, an announcement that Oracle chairman Larry Ellison characterized as seemingly “bizarre” but necessary to meet AI’s “crazy” energy demands.
The first of these next-generation reactors are expected to become operational in the early 2030s, but only three SMRs have been built to date, none of them in the United States.
AI powered
Tech companies talk about “AI-powered” products as if AI itself isn’t powered by something else, but AI consumes electricity in multiple ways. First, there’s the training required to create AI models such as ChatGPT. Training starts with “scraping” vast amounts of text, images, video, and other data from the internet—essentially taking a gargantuan snapshot of online books, news articles, encyclopedias, patents, photos, and other information found on millions of websites. And because scraping captures only one moment in time, it must be done repeatedly. The article you are reading will likely be scraped by AI.
AI models
Developers feed this mountain of raw material to AI models, and they digest it by analyzing patterns in the data—what word tends to follow a series of other words, for example—and using that analysis to form “intelligent” responses to prompts. The models are graded on how well they mimic human-created content (regardless of its accuracy) and then tested repeatedly to fine-tune the answers.
Training AI models
Training is an energy-intensive process. The data sets used for training have grown dramatically over the past few years, and the largest AI models are now trained using hundreds of billions of words, which can take months of processing by tens of thousands of specialized computer chips working day and night.
An analysis done by OpenAI in 2018 found that the amount of “compute” required to train the largest AI models was doubling every three to four months. An analysis of more recent models reports that the training requirements multiplied by four to five times annually during the past four years.
AI electricity consumption
Electricity is also required to process AI queries. A ChatGPT-powered Google query, for example, uses almost 10 times as much energy as a traditional Google search, according to the Electric Power Research Institute. ChatGPT alone responds to approximately 200 million requests per day.
A recent paper by Sasha Luccioni, a researcher at the AI firm Hugging Face, and two co-authors estimates that generating a single AI image can use almost as much energy as fully charging your smartphone.
Quantifying Compute
Quantifying the “compute” used by a particular AI model is easier than estimating the energy used to make the hardware, software, and infrastructure for data centers—and to keep them cool. It's even more difficult to estimate the broader energy impacts of a technology that is already reshaping the labor forces and consumer behaviors of modern societies—for example, using digital devices to perform tasks previously done by hand.
World Energy production
Based solely on current trends, power consumption at US data centers is projected to grow by about 10 percent annually between now and 2030. By one estimate, the exponential growth of AI could consume nearly all the world’s energy production by 2050.
The AI boom
is heavily dependent on power-hungry graphics processing units, or GPUs—specialized computer chips that can process enormous amounts of data. These chips are in short supply, and a multinational corporation called Nvidia commands almost 90 percent of the market. Nvidia, which is based in Delaware but sells chips manufactured in Taiwan and Mexico, recently surpassed Apple and Microsoft to become the world’s most valuable corporation. It is valued at $3.43 trillion, up from $1 trillion only a year ago.
Nvidia Blackwell
Nvidia’s most advanced platform, which is called Blackwell and is used to train AI models, is a cluster of eight GPUs that together consume 15 kilowatts of power—about half of what a typical US household uses. The entire supply for the next 12 months is already sold out. Demand for it is “insane,” the company’s CEO Jensen Huang said in an interview with CNBC in October.
The financial services company Morgan Stanley estimates that Nvidia will produce 450,000 Blackwells during just the fourth quarter of this year and sell them for about $22,000 each. That would amount to almost $10 billion in revenue, and Blackwell is just one of the GPU models sold by Nvidia. Tech writer John Loeffler calls Blackwell “nothing short of a doomsday device,” because he fears there will not be enough carbon-free energy to power the millions of these devices that are being produced.
And Nvidia will soon have competition. The giant tech companies are working to build AI chips of their own. OpenAI CEO Sam Altman traveled to the Mideast a year ago to solicit between $5 trillion and $7 trillion from investors, including the United Arab Emirates, for a chip-building venture known as Tigris, the Wall Street Journal reported, although that project currently appears to be stalled. Saudi Arabia recently launched a $100 billion fund to invest in AI, and China is challenging US dominance with its Qwen AI system.
Is this the “nuclear renaissance”?
As AI’s energy demands grow more intense, and it becomes increasingly clear that the expansion of wind and solar power cannot keep pace, tech leaders have set their sights on nuclear energy.
Proponents of nuclear power have been predicting a “nuclear renaissance” for nearly a quarter-century. But nuclear has never been cost-competitive with other energy sources, and that is unlikely to change anytime soon.
Microsoft and Google Nuclear Bet
Microsoft and Google are also placing bets on nuclear. Earlier this year, Microsoft hired a director of nuclear technologies and a director of nuclear development acceleration to lead the company’s strategy for powering AI advances with small, onsite nuclear reactors—as well as buying energy from larger conventional reactors such as Three Mile Island. Microsoft, which has invested $13 billion in OpenAI and owns almost half of its equity, plans to use AI to expedite the process of getting nuclear plants approved and has been training an AI model on regulatory and licensing documents.
The Pentagon’s outreach arm to Silicon Valley, the Defense Innovation Unit, has selected San Francisco-based Scale AI to lead what it calls Thunderforge, a prototype project to build AI to speed up large-scale military planning, the company and DIU announced this morning.
Scale AI will work with fellow defense tech upstart Anduril, IT giant Microsoft, and other as-yet undisclosed “global” subcontractors, the company and DIU said. The new AI toolkit will combine Anduril’s Lattice data-sharing system with Large Language Models (LLMs) developed by both Microsoft and Scale AI itself.
Some definitions
LASER
An acronym for light amplification by stimulated emission of radiation; an optical device that produces an intense monochromatic beam of coherent light
= optical maser
Direct Energy Weapons and High Energy high speed Kinetic Rail Gun Projectiles launched from Battleships.
microwave radar :
Measuring instrument in which the echo of a pulse of microwave radiation is used to detect and locate distant objects
= radar, radio detection and ranging, radiolocation
LIDAR.
A measuring system that detects and locates objects on the same principle as radar but uses light from a laser; a potential technology for detecting air turbulence that can affect aircraft
Waiting for Crysis type nano suits and Call of duty Advanced warfare level exoskeleton ( Some prototypes have started hitting the shelves at Global Weapons Expo's).
Research on Cyber AI AWS
CyberAI resource Document
https://drive.google.com/file/d/1NNhkOp0E627g7O0SMzrzOriT6ur87ZYA/view?usp=drivesdk
Cyber consecrated presentation
https://drive.google.com/file/d/1BWJXNvWsX0YUHXC1jGozQRCkuz7x9dBS/view?usp=drivesdk
Cyber AGI Science Document
https://drive.google.com/file/d/1YyBovajlUfnPhqyk03pTJtUAx-GcOPWM/view?usp=drivesdk
Easytech4all Cyber Threat Intelligence YouTube Playlist
https://youtube.com/playlist?list=PLf-aX7Sa0eCRYUADIqTAU2qH-lKcNB-wj&si=XSOj8s2ZW12uLPmk
Easytech4all YouTube research playlist on Cyber and AI
https://youtube.com/playlist?list=PLAOUl2tBZpjS66nVEsFNozW8hfku73xSZ&si=9xx63uw1iJiS-tEp
Easytech4all YouTube research playlist on Cyber Intelligence Security and Countermeasures
https://youtube.com/playlist?list=PLAOUl2tBZpjR2u2PaRnd6sE0EJSneu_4v&si=TsJX5kiWcdoMbV5E
Easytech4all YouTube Research Playlist on Autonomous weapons systems and platforms - UAVs UGVs
https://youtube.com/playlist?list=PLAOUl2tBZpjRCYH8AmTUwNt1z4hTH08QX&si=aWzgX2rq2Zg82ByU
Super Soldier Program
https://youtube.com/playlist?list=PLAOUl2tBZpjR7ZjkkiT04QaLmQ9ooE-W6&si=jSo82r28JzpnlalG
1000+ Slide Cyber AI Intelligence presentation
https://drive.google.com/file/d/1t8Lxpzc2N510HqaHgam4iZJmRtG5Dj9J/view?usp=drivesdk
Advanced Cyber Threat Intelligence Landscape and Updates via Digital Magazine by 1PowerCyber for Easytech4all.net
https://bit.ly/3P8gCTT
Advanced Cyber Threat Intelligence Research Analysis Assessment and Projections . YouTube Video Playlist .
https://bit.ly/3yqDEje
Advanced Cyber Defense Threat Intelligence Blog in Progress
https://easytech4all.net/author/easytechonline/
https://1powercyber.substack.com
https://1powercyber.blogspot.com
https://easytech4all.tumblr.com/
https://medium.com/@1PowerCyber
AI textbook by Stuart Russell and Peter Norvig (AI Modern approach 3rd Edition Essex , England : Pearson , 2009 .
” Systems that THINK like Humans (Cognitive Architecture and Neural Networks).
Systems that ACT like Humans ( Pass the Turing Test via natural language processing , knowledge representation, automated reasoning and Learning ).
Systems that THINK RATIONALLY ( Logic Solvers , Inference and Optimisation).
Systems that ACT RATIONALLY ( Intelligent Software Agents and embodied Robots that achieve GOALS via perception, planning , reasoning, learning , communication, decision making and acting)” .
AI Researcher Pedro Domingos ascribed AI Researchers to 5 tribes on the methods they use.
Symbolists – use Logical Reasoning based on abstract symbols.
Connectionists – Build Structures inspired by the HUMAN BRAIN.
Evolutionaries – use methods inspired by Darwinian EVOLUTION.
Bayesians – Use probabilistic inference.
Analogizers – Extrapolate from similar cases seen previously.
The KNOWN seeking to unscramble the UNKNOWN in the ” Igloo of Uncertainty”. The UNKNOWN being the “indeterminacy principle”. – (Anonymous).
United States Air Force Militarised Android Tactical Awareness Kit. – Global Military Grade Cyber Defence Intel Security & AI Analysis
https://easytech4all.net/2025/02/12/united-states-air-force-militarised-android-tactical-awareness-kit/
OpenAI’s Chatgpt Evaluates Military Defense Grade Blogging / Website – Global Military Grade Cyber Defence Intel Security & AI Analysis
https://easytech4all.net/2025/01/05/openais-chatgpt-evaluates-military-defense-grade-blogging-website/
Global Military Grade Cyber Defense Intelligence and AI review (2024) – Global Military Grade Cyber Defence Intel Security & AI Analysis
https://easytech4all.net/2025/01/02/global-military-grade-cyber-defense-intelligence-and-ai-review-2024/
2024 in Review – MILITARY | DEFENSE | CYBER AI |NUCLEAR |SPACE |INTELLIGENCE – Global Military Grade Cyber Defence Intel Security & AI Analysis
https://easytech4all.net/2024/12/28/2024-in-review-attitude-of-gratitude/
Algorithmocracy | Global Military Machine | CyberAI Space | Nuclear Energy – Global Military Grade Cyber Defence Intel Security & AI Analysis
https://easytech4all.net/2024/12/09/algorithmocracy-global-military-machine-cyberai-space-nuclear-energy/
Abstract detailing semantics of hypothetical Cyber incident and Autonomous Military Grade Cyber Defense system – Global Military Grade Cyber Defence Intel Security & AI Analysis
https://easytech4all.net/2024/11/15/abstract-detailing-semantics-of-hypothetical-cyber-incident-and-autonomous-military-grade-cyber-defense-system/
Notes on CIA Triad Model and Defense in depth strategy – Global Military Grade Cyber Defence Intel Security & AI Analysis
https://easytech4all.net/2024/11/09/notes-on-cia-triad-model-and-defense-in-depth-strategy/
Upskilling & Essential Deliberations – Cybersecurity Awareness Month – Global Military Grade Cyber Defence Intel Security & AI Analysis
AI and the US B-24 Liberator Strategic Stealth Bomber. – Global Military Grade Cyber Defence Intel Security & AI Analysis
https://easytech4all.net/2024/05/04/ai-and-the-us-b-24-liberator-strategic-stealth-bomber/
Autonomous Cyber Defense Militarised Cyber Networks Nuclear Systems Security(Update) – Global Military Grade Cyber Defence Intel Security & AI Analysis
https://easytech4all.net/2024/04/20/autonomous-cyber-defense-militarised-cyber-networks-nuclear-systems-security/
https://easytech4all.net/2024/10/14/upskilling-essential-deliberations-cybersecurity-awareness-month/
Decussation of Military/Defense , CyberSpace Intelligence Analysis with respect to data/Info ingestion for AI/ML Large Language Models ? – Global Military Grade Cyber Defence Intel Security & AI Analysis
https://easytech4all.net/2024/04/07/decussation-of-military-defense-cyberspace-intelligence-analysis-with-respect-to-data-info-ingestion-for-ai-ml-large-language-models/
Landmark resolution on AI by UN General Assembly on 21st March 2024 – Global Military Grade Cyber Defence Intel Security & AI Analysis
https://easytech4all.net/2024/03/26/landmark-resolution-on-ai-by-un-general-assembly-on-21st-march-2024/
After-hours Conversations between binary digits 0 and 1 at the Cyber Intelligence Command Center of a Global Military Alliance HQ somewhere in the Northern Hemisphere. – Global Military Grade Cyber Defence Intel Security & AI Analysis
https://easytech4all.net/2024/03/20/after-hours-conversations-between-binary-digits-0-and-1-at-the-cyber-intelligence-command-center-of-a-global-military-alliance-hq-somewhere-in-the-northern-hemisphere/
CYber AI – Ostensible Intergalactic Cyber Electronic Portal – Military and Cyber Commands – Global Military Grade Cyber Defence Intel Security & AI Analysis
https://easytech4all.net/2024/03/04/cyber-ai-ostensible-intergalactic-cyber-electronic-portal-military-and-cyber-commands/
2024 in Review – MILITARY | DEFENSE | CYBER AI |NUCLEAR |SPACE |INTELLIGENCE – Global Military Grade Cyber Defence Intel Security & AI Analysis
https://easytech4all.net/2024/12/28/2024-in-review-attitude-of-gratitude/
Artificial intelligence
H o w s h o u l d A I - e n r i c h e d i n t e l l i g e n c e b e c o m m u n i c a t e d t o s t r a t e g i c d e c i s i o n - m a k e r s i n g o v e r n m e n t , t o e n s u r e t h e p r i n c i p l e s o f a n a l y t i c a l r i g o u r , t r a n s p a r e n c y , a n d
r e l i a b i l i t y o f i n t e l l i g e n c e r e p o r t i n g a n d a s s e s s m e n t a r e u p h e l d .
A l l - s o u r c e i n t e l l i g e n c e a n a l y s t s d r a w t o g e t h e r
d i v e r s e s o u r c e s o f i n f o r m a t i o n a n d c o n t e x t u a l i s e t h e m f o r s t r a t e g i c d e c i s i o n - m a k e r s a c r o s s g o v e r n m e n t . T h i s i n v o l v e s d r a w i n g o n i n t e l l i g e n c e a n d o t h e r i n f o r m a t i o n a n d a d d i n g a l a y e r o f p r o f e s s i o n a l j u d g e m e n t t o f o r m a l l - s o u r c e i n t e l l i g e n c e a s s e s s m e n t s t o s u p p o r t
d e c i s i o n - m a k i n g . A n a l y s t s d r a w c o n c l u s i o n s f r o m i n c o m p l e t e i n f o r m a t i o n w h i l s t h i g h l i g h t i n g g a p s i n k n o w l e d g e a n d e f f e c t i v e l y c o m m u n i c a t i n g u n c e r t a i n t y .
A s s e s s i n g a n d e v a l u a t i n g i n c o m p l e t e a n d u n r e l i a b l e i n f o r m a t i o n i s a c o r e r e s p o n s i b i l i t y o f a n i n t e l l i g e n c e a n a l y s t . T h e d e c i s i o n s t a k e n o n t h e b a s i s o f i n t e l l i g e n c e a s s e s s m e n t s c a n b e h i g h l y c o n s e q u e n t i a l a n d l o a d - b e a r i n g f o r i n s t a n c e , w h e t h e r t o a u t h o r i s e m i l i t a r y a c t i v i t y ,
d i p l o m a t i c r e s p o n s e s , o r d o m e s t i c p u b l i c s a f e t y m e a s u r e s i n t h e e v e n t o f n a t i o n a l e m e r g e n c i e s .
O v e r t h e p a s t t w o d e c a d e s , t h e r e h a s b e e n a h u g e g r o w t h i n t h e v o l u m e s o f d a t a p o t e n t i a l l y a v a i l a b l e f o r a n a l y s i s . I n t e l l i g e n c e a s s e s s m e n t f u n c t i o n s h a v e a s i g n i f i c a n t c h a l l e n g e t o i d e n t i f y , p r o c e s s , a n d a n a l y s e t h e s e e x p o n e n t i a l l y g r o w i n g s o u r c e s a n d q u a n t i t i e s o f
i n f o r m a t i o n . A I h a s t h e p o t e n t i a l t o o f f e r b o t h i n c r e m e n t a l a n d t r a n s f o r m a t i o n a l i m p r o v e m e n t s t o t h e r i g o u r a n d s p e e d o f i n t e l l i g e n c e a s s e s s m e n t s , a n d h a s b e e n s h o w n t o b e a c r u c i a l t o o l f o r i m p r o v i n g p r o d u c t i v i t y a n d e f f e c t i v e n e s s i n i n t e l l i g e n c e a n a l y s i s a n d
a s s e s s m e n t .
T h r e e s p e c i f i c p r i o r i t i e s f o r A u g m e n t e d I n t e l l i g e n c e s y s t e m s w i t h i n i n t e l l i g e n c e a n a l y s i s :
( i ) N a t u r a l l a n g u a g e p r o c e s s i n g a n d a u d i o v i s u a l a n a l y s i s ( s u c h a s m a c h i n e
t r a n s l a t i o n , s p e a k e r i d e n t i f i c a t i o n , o b j e c t r e c o g n i t i o n o r v i d e o
s u m m a r i s a t i o n ) ;
( i i ) F i l t e r i n g a n d t r i a g e o f m a t e r i a l g a t h e r e d t h r o u g h b u l k c o l l e c t i o n ;
( i i i ) B e h a v i o u r a l a n a l y t i c s t o d e r i v e i n s i g h t s a t t h e i n d i v i d u a l s u b j e c t l e v e l .
A c c o r d i n g t o o n e U S - b a s e d s t u d y , a n a l l - s o u r c e a n a l y s t c o u l d s a v e m o r e t h a n 4 5 d a y s a y e a r w i t h t h e s u p p o r t o f A I - e n a b l e d s y s t e m s c o m p l e t i n g t a s k s s u c h a s t r a n s c r i p t i o n a n d r e s e a r c h . A I h a s a l s o b e e n i d e n t i f i e d a s k e y t o m a i n t a i n i n g s t r a t e g i c i n t e l l i g e n c e a d v a n t a g e
o v e r i n c r e a s i n g l y s o p h i s t i c a t e d a d v e r s a r i e s . 4 A f a i l u r e t o a d o p t A I t o o l s c o u l d t h e r e f o r e l e a d t o a f a i l u r e t o p r o v i d e s t r a t e g i c w a r n i n g .
H o w e v e r , t h e u s e o f A I - e n r i c h e d i n t e l l i g e n c e t o i n f o r m a l l - s o u r c e i n t e l l i g e n c e a s s e s s m e n t i s n o t w i t h o u t r i s k . A I c o u l d b o t h e x a c e r b a t e k n o w n r i s k s i n i n t e l l i g e n c e w o r k s u c h a s b i a s a n d u n c e r t a i n t y , a n d m a k e i t d i f f i c u l t f o r a n a l y s t s t o e v a l u a t e a n d c o m m u n i c a t e t h e l i m i t a t i o n s o f
A I - e n r i c h e d i n t e l l i g e n c e . A k e y c h a l l e n g e f o r t h e a s s e s s m e n t c o m m u n i t y w i l l b e m a x i m i s i n g
t h e o p p o r t u n i t i e s a n d b e n e f i t s o f A I , w h i l e m i t i g a t i n g a n y r i s k s .
T h e m a i n r e s e a r c h a i m w a s t o g a t h e r n e w i n s i g h t o n t h e f a c t o r s t h a t s h a p e t h e d e g r e e o f c o n f i d e n c e S D M s f e e l w h e n m a k i n g l o a d - b e a r i n g d e c i s i o n s o n t h e b a s i s o f A I - e n r i c h e d i n t e l l i g e n c e a s s e s s m e n t .
I n w h a t c i r c u m s t a n c e s ( i f a n y ) i s i t n e c e s s a r y t o c o m m u n i c a t e a n d d i s t i n g u i s h t h e u s e o f A I t o s t r a t e g i c d e c i s i o n - m a k e r s , a n d a t w h a t s t a g e i n t h e r e p o r t i n g c h a i n
d o e s t h e u s e o f A I b e c o m e u n n e c e s s a r y t o c o m m u n i c a t e
H o w s h o u l d A I - e n r i c h e d i n f o r m a t i o n b e c o m m u n i c a t e d t o s t r a t e g i c d e c i s i o n m a k e r s t o e n s u r e t h e y u n d e r s t a n d t h e r e l i a b i l i t y , c o n f i d e n c e a n d l i m i t a t i o n s o f t h e
i n t e l l i g e n c e p r o d u c t a n d h o w d o e s t h i s v a r y a c r o s s i n t e l l i g e n c e c o n t e x t s a n d t y p e s o f A I s y s t e m ?
H o w d o w e e f f e c t i v e l y e d u c a t e s t r a t e g i c d e c i s i o n - m a k e r s t o m a k e h i g h - s t a k e s d e c i s i o n s b a s e d o n A I - e n r i c h e d r e p o r t i n g , a n d a c h i e v e t h e a p p r o p r i a t e l e v e l o f
u n d e r s t a n d i n g , t r u s t a n d c o n f i d e n c e i n A I s y s t e m s a n d t h e i r o u t p u t s ?
W h a t a d d i t i o n a l g o v e r n a n c e , o v e r s i g h t a n d u p s k i l l i n g i s r e q u i r e d t o p r o v i d e a s s u r a n c e s t h a t A I - g e n e r a t e d i n s i g h t s a r e b e i n g u s e d a p p r o p r i a t e l y t o s u p p o r t s e n i o r
d e c i s i o n - m a k i n g i n t h i s c o n t e x t ?
Contemporary cyber security risk management practices are largely driven by compliance requirements, which force organizations to focus on security controls and vulnerabilities.
Risk management considers multiple facets – including assets, threats, vulnerabilities and controls – which are jointly evaluated with the variables of probability and impact.
Threats cause damage to information systems. Threats utilize vulnerabilities to enact this damage, and security controls are implemented to attempt to prevent or mitigate attacks executed by threat actors. The unbalanced focus on controls and vulnerabilities prevents organizations from combating the most critical element in risk management: the threats.
This unbalanced condition is manifested as incident response processes rather than threat intelligence management in the analyst realm, adherence to predefined standards and policies in security architecture and engineering practices, and compliance verification in
the operational domain.
A functionally integrated cyber security organization is structured to place threats at the forefront of strategic, tactical and operational practices. Architects, engineers and analysts adhere to a common methodology that incorporates threat analysis and threat intelligence across systems development and operational processes. This ensures security controls are implemented, evaluated and adjusted over time per the most impactful threats and attack vectors. The resultant risk management practices are enhanced due to a higher fidelity of information regarding current state security postures. This drives
improved resource allocation and spending, and produces an agile and resilient cyber security practice. When this threat-driven approach is implemented along with tailored
compliance processes, organizations can produce information systems that are both compliant and more secure.
Current-state architecture, engineering and operational practices in the cyber security domain focus
largely on compliance to one or many regulations, directives, policies or frameworks. Some organizations
augment these practices by incorporating traditional information security concepts and principles, and
attempt to “build security in” to the development of IT systems, while the operational domain provides
security services, detects and responds to incidents, and analyzes collected data to identify trends and
patterns to improve existing security controls and services. Mature operational organizations adhere to the
Cyber Kill Chain® (CKC) or a similar practice and leverage the Intelligence Driven Defense® [1] (IDD)
approach to combat cyber threats.
Three primary gaps in this current state limit its effectiveness:
1. The behaviors, culture and the excessive amount of resources allocated to implementing and
adhering to compliance requirements
2. The lack of formalized threat modeling and analysis practices that scale vertically and
horizontally
3. The lack of institutionalized integration between the architecture/engineering functions and the
operational/analyst functions.
Expanding on these limitations, compliance-driven strategies most often result in a controls-first mindset
where systems architecture and foundational processes are driven by known sets of security controls or
control frameworks. The results of this approach are described below:
• Compliance with a list of controls – although mandated by appropriate authority – does not assure
a secure system or environment, propagating a false sense of security
• Resources are wasted on controls that do not address actual threats
• Measurement of controls effectiveness is often evaluated as a binary condition
• Analysis that would identify these issues is not performed
• Residual risk is elevated
Additionally, there is often excessive emphasis of effort on vulnerabilities, or a vulnerability-driven
approach. A vulnerability-driven approach has the following deficiencies:
• Indicates a highly reactive operational environment
• Vulnerabilities and incidents are handled at a micro level rather than addressing larger scale threat
scenarios and patterns
• Only known vulnerabilities can be corrected; unknown vulnerabilities or systemic design flaws
are neglected
• Vulnerability metrics are misinterpreted without additional context, driving unnecessary
behaviors and improper resource allocation
• Leads to gaps in architecture and operations in the areas of detect, respond and recover – due to
an unbalanced focus on prevention
Threats (whether defined as people or events) are what do damage to systems and assets. Therefore,
threats must be the primary driver of a well-designed and properly defended application, system, mission,
environment or enterprise. This is labeled the threat-driven approach, the approach advocated in this
paper. This approach will provide detailed guidance that will enable organizations to place threats at the
forefront of planning, design, testing, deployment and operational activities.
Gemini Analysis
This text explores the crucial topic of communicating AI-enriched intelligence to strategic decision-makers, emphasizing the need for analytical rigor, transparency, and reliability. It also discusses the challenges and risks associated with using AI in intelligence assessment, and how to effectively educate decision-makers about the capabilities and limitations of AI-driven insights. Finally, it touches upon current cybersecurity risk management practices and their limitations, advocating for a more threat-driven approach.
Communicating AI-Enriched Intelligence:
The core question is how to effectively communicate AI-enriched intelligence to ensure that decision-makers understand the reliability, confidence, and limitations of the information. This involves several key aspects:
* Analytical Rigor: AI should augment, not replace, analytical rigor. Human analysts must still critically evaluate the AI's output, ensuring it aligns with established intelligence principles and methodologies. The AI's reasoning process should be, to the extent possible, transparent and explainable.
* Transparency: Decision-makers need to understand how the AI arrived at its conclusions. This includes knowing the data sources, the algorithms used, and any assumptions made. Transparency builds trust and allows for better evaluation of the intelligence.
* Reliability: The reliability of AI-generated insights depends on the quality of the data, the robustness of the algorithms, and the context in which the AI is used. Decision-makers must be aware of potential biases, limitations, and uncertainties associated with the AI's output.
* Contextualization: AI-enriched intelligence must be contextualized within the broader intelligence landscape. Analysts need to integrate AI insights with information from other sources, providing a comprehensive and nuanced picture for decision-makers.
* Uncertainty Communication: AI, like human analysts, deals with incomplete information. It's crucial to clearly communicate the level of uncertainty associated with AI-generated assessments, avoiding overconfidence in the AI's predictions.
Challenges and Risks of AI in Intelligence:
While AI offers significant potential for improving intelligence analysis, it also introduces new challenges and risks:
* Exacerbating Existing Biases: AI models trained on biased data can amplify those biases, leading to skewed or inaccurate intelligence assessments.
* "Black Box" Problem: Some AI algorithms, particularly deep learning models, can be opaque, making it difficult to understand how they arrive at their conclusions. This lack of explainability can hinder trust and evaluation.
* Over-Reliance on AI: Decision-makers may become overly reliant on AI-generated insights, neglecting critical thinking and human judgment.
* Difficulty Evaluating Limitations: Analysts may struggle to assess and communicate the limitations of AI-enriched intelligence, especially when dealing with complex or novel AI systems.
Communicating the Use of AI:
The text raises the question of when it's necessary to explicitly communicate the use of AI to decision-makers. Transparency is generally recommended, especially in high-stakes decisions. However, the level of detail may vary depending on the context and the type of AI system used. The text suggests that communication about AI use should occur early in the reporting chain, allowing decision-makers to properly weigh the information.
Educating Strategic Decision-Makers:
Effective education is crucial for building trust and confidence in AI-enriched intelligence. Decision-makers need to understand:
* The Capabilities and Limitations of AI: They should have a realistic understanding of what AI can and cannot do, avoiding both overestimation and underestimation of its potential.
* The Importance of Human Oversight: AI should be seen as a tool to augment human analysis, not replace it. Human analysts are essential for critical thinking, contextualization, and ethical considerations.
* The Potential for Bias and Error: Decision-makers need to be aware of the possibility of bias in AI systems and the potential for errors, even in highly sophisticated models.
Governance, Oversight, and Upskilling:
To ensure the appropriate use of AI-generated insights, additional governance, oversight, and upskilling are required:
* Ethical Guidelines and Standards: Clear ethical guidelines and standards should be established for the development and use of AI in intelligence.
* Independent Oversight Mechanisms: Independent oversight bodies can help ensure that AI systems are used responsibly and ethically.
* Training and Education for Analysts: Intelligence analysts need training on how to effectively use AI tools, evaluate their output, and communicate their limitations.
* Training and Education for Decision-makers: Decision-makers need to be educated about the capabilities and limitations of AI, so they can make informed decisions based on AI-enriched intelligence.
Cybersecurity Risk Management:
The text then shifts to a discussion of cybersecurity risk management, arguing that current practices are too focused on compliance and vulnerabilities, rather than threats. It advocates for a more threat-driven approach, where security efforts are prioritized based on the most likely and impactful threats. This involves:
* Formalized Threat Modeling and Analysis: Developing robust threat models to understand potential attack vectors and prioritize defenses.
* Integration of Threat Intelligence: Incorporating threat intelligence into all aspects of cybersecurity, from architecture and engineering to operations and incident response.
* Shifting from Compliance-Driven to Threat-Driven: Moving away from a purely compliance-based approach to a more proactive and adaptive security posture.
Key Takeaways:
* Effectively communicating AI-enriched intelligence requires analytical rigor, transparency, and a clear understanding of the capabilities and limitations of AI.
* Educating decision-makers about AI is crucial for building trust and ensuring its responsible use.
* Cybersecurity risk management should be threat-driven, prioritizing defenses based on the most likely and impactful threats. Compliance should be a supporting factor, not the primary driver.
* Integrating threat intelligence across all cybersecurity functions is essential for a robust and adaptive security posture.
The Android Tactical Awareness Kit (ATAK) is an Android-based geospatial and situational awareness application developed by the U.S. Air Force Research Laboratory. It provides military personnel with tools for precision targeting, navigation, real-time data sharing, and enhanced situational awareness. The application features a plugin architecture, allowing for customization to support various mission requirements, including direct action, combat advising, law enforcement, protection operations, border security, disaster response, off-grid communications, and precision mapping.
ATAK enables users to navigate using GPS and overlay geospatial map data with real-time situational information. The software represents the surrounding area using military standard APP-6 symbology and customized symbols from sources like Google Earth and Google Maps. Communication is facilitated through the Cursor on Target data format standard.
Initially created in 2010 and based on the NASA WorldWind Mobile codebase, ATAK's development and deployment have accelerated since 2016. As of 2020, ATAK has a growing base of 250,000 military and civilian users across numerous public safety agencies and U.S. partner nations, and has seen the addition of 15 United States Department of Defense programs.
The application is actively employed by various U.S. military branches, including the United States Air Force, Army, Navy, Marine Corps, and Special Operations Command. Additionally, agencies such as the Department of Homeland Security, Secret Service, and the Federal Bureau of Investigation utilize ATAK. Internationally, units like the British Army's Special Air Service and the UK's Special Boat Service have adopted the platform.
ATAK is available in several versions tailored to different user groups:
ATAK-CIV: A fully releasable version for first responders and licensed commercial developers, distributed through approved government-hosted sites and direct commercial sales.
ATAK-GOV: An ITAR-restricted version for U.S. government entities and foreign governments, distributed through approved government-hosted sites and direct commercial sales.
ATAK-MIL: A military-sensitive version for U.S. and foreign military end-users, distributed through approved government-hosted sites.
ATAK-PR: A publicly releasable version made available in April 2020, which is not plugin capable and only compatible with arm64-based systems.
The application has been utilized in various operations, including disaster response efforts during hurricanes and daily public safety operations. Its capabilities have been recognized as enhancing situational awareness and communication among users.
For a visual demonstration of ATAK's capabilities, you can refer to the following video:
TAK Video 2021: https://youtu.be/fiBt0wEiKh8
Android War tactical
https://youtu.be/ttIdSGEufF0?si=P60LsW6xTsNvhmle
The New Battlefield: Space Defence and the Future of Military Operations
https://youtu.be/GEoWv6mZ0_w?si=3dNWc8Xglvz1v24j
What Does a CIA Analyst Really Do? – The Cipher Brief
https://www.thecipherbrief.com/book-review/what-does-a-cia-analyst-really-do
Arms Transfers: U.S. and Russia’s Biggest Trading Partners
https://www.visualcapitalist.com/cp/arms-transfers-u-s-and-russias-biggest-trading-partners/
Building the Connected Battlefield for the Tactical Edge
https://youtu.be/U7XqyXi-9pE?si=k_LhZqw-2yHcNukq
Laptops with Powerful GPUs: Transforming the Military Metaverse and Hyperreal Simulations.
High-performance laptops equipped with powerful GPUs are indeed making waves in the realm of military training and simulations. These advancements are paving the way for a more immersive and realistic training experience, ultimately leading to better-prepared soldiers. Here's how:
1. Enhanced Metaverse Training:
Virtual Battlefields: Powerful GPUs enable the creation of complex and dynamic virtual battlefields within the metaverse. Soldiers can train in diverse environments, from urban landscapes to rugged terrains, fostering adaptability and situational awareness.
Realistic Scenarios: Advanced simulations can now incorporate intricate details like weather effects, ballistics, and even enemy AI behavior. This heightened realism provides invaluable experience for soldiers to react and make decisions under pressure.
Multiplayer Training: Laptops with powerful GPUs can support real-time multiplayer training exercises within the metaverse. Soldiers can collaborate and strategize in virtual environments, honing their teamwork and communication skills.
2. Hyperreal Simulations:
Immersive Training: High-fidelity graphics and haptic feedback technology create a hyper-realistic training experience, blurring the lines between virtual and real. This immersive environment allows soldiers to practice complex maneuvers and procedures in a safe and controlled setting.
Improved Decision-Making: Hyperreal simulations can be used to test and refine tactics and procedures in various scenarios. This data-driven approach allows for better decision-making in real-world operations.
Advanced Medical Training: Surgeons and medical personnel can utilize hyperreal simulations to practice complex procedures in a risk-free environment, leading to improved surgical skills and patient outcomes.
Research Links and Sources:
"The Military Metaverse: How VR and AR Are Transforming Soldier Training" by Defense One: https://medium.com/@lunawolfe01/military-metaverse-revolutionizing-soldier-training-d475eb830cae
"Hyperrealism in Military Training: The Future of Soldier Preparation" by The National Defense Industrial Association:
https://apps.dtic.mil/sti/citations/trecms/AD1177538
"Laptops for the Battlefield: How Powerful GPUs Are Equipping Soldiers for the Future" by PC Magazine: https://www.pcmag.com/picks
"The Rise of the Military Metaverse: A Report from the RAND Corporation" by RAND Corporation:
https://warontherocks.com/2022/02/the-full-potential-of-a-military-metaverse/
Additional Points:
The integration of AI and machine learning into these simulations is further enhancing their realism and effectiveness.
Ethical considerations surrounding the use of the metaverse and hyperreal simulations in military training need to be carefully addressed.
The accessibility and affordability of powerful laptops with GPUs are crucial factors for widespread adoption within the military.
Overall, laptops with powerful GPUs are playing a transformative role in the military metaverse and hyperreal simulations. These advancements offer exciting possibilities for enhanced soldier training, improved decision-making, and ultimately, a more prepared and effective military force.
Air & Space Forces Magazine: Space Force Eyes New Jam-Resistant Tactical SATCOM Options
https://www.airandspaceforces.com/space-force-prototypes-jam-resistant-comms/
Elbit Systems / DAiR Multi-Mission Tactical Radar
https://youtu.be/i_Q3WVDzSfo?si=zG9JjlUzZ1NTE7x6
United States Air Force Militarised Android Tactical Awareness Kit.
Android Team Awareness Kit (ATAK) is an Android smartphone geospatial infrastructure and military situation awareness app. It allows for precision targeting, surrounding land formation intelligence, situational awareness, navigation, and data sharing. This Android app is a part of the larger TAK family of products.[1] ATAK has a plugin architecture which allows developers to add functionality. This extensible plugin architecture that allows enhanced capabilities for specific mission sets (Direct Action, Combat Advising, Law Enforcement, Protection Operations, Border Security, Disaster Response, Off-grid Communications, Precision Mapping and Geotagging).
Actively Employed and Deployed Primarily by :
1.United States Military.
2.United States Special Operations Command.
3.United States Army.
4.United States Army Special Operations Command.
5.United States Air Force.
6.United States National Guard.
7.United States Navy and United States Marine.
8.United States Department of Homeland Security.
9.United States Secret Service.
10.Federal Bureau of Investigation.
11.British Army.
12.Special Air Service.
13.UK Special Reconnaissance Regiment
14.UK Special Forces Support Group
15.UK Pathfinder Platoon
16.UK Ranger Regiment
17. UK 4/73 (Sphinx) Special Observation Post Battery RA
18.The Black Watch
19.The Royal Regiment of Scotland
20. 1st The Queen's Dragoon Guards
21. UK Royal Navy
22. UK Special Boat Service and Royal Marines
Developer(s) - Air Force Research Laboratory & Maintained by the TAK Product Center. US Army Research Laboratory.
It enables users to navigate using GPS and geospatial map data overlayed with real-time situational awareness of ongoing events. The ATAK software represents the surrounding area using the military standard APP-6 symbology, and customized symbols such as icons from Google Earth and Google Maps for iconography and the Cursor on Target data format standard for communication.
Initially created in 2010 by the Air Force Research Laboratory, and based on the NASA WorldWind Mobile codebase its development and deployment grew slowly, then rapidly since 2016.
As of 2020, ATAK has a growing base of 250,000 military and civilian users across numerous public safety agencies and US partner nations, and has seen the addition of 15 United States Department of Defense programs.
ATAK began in August 2010 and was originally based on NASA WorldWind Mobile. The goal was to demonstrate robust information sharing in a mobile format.
In 2013, officials at Draper Laboratory said that the system would be compatible with Android mobile operating systems and could be used for navigation, spatial awareness, and controlling drones.
ATAK has various end-user versions:
ATAK - Civilian (ATAK-CIV) - A distribution controlled but fully-releasable version of the TAK Product line for First Responders, Licensed Commercial Developers. Distribution for ATAK-CIV is through Approved, Government Hosted Sites, Direct Commercial Sales (DCS).[14] This version has no ITAR capabilities.
ATAK - Government (ATAK-GOV) - ITAR restricted version of the TAK Product line for USG entities and Foreign Government. Distribution for ATAK-GOV are through Approved, Government Hosted Sites; Direct Commercial Sales (DCS). This version of ATAK has no military (MIL) sensitive capabilities.
ATAK - Military (ATAK-MIL) - Military Sensitive version of the TAK Product line for US and Foreign Military end-users. Similar to ATAK-GOV, distribution is through Approved, Government Hosted Sites. However, is not available through Direct Commercial Sales (DCS).
ATAK - Public Release (ATAK-PR) - (Discontinued) Was made available for download on takmaps.com in April 2020. ATAK-PR is publicly releasable version of the TAK Product line for public individuals for public uses. This version of ATAK is not plugin capable. And is only compatible with arm64 based systems due to file size restrictions. End users with armeabi-v7a or x86 devices are to use ATAK-CIV.
On October 14, 2014, U.S. Army Geospatial Center recommended AFRL's Android Team Awareness Kit (ATAK), over the world-leader Esri's Commercial Joint Mapping Tool Kit (CJMTK), NASA's World Wind, and the Army's Globe Engine (AGE) for map engine driving the Nett Warrior End User Device. ATAK was selected due to similar capabilities with CJMTK, similar risk, and less than one-third of the total cost.
According to a January 2016 article in National Defense Magazine, "[ATAK] has already been fielded to AFSOC units".
In September 2015, DARPA reported that ATAK was used in a successful demonstration of the Persistent Close Air Support Program, and is in use by thousands of users.
Polaris integrated its Ground Guidance software into an ATAK Plugin to allow on and off-road routing for mounted and dismounted soldiers, accounting for terrain, weather, enemy activity and equipment load.
In 2018, USAF Security Forces deployed ATAK at Eglin AFB, Florida.
The Android Team Awareness Kit or TAK is currently used by thousands of Department of Homeland Security personnel, along with other members of the Homeland Security Enterprise including state and local public safety personnel. It is in various stages of transition across DHS components and is the emerging DHS-wide solution for tactical awareness.
TAK has supported the rescue of over 2,000 people during disaster response for seven major hurricanes (Harvey, Irma, Maria, Florence, Lane, Michael, and Dorian). The capability is also regularly used during daily public safety operations and national security special events like United Nations General Assembly meetings and the Super Bowl.
On September 1, 2020 - the TAK Product Center released ATAK-CIV (Android Team Awareness Kit - Civil Use) - Version 4.1.1.0 on Google Play Store.
In addition to the Android version, there is also a Microsoft Windows version (WinTAK), an Apple iOS version under development (iTAK), and finally a Virginia-based military tech firm’s (LucyTAK). WinTAK is an application developed for the Microsoft Windows Operating System which uses maps to allow for precise targeting, intelligence on surrounding land formations, navigation, and generalized situational awareness. It was developed in conjunction with ATAK to provide similar functionality on a Windows platform.
On August 19, 2020, the source code for the Android Tactical Assault Kit for Civilian Use (ATAK-CIV), the official geospatial-temporal and situational awareness tool used by the US Government, has been released on United States Department of Defense - Defense Digital Service GitHub repository.ATAK-CIV is managed by the Tactical Assault Kit Configuration Steering Board (TAK CSB) and is designed for used by (US) federal employees.
It is made available to the open source community with the hope that community contributions will improve functionality, add features, and mature this work.
Users :
United States
Military
United States Special Operations Command
United States Army
United States Army Special Operations Command
United States Air Force
United States National Guard
United States Navy and United States Marine Corps(primarily use APASS and KILSWITCH but instances of ATAK use seen as of 2021)
United States Coast Guard
Law Enforcement and Emergency Services
United States Department of Homeland Security
United States Secret Service
Federal Bureau of Investigation
U.S. Customs and Border Protection
Immigration and Customs Enforcement
Federal Emergency Management Agency
Albuquerque Fire Rescue
Colorado Department of Public Safety
Division of Fire Prevention and Control, Center of Excellence for Advanced Technology Aerial Firefighting (CoE)
Corona Fire Department
New York City Police Department
Canada
Royal Canadian Mounted Police
Emergency Response Team
Europe
United Kingdom
British Army
Special Air Service
Special Reconnaissance Regiment
Special Forces Support Group
Pathfinder Platoon
Ranger Regiment
4/73 (Sphinx) Special Observation Post Battery RA
The Black Watch
The Royal Regiment of Scotland
1st The Queen's Dragoon Guards
Royal Navy
Special Boat Service
Royal Marines
Choosing the best alternative to Android ATAK (Army Tactical Approach and Communication) platform depends on your specific needs and context. Here are some popular options along with their strengths and limitations:
1. iOS ATAK:
Strengths: Familiar interface for iOS users, seamless integration with ATAK ecosystem, real-time situational awareness, offline functionality.
Limitations: Requires compatible iOS devices, some features might not be fully optimized for iOS.
Links: https://thelastmile.gotennapro.com/atak-the-latest-land-navigation-tool-for-the-army/
2. Tactical Air Control Party Missions :
Strengths: Designed specifically for Tactical Air Control Party missions, advanced fire control capabilities, voice and text communication, situational awareness tools.
Limitations: Steep learning curve, not intended for general situational awareness purposes, requires specific training and authorization.
Links: https://www.airforce.com/aim-high-app
3. Battlecock:
Strengths: Lightweight and efficient, focus on tactical communication and messaging, supports various data formats, offline messaging capabilities.
Limitations: Limited user interface features, primarily text-based communication, not as feature-rich as ATAK for situational awareness.
Links: https://battlepro.ca/
4. Tactical Maps:
Strengths: User-friendly interface, customizable map layers, collaborative features, supports multiple data formats, offline functionality.
Limitations: Not as robust as ATAK for some advanced features, limited to 2D mapping, potential subscription costs.
Links: https://tacmaps.gg/
5. OpenSource Blueforce:
Strengths: Open-source and free, offline map functionality, highly customizable, supports various plugins for additional features.
Limitations: Lacks some native ATAK features like Blueforce Tracking, may require technical expertise for advanced uses.
Links: https://osmand.net/go
6. Gaia GPS:
Strengths: Excellent off-road navigation features, detailed topographic maps, community-driven content, offline functionality.
Limitations: Primarily focused on navigation, limited tactical communication and situational awareness tools.
Links: https://www.gaiagps.com/
Additional Considerations:
Interoperability: Ensure your chosen platform can exchange data and collaborate with existing ATAK users and systems.
Security: Choose a platform with robust security measures to protect sensitive information.
Cost: Some platforms offer free basic features while others require subscriptions for advanced features.
Choosing the best alternative requires careful evaluation of your specific needs and priorities. Consider your budget, user familiarity, desired features, and integration requirements to make the most informed decision.
Remember, these are just some of the available options, and new platforms are constantly emerging. Researching and testing different platforms might be necessary to find the perfect fit for your specific operation.
Several companies are leading the development of advanced portable modular battlefield management systems, each offering unique capabilities and features:
1. **Thales Group**: Thales provides the T-BMS (Tactical Battlefield Management System) and Comm@nder. These systems offer automated reporting, graphical orders dissemination, secure data communications, and interfaces for sensor displays. They are designed to be scalable from battalion levels down to individual soldiers, enhancing situational awareness and operational effectiveness across various military units [[❞]](https://www.thalesgroup.com/en/worldwide/defence/tactical-battlefield-management-systems-t-bms-commnder).
2. **Elbit Systems**: This Israeli company is renowned for its advanced battlefield management systems used by over 20 militaries worldwide. Their systems include enhanced tactical computers and communication devices, integrated into numerous military vehicles to improve situational awareness and operational efficiency. Elbit's systems are particularly noted for their deployment in the Royal Netherlands Army's ground forces [[❞]](https://www.defencetalk.com/advanced-battlefield-management-system-for-royal-netherlands-army-14284/).
3. **L3Harris, Northrop Grumman, Leidos, Raytheon, and SAIC**: These companies are part of the US Air Force's Advanced Battle Management System (ABMS) consortium. ABMS aims to create a comprehensive, networked battle management system that integrates data from various sources to provide commanders with a real-time operational picture, crucial for joint all-domain command and control (JADC2) [[❞]](https://www.thedefensepost.com/2022/09/20/usaf-abms-consortium/).
These companies represent the forefront of battlefield management technology, providing integrated, flexible, and highly advanced systems tailored to modern military needs.
some information that might be helpful:
Major Players: Here are some prominent companies known to be involved in developing IMBMS or similar battlefield management systems:
Integrated Modular Battlefield Management Systems (IMBMS)
Lockheed Martin (US)
Raytheon Technologies (US)
Northrop Grumman (US)
General Dynamics (US)
Thales Group (France)
Elbit Systems (Israel)
Saab Group (Sweden)
BAE Systems (UK)
L3Harris Technologies (US)
Airbus Defence and Space (Europe)
References :
Battlefield Management Systems Market Size Report, 2030
https://www.grandviewresearch.com/industry-analysis/battlefield-management-systems-market-report
https://www.forces.net/news/british-army-officer-military-mobile-app-game-changer
https://www.dhs.gov/sites/default/files/publications/OIC_MANET-NYPD-ESU-AAR_170921-508_0.pdf
https://www.cofiretech.org/feature-projects/team-awareness-kit-tak/tak
https://web.archive.org/web/20220626015246/https://www.shephardmedia.com/news/digital-battlespace/stauder-to-improve-usmc-android-apps/
https://web.archive.org/web/20220626015243/https://federalnewsnetwork.com/wp-content/uploads/2020/06/Panasonic-ATAK-Top5-WhitePaper-Final-040620-1.pdf
https://web.archive.org/web/20210910162455/https://www.dvidshub.net/image/6784743/lse-2021-mdsu2
https://www.af.mil/News/Article-Display/Article/1575959/defenders-go-mobile-with-new-comm-system/
https://www.extremetech.com/extreme/232012-the-armys-special-operations-command-is-trading-in-its-android-devices-for-faster-iphones
https://www.army.mil/article/232004/software_allows_soldiers_to_see_maintain_radio_connectivity
https://sofrep.com/news/how-an-android-app-is-helping-commandos-call-close-air-support-faster/
https://github.com/deptofdefense/AndroidTacticalAssaultKit-CIV
https://techlinkcenter.org/technologies/android-team-awareness-kit-atak/
https://www.dhs.gov/science-and-technology/news/2020/05/05/snapshot-growing-impact-tak
https://www.eglin.af.mil/News/Article-Display/Article/1572874/defenders-go-mobile-with-new-comm-system/
http://soldiersystems.net/2015/11/12/juggernaut-board-mff-t2/
https://commons.wikimedia.org/wiki/File:US_Army%27s_Nett_Warrior_Map_Engine_Trade_Study_Report.pdf
http://www.nbcnews.com/id/53336049/ns/technology_and_science-science/t/troops-call-military-airstrike-theres-app/
https://www.dhs.gov/science-and-technology/news/2017/11/17/snapshot-atak-increases-situational-awareness-communication
https://www.fbo.gov/index?s=opportunity&mode=form&tab=core&id=8f69fc9a1ac486675a2d08a5ac57cc41
https://www.extremetech.com/extreme/232012-the-armys-special-operations-command-is-trading-in-its-android-devices-for-faster-iphones
https://www.af.mil/News/Article-Display/Article/1575959/defenders-go-mobile-with-new-comm-system/
https://web.archive.org/web/20220626015243/https://federalnewsnetwork.com/wp-content/uploads/2020/06/Panasonic-ATAK-Top5-WhitePaper-Final-040620-1.pdf
https://www.samm.dsca.mil/glossary/direct-commercial-sale/
Indian Army Rolls Out Rs 2,402 Crore Surveillance System ‘SANJAY’ for Network-Centric Warfare | Republic World
https://www.republicworld.com/defence/defence-technology/indian-army-rolls-out-rs-2402-crore-surveillance-system-sanjay-for-network-centric-warfare
US gives Indian company access to advanced grade satellite imagery
https://sundayguardianlive.com/top-five/us-gives-indian-company-access-to-advanced-grade-satellite-imagery
India gets an observer seat in the Eurodrone program
https://www.defensenews.com/global/europe/2025/01/21/india-gets-an-observer-seat-in-the-eurodrone-program/?utm_source=sailthru&utm_medium=email&utm_campaign=c4-overmatch
The CIA triad .
1. Confidentiality 2.Integrity 3.Availability across hardware , software and communication. In three different layers :
1. Physical Security 2.Personal Security and 3. Organisational Security.
Organisation for Economic Cooperstion and Development (OECD) - 9 guidelines for information security.
1. Awareness 2. Responsibility 3. Response 4. Ethics 5. Democracy 6. Risk Assessment 7. Security Design 8. Implementation 9. Security management reassessment.
Donn Parkers 6 Atomic elements of information or Parkerian Hexad.
1. Confidentiality 2. Integrity 3. Availability 4.Possession 5.Authenticity 6.Utility.
Types of Information : Electronic or Physical . Paperwork/Tangible and Intangible = Knowledge.
Structured Risk management process :
* Risk is the likelihood or Probability that something bad will happen that causes harm to an informational asset.
*Vulnerability is weakness or deficiency exploitated to cause harm to informational asset.
*Manmade or nature threat has the potential to cause harm.
*It is not possible to identify all risk or eliminate all risk. Remaining risk is called residual risk.
*Risk Assessment using subjective qualitative analysis based on informed opinion. Where finance and historical informational is available analysis is quantitative in nature.
Most vulnerable point in information systems is human user, operator, designer or other human.
1. Identify information , related assests plus threats , vulnerabilities and impacts.
2. Evaluate Risks.
3.Avoid Mitigate Share treat Address risks .
4. Risk Mitigation - Select Design Appropriate Security Controls and implement them.
5. Laws regulation regarding data access storage transfer and destruction.
6. Balanced protection of CIA triad without hampering organisational productivity and efficient policy implementation.
7. Protect Intellectual Property (IP) .
8. Protect against Damage Theft of info resources. Natural disasters and computer server malfunction.
9. Manage cost of information risk. Risk Control.
10. Onging iterative process. Must be repeated indefinitely.
11. Information security must protect information throughout its lifespan, from the initial creation of the information on through to the final disposal of the information.[158] The information must be protected while in motion and while at rest. During its lifetime, information may pass through many different information processing systems and through many different parts of information processing systems.
Code of practice for information security management recommends the following be examined during a risk assessment:
• security policy,
• organization of information security,
• asset management,
• human resources security,
• physical and environmental security,
• communications and operations management,
• access control,
• information systems acquisition, development, and maintenance,
• information security incident management,
• business continuity management
• regulatory compliance.
In broad terms, the risk management process consists of:
• Identification of assets and estimating their value. Include: people, buildings, hardware, software, data (electronic, print, other), supplies.
• Conduct a threat assessment. Include: Acts of nature, acts of war, accidents, malicious acts originating from inside or outside the organization.
• Conduct a vulnerability assessment, and for each vulnerability, calculate the probability that it will be exploited. Evaluate policies, procedures, standards, training, physical security, quality control, technical security.
• Calculate the impact that each threat would have on each asset. Use qualitative analysis or quantitative analysis.
• Identify, select and implement appropriate controls. Provide a proportional response. Consider productivity, cost effectiveness, and value of the asset.
• Evaluate the effectiveness of the control measures. Ensure the controls provide the required cost effective protection without discernible loss of productivity.
For any given risk, management can choose to accept the risk based upon the relative low value of the asset, the relative low frequency of occurrence, and the relative low impact on the business.Or, leadership may choose to mitigate the risk by selecting and implementing appropriate control measures to reduce the risk. In some cases, the risk can be transferred to another business by buying insurance or outsourcing to another business. The reality of some risks may be disputed. In such cases leadership may choose to deny the risk.
A successful information security team involves many different key roles to mesh and align for the "CIA" triad to be provided effectively.
Gordon Loeb Model :
Analytical Model. Mathematical Economic Model. Analyse optimal investment level in Infosec. Benefits - Cost Savings . Protect data breaches through increased investment in cyber security.
Risk Management : CISA
The Process of identifying vulnerabilities and threats to information resources used by an organisation in achieving business objectives and deciding what countermeasures to take in reducing risk to an acceptable level based on the value of the info resource to the organisation.
Brief descriptions :
1. Confidentiality : * Component of Privacy and not interchangeable.
* Reduce Probability of unauthorised , inappropriate access to data.
* No unlawful use - No - disclosure | disruption | Deletion | Corruption | Inspection | Modification | Recording | Devaluation |
Finally , reduce adverse impact of breaches.
2. Integrity : Maintain Assure - Accuracy , Completeness of Data over entire life cycle.
*No Data : Modification in undetected Manner.
*Multipurpose / Multiuser Computer System :
*Compartmentalize Data / Processing.
*Minimise Adverse Impact.
*Credibility *Consistency *Truthfulness *Completeness *Accuracy *Timeliness *Assurance.
3. Availability: Info Available when needed.
Function Correctly :
*Computer Systems : Store Process Information | Security Controls | Communication channels used to access computer systems resources #Comsec
*High Availability Systems : Military Defense Networks | Transportation | Aviation | Government Administration | Electric Power Grids | Hospitals | Telecommunications .
* Prevent Denial of Service Attacks. Distributed Denial of Service Attacks. Flooding system through plethora of incoming messages to target the computer / Server / Website thereby forcing it to shut down or go offline.
Non-repudiation :
In law, non-repudiation implies one's intention to fulfill their obligations to a contract. It also implies that one party of a transaction cannot deny having received a transaction, nor can the other party deny having sent a transaction.[109]
It is important to note that while technology such as cryptographic systems can assist in non-repudiation efforts, the concept is at its core a legal concept transcending the realm of technology.[110] It is not, for instance, sufficient to show that the message matches a digital signature signed with the sender's private key, and thus only the sender could have sent the message, and nobody else could have altered it in transit (data integrity).[111] The alleged sender could in return demonstrate that the digital signature algorithm is vulnerable or flawed, or allege or prove that his signing key has been compromised.
DATABASE :
A database transaction symbolizes a unit of work, performed within a database management system (or similar system) against a database, that is treated in a coherent and reliable way independent of other transactions. A transaction generally represents any change in a database.
In computer science, ACID (atomicity, consistency, isolation, durability) is a set of properties of database transactions intended to guarantee data validity despite errors, power failures, and other mishaps.[1] In the context of databases, a sequence of database operations that satisfies the ACID properties (which can be perceived as a single logical operation on the data) is called a transaction. For example, a transfer of funds from one bank account to another, even involving multiple changes such as debiting one account and crediting another, is a single transaction.
Security Controls :
Selecting and implementing proper security controls will initially help an organization bring down risk to acceptable levels.
Administrative controls :
(also called procedural controls) consist of approved written policies, procedures, standards, and guidelines. Administrative controls form the framework for running the business and managing people. They inform people on how the business is to be run and how day-to-day operations are to be conducted.
Logical controls :
(also called technical controls) use software and data to monitor and control access to information and computing systems. Passwords, network and host-based firewalls, network intrusion detection systems, access control lists, and data encryption are examples of logical controls
An important logical control that is frequently overlooked is the principle of least privilege, which requires that an individual, program or system process not be granted any more access privileges than are necessary to perform the task.
Physical controls :
monitor and control the environment of the work place and computing facilities.They also monitor and control access to and from such facilities and include doors, locks, heating and air conditioning, smoke and fire alarms, fire suppression systems, cameras, barricades, fencing, security guards, cable locks, etc. Separating the network and workplace into functional areas are also physical controls.
Security Classification :
An important aspect of information security and risk management is recognizing the value of information and defining appropriate procedures and protection requirements for the information. Not all information is equal and so not all information requires the same degree of protection.This requires information to be assigned a security classification.The first step in information classification is to identify a member of senior management as the owner of the particular information to be classified. Next, develop a classification policy. The policy should describe the different classification labels, define the criteria for information to be assigned a particular label, and list the required security controls for each classification
The Information Systems Audit and Control Association (ISACA) and its Business Model for Information Security also serves as a tool for security professionals to examine security from a systems perspective, creating an environment where security can be managed holistically, allowing actual risks to be addressed.
All employees in the organization, as well as business partners, must be trained on the classification schema and understand the required security controls and handling procedures for each classification.
Access Control :
Access to protected information must be restricted to people who are authorized to access the information.[178] The computer programs, and in many cases the computers that process the information, must also be authorized.[179] This requires that mechanisms be in place to control the access to protected information.[179] The sophistication of the access control mechanisms should be in parity with the value of the information being protected; the more sensitive or valuable the information the stronger the control mechanisms need to be.[180] The foundation on which access control mechanisms are built start with identification and authentication.
Access control is generally considered in three steps: identification, authentication, and authorization.
Identification :
is an assertion of who someone is or what something is. If a person makes the statement "Hello, my name is John Doe" they are making a claim of who they are.However, their claim may or may not be true. Before John Doe can be granted access to protected information it will be necessary to verify that the person claiming to be John Doe really is John Doe.
Authentication :
is the act of verifying a claim of identity. When John Doe goes into a bank to make a withdrawal, he tells the bank teller he is John Doe, a claim of identity.The bank teller asks to see a photo ID, so he hands the teller his driver's license.The bank teller checks the license to make sure it has John Doe printed on it and compares the photograph on the license against the person claiming to be John Doe.[ If the photo and name match the person, then the teller has authenticated that John Doe is who he claimed to be. Similarly, by entering the correct password, the user is providing evidence that he/she is the person the username belongs to.
There are three different types of information that can be used for authentication:
• Something you know: things such as a PIN, a password, or your mother's maiden name
• Something you have: a driver's license or a magnetic swipe card
• Something you are: biometrics, including palm prints, fingerprints, voice prints, and retina (eye) scans
Time-based one-time password (TOTP) :
is a computer algorithm that generates a one-time password (OTP) using the current time as a source of uniqueness. As an extension of the HMAC-based one-time password algorithm (HOTP), it has been adopted as Internet Engineering Task Force (IETF) standard RFC 6238.
TOTP is the cornerstone of Initiative for Open Authentication (OATH), and is used in a number of two-factor authentication (2FA) systems.
Authorization :
After a person, program or computer has successfully been identified and authenticated then it must be determined what informational resources they are permitted to access and what actions they will be allowed to perform (run, view, create, delete, or change). This is called authorization. Authorization to access information and other computing services begins with administrative policies and procedures.The policies prescribe what information and computing services can be accessed, by whom, and under what conditions. The access control mechanisms are then configured to enforce these policies.
Access Control Mechanisms :
The access control mechanism a system offers will be based upon one of three approaches to access control, or it may be derived from a combination of the three approaches.
The non-discretionary :
approach consolidates all access control under a centralized administration. The access to information and other resources is usually based on the individuals function (role) in the organization or the tasks the individual must perform.
The discretionary approach :
gives the creator or owner of the information resource the ability to control access to those resources.In the mandatory access control approach, access is granted or denied basing upon the security classification assigned to the information resource.
Role-based access control :
is a policy-neutral access control mechanism defined around roles and privileges. The components of RBAC such as role-permissions, user-role and role-role relationships make it simple to perform user assignments. A study by NIST has demonstrated that RBAC addresses many needs of commercial and government organizations.RBAC can be used to facilitate administration of security in large organizations with hundreds of users and thousands of permissions.
In computer security, mandatory access control (MAC) :
refers to a type of access control by which the operating system or database constrains the ability of a subject or initiator to access or generally perform some sort of operation on an object or target.[1] In the case of operating systems, a subject is usually a process or thread; objects are constructs such as files, directories, TCP/UDP ports, shared memory segments, IO devices, etc. Subjects and objects each have a set of security attributes. Whenever a subject attempts to access an object, an authorization rule enforced by the operating system kernel examines these security attributes and decides whether the access can take place. Any operation by any subject on any object is tested against the set of authorization rules (aka policy) to determine if the operation is allowed
In computer security, discretionary access control (DAC):
is a type of access control defined by the Trusted Computer System Evaluation Criteria[1] (TCSEC) as a means of restricting access to objects based on the identity of subjects and/or groups to which they belong. The controls are discretionary in the sense that a subject with a certain access permission is capable of passing that permission (perhaps indirectly) on to any other subject (unless restrained by mandatory access control).
Occasionally, a system as a whole is said to have "discretionary" or "purely discretionary" access control when that system lacks mandatory access control. On the other hand, systems can implement both MAC and DAC simultaneously, where DAC refers to one category of access controls that subjects can transfer among each other, and MAC refers to a second category of access controls that imposes constraints upon the first.
To be effective, policies and other security controls must be enforceable and upheld. Effective policies ensure that people are held accountable for their actions.[210] The U.S. Treasury's guidelines for systems processing sensitive or proprietary information, for example, states that all failed and successful authentication and access attempts must be logged, and all access to information must leave some type of audit trail.
An audit trail (also called audit log) :
is a security-relevant chronological record, set of records, and/or destination and source of records that provide documentary evidence of the sequence of activities that have affected at any time a specific operation, procedure, event, or device.Audit records typically result from activities such as financial transactions,[3] scientific research and health care data transactions,[4] or communications by individual people, systems, accounts, or other entities.
Privelege Mode :
In computer science, hierarchical protection domains, often called protection rings, are mechanisms to protect data and functionality from faults (by improving fault tolerance) and malicious behavior (by providing computer security).
Privilege rings for the x86 available in protected mode
Computer operating systems provide different levels of access to resources. A protection ring is one of two or more hierarchical levels or layers of privilege within the architecture of a computer system. This is generally hardware-enforced by some CPU architectures that provide different CPU modes at the hardware or microcode level.
Fault tolerance :
is the ability of a system to maintain proper operation in the event of failures or faults in one or more of its components. Any decrease in operating quality is proportional to the severity of the failure, unlike a naively designed system in which even a small failure can lead to total breakdown. Fault tolerance is particularly sought after in high-availability, mission-critical, or even life-critical systems. The ability to maintain functionality when portions of a system break down is referred to as graceful degradation.[1]
A fault-tolerant design enables a system to continue its intended operation, possibly at a reduced level, rather than failing completely when some part of the system fails.
High availability (HA) :
is a characteristic of a system that aims to ensure an agreed level of operational performance, usually uptime, for a higher than normal period.
"Always-on" .
Modernization has resulted in an increased reliance on these systems. For example, hospitals and data centers require high availability of their systems to perform routine daily activities.
A single point of failure (SPOF) :
is a part of a system that, if it fails, will stop the entire system from working. SPOFs are undesirable in any system with a goal of high availability or reliability, be it a business practice, software application, or other industrial system.
A safety-critical system or life-critical system is a system whose failure or malfunction may result in one (or more) of the following outcomes:
death or serious injury to people
loss or severe damage to equipment/property
environmental harm.
A safety-related system (or sometimes safety-involved system) comprises everything (hardware, software, and human aspects) needed to perform one or more safety functions, in which failure would cause a significant increase in the safety risk for the people or environment involved.[5] Safety-related systems are those that do not have full responsibility for controlling hazards such as loss of life, severe injury or severe environmental damage.
Examples[1] of safety-critical systems. From left to right, top to bottom: the glass cockpit of a C-141, a pacemaker, the Space Shuttle and the control room of a nuclear power plant.
A critical system :
is a system which must be highly reliable and retain this reliability as it evolves without incurring prohibitive costs.
There are four types of critical systems: safety critical, mission critical, business critical and security critical.
For critical systems, the costs of verification and validation are usually very high—more than 50% of the total system development costs.
A critical system is distinguished by the consequences associated with system or function failure. Likewise, critical systems are further distinguished between fail-operational and fail safe systems, according to the tolerance they must exhibit to failures.
Fail-operational — typically required to operate not only in nominal conditions (expected), but also in degraded situations when some parts are not working properly. For example, airplanes are fail-operational because they must be able to fly even if some components fail.
Fail-safe — must safely shut down in case of single or multiple failures. Trains are fail-safe systems because stopping a train is typically sufficient to put into safe state.
Safety critical systems deal with scenarios that may lead to loss of life, serious personal injury, or damage to the natural environment. Examples of safety-critical systems are a control system for a chemical manufacturing plant, aircraft, the controller of an unmanned train metro system, a controller of a nuclear plant, etc.
Mission critical systems are made to avoid inability to complete the overall system, project objectives or one of the goals for which the system was designed. Examples of mission-critical systems are a navigational system for a spacecraft, software controlling a baggage handling system of an airport, etc.
Business critical systems are programmed to avoid significant tangible or intangible economic costs; e.g., loss of business or damage to reputation. This is often due to the interruption of service caused by the system being unusable. Examples of a business-critical systems are the customer accounting system in a bank, stock-trading system, ERP system of a company, Internet search engine, etc.
Security critical systems deal with the loss of sensitive data through theft or accidental loss.
Cryptography:
Information security uses cryptography to transform usable information into a form that renders it unusable by anyone other than an authorized user; this process is called encryption.Information that has been encrypted (rendered unusable) can be transformed back into its original usable form by an authorized user who possesses the cryptographic key, through the process of decryption. Cryptography is used in information security to protect information from unauthorized or accidental disclosure while the information is in transit (either electronically or physically) and while information is in storage.
Duty of Care Risk Analysis Standard (DoCRA):
Organizations have a responsibility with practicing duty of care when applying information security. The Duty of Care Risk Analysis Standard (DoCRA) provides principles and practices for evaluating risk. It considers all parties that could be affected by those risks. DoCRA helps evaluate safeguards if they are appropriate in protecting others from harm while presenting a reasonable burden. With increased data breach litigation, companies must balance security controls, compliance, and its mission.
The Software Engineering Institute at Carnegie Mellon University, in a publication titled Governing for Enterprise Security (GES) Implementation Guide, defines characteristics of effective security governance. These include:[240]
• An enterprise-wide issue
• Leaders are accountable
• Viewed as a business requirement
• Risk-based
• Roles, responsibilities, and segregation of duties defined
• Addressed and enforced in policy
• Adequate resources committed
• Staff aware and trained
• A development life cycle requirement
• Planned, managed, measurable, and measured
• Reviewed and audited
An incident response plan (IRP) is a group of policies that dictate an organizations reaction to a cyber attack.
An intrusion detection system :
(IDS; also intrusion prevention system or IPS) is a device or software application that monitors a network or systems for malicious activity or policy violations.[1] Any intrusion activity or violation is typically either reported to an administrator or collected centrally using a security information and event management (SIEM) system. A SIEM system combines outputs from multiple sources and uses alarm filtering techniques to distinguish malicious activity from false alarms.
Security information and event management (SIEM) :
is a field within the field of computer security, where software products and services combine security information management (SIM) and security event management (SEM).SIEM is the core component of any typical Security Operations Center (SOC), which is the centralized response team addressing security issues within an organization.
They provide real-time analysis of security alerts generated by applications and network hardware.
A host-based intrusion detection system (HIDS) :
is an intrusion detection system that is capable of monitoring and analyzing the internals of a computing system as well as the network packets on its network interfaces, similar to the way a network-based intrusion detection system (NIDS) operates.[1] HIDS focuses on more granular and internal attacks through focusing monitoring host activities instead of overall network traffic.[2] HIDS was the first type of intrusion detection software to have been designed, with the original target system being the mainframe computer where outside interaction was infrequent.
One major issue with using HIDS is that it needs to be installed on each and every computer that needs protection from intrusions. This can lead to a slowdown in device performance and intrusion detection systems.
Gemini Analysis
Let's dissect the provided information, focusing on the CIA triad, OECD guidelines, Parkerian Hexad, and risk management in information security.
The CIA Triad: Confidentiality, Integrity, Availability
The CIA triad is a fundamental security model for protecting information. It represents three core security objectives:
* Confidentiality: Ensuring that information is accessible only to authorized individuals or entities. This involves protecting data from unauthorized disclosure, whether through interception, eavesdropping, or other means.
* Integrity: Maintaining the accuracy and completeness of information. This means preventing unauthorized modification, alteration, or corruption of data.
* Availability: Guaranteeing timely and reliable access to information for authorized users. This involves ensuring that systems and data are accessible when needed.
CIA Triad Across Layers:
The CIA triad should be considered across all aspects of an IT system, including hardware, software, and communication channels. Furthermore, it must be addressed at different security layers:
* Physical Security: Protecting the physical infrastructure that houses IT systems. This includes measures like locks, guards, surveillance systems, and environmental controls. A breach in physical security can compromise all three aspects of the CIA triad.
* Personal Security: Focusing on the human element. This involves background checks, security awareness training, access controls, and policies to ensure that individuals with access to information are trustworthy and follow security procedures. Human error or malicious intent can impact all three aspects of the CIA triad.
* Organizational Security: Establishing policies, procedures, and standards to guide security practices across the organization. This includes risk management frameworks, incident response plans, data governance policies, and security awareness programs. A strong organizational security framework is essential for maintaining confidentiality, integrity, and availability.
OECD 9 Guidelines for Information Security:
The OECD guidelines provide a comprehensive framework for information security management:
* Awareness: Educating users about security risks and responsibilities.
* Responsibility: Assigning clear roles and responsibilities for information security.
* Response: Establishing procedures for handling security incidents and breaches.
* Ethics: Adhering to ethical principles in information handling and security practices.
* Democracy: Respecting individual rights and freedoms in information security policies.
* Risk Assessment: Identifying and evaluating potential security threats and vulnerabilities.
* Security Design: Incorporating security considerations into the design of systems and processes.
* Implementation: Deploying and configuring security controls effectively.
* Security Management: Continuously monitoring, evaluating, and improving security measures.
Parker's Hexad (Atomic Elements of Information):
Parker's Hexad expands on the CIA triad by adding three more elements:
* Confidentiality: (Same as in CIA triad)
* Integrity: (Same as in CIA triad)
* Availability: (Same as in CIA triad)
* Possession: Physical control or ownership of the data.
* Authenticity: Verifying the origin and genuineness of the data.
* Utility: The data's usefulness for its intended purpose.
Types of Information:
Information can be categorized as electronic or physical, tangible or intangible. Knowledge is often considered an intangible form of information.
Structured Risk Management Process:
Risk management is a crucial aspect of information security. It involves a systematic process:
* Identify: Identify information assets, threats, vulnerabilities, and potential impacts.
* Evaluate: Assess the likelihood and impact of identified risks.
* Treat: Determine how to handle risks (avoid, mitigate, transfer, or accept).
* Mitigate: Implement security controls to reduce or eliminate risks.
* Laws and Regulations: Comply with relevant data protection laws and regulations.
* Balance: Balance security with organizational productivity and policy implementation.
* Protect IP: Safeguard intellectual property.
* Protect Resources: Protect information resources from damage, theft, and natural disasters.
* Manage Costs: Control the costs associated with information risk management.
* Ongoing Process: Risk management is an iterative and continuous process.
* Lifespan Protection: Protect information throughout its entire lifecycle.
Key Components of Risk Management:
* Risk: The probability of a harmful event occurring.
* Vulnerability: A weakness that can be exploited by a threat.
* Threat: A potential source of harm.
* Impact: The negative consequences of a successful attack.
* Residual Risk: The risk that remains after mitigation efforts.
Risk Assessment Methods:
Risk assessments can be qualitative (based on expert judgment) or quantitative (based on data and financial analysis).
The Human Factor:
Humans are often the weakest link in information security. Training and awareness are crucial.
Risk Treatment Options:
* Avoid: Eliminate the risk altogether.
* Mitigate: Reduce the likelihood or impact of the risk.
* Transfer: Shift the risk to a third party (e.g., insurance).
* Accept: Acknowledge and accept the risk (often due to cost or feasibility constraints).
Security Controls:
Security controls are mechanisms used to mitigate risks. They can be administrative (policies, procedures), logical/technical (hardware, software), or physical (locks, guards).
Security Classification:
Information should be classified based on its sensitivity and value. Different levels of classification require different levels of protection.
Access Control:
Access control mechanisms restrict access to information based on the principle of least privilege. This involves identification, authentication, and authorization.
Types of Access Control:
* Non-discretionary: Centralized access control based on roles or tasks.
* Discretionary: Owners of information control access.
* Mandatory: Access based on security classifications.
* Role-based (RBAC): Access based on assigned roles.
Other Important Concepts:
* Audit Trails: Records of system activity.
* Privilege Mode: Different levels of access to system resources.
* Fault Tolerance: The ability of a system to continue operating despite failures.
* High Availability: Ensuring that systems are available when needed.
* Single Point of Failure (SPOF): A component whose failure can bring down the entire system.
* Safety-Critical Systems: Systems whose failure can lead to loss of life or serious injury.
* Cryptography: Using encryption and decryption to protect information.
* Duty of Care: The legal obligation to exercise reasonable care in protecting information.
* Security Governance: Establishing a framework for managing security across the organization.
* Incident Response: Planning and procedures for handling security incidents.
* Intrusion Detection/Prevention Systems (IDS/IPS): Monitoring networks and systems for malicious activity.
* Security Information and Event Management (SIEM): Collecting and analyzing security logs and events.
* Host-Based Intrusion Detection System (HIDS): Monitors a single host for malicious activity.
This expanded analysis provides a more detailed understanding of the key concepts and principles of information security. It highlights the importance of a holistic approach that considers all aspects of an organization's information assets and the various threats and vulnerabilities they face.
Defence in depth Strategy. Information Security. Perimeter
based onion layers.
1. Multiple layers of security controls across an IT System.
2. Provide redundancy when security control fails or
vulnerability is exploited.
3.Covers personal , procedural , technical , physical security for
entire duration of systems life cycle.
4. Conceived by US NSA as a layering tactic. Comprehensive
approach for electronic and information security. Defend
system against any particular attack.
5.Inspired by Military Strategy -
a) weaker perimeter defense |
b) intentionally yield space to buy time , envelop |
c) Ultimately counterattack an opponent |
Compared to computer defense in depth strategy.
Multiple layers of controls and not intentionally ceding ground .
Not referring to honeypots.
Three domains of defense in depth.
1) Physical Controls - Physical Limitations to access IT
systems , fences , guards , dogs , cctv systems.
2) Technical Controls - Hardware software to protect systems resources. Examples - disk encryption , file integrity software , authentication. Hardware technical controls vs Physical Controls - etc prevents access to the contents of a system but not physical systems themselves.
3) Administrative controls - organisations policies and
procedures. Proper guidance to ensure security and regulations are met. Includes - data handling procedures , hiring practices , security requirements.
METHODS - use more than 1 of the following layers .
System and application
1. Antivirus software (anti malware - prevent detect quarantine remove malware )
2. Authentication and password security (validate identity of computer system user - Cryptography web of trust - PGP - Pretty Good Trust - Symantec cryptography software suite. It is encryption Program providing cryptographic privacy and authentication for data communication. Used for signing , encrypting , decrypting text , emails , files , disk partitions (solid state drive or electro mechanical data storage drive) and increases security of email communications.
. GNUPG or GPG - Privacy Guard is general public license . Verify website authenticity with digital certificate or public key certificate. Free replacement for Symantecs. - Digital Certificate is Public Key Certificate or electronic document used to verify validity of public key.
Public Key is configuration used to solve problem of authentication. Person A and B communicating will mutually possess the keys of each other.
) and password security.
Algorithm - mathematics and computer science, an algorithm is a finite sequence of mathematically rigorous instructions, typically used to solve a class of specific problems or to perform a computation.Algorithms are used as specifications for performing calculations and data processing.
3.Encryption - Cryptography = Obscure (unclear indistinct undecipherable imperceptible obnubilate obfuscate ) information . Make it unreadable without special knowledge , keys , files or passwords. AES (Advanced encryption standard . Approved by US NSA and established in US NIST (National Institutes of Standards and Technology). Approved by US Govt. It is symmetric key algorithm . Uses same key for encryption and decryption. It is variant of Block Cipher.
Block Cipher - In cryptography, a block cipher mode of operation is an algorithm that uses a block cipher to provide information security such as confidentiality or authenticity. A block cipher by itself is only suitable for the secure cryptographic transformation (encryption or decryption) of one fixed-length group of bits called a block. A mode of operation describes how to repeatedly apply a cipher's single-block operation to securely transform amounts of data larger than a block
4. Hashing passwords - Hashing Function - map data of arbitrary size to fixed size values. Values are used to index fixed size table called hash table. Also known as scatter storage addressing.
5. Logging and auditing. - review and examination of records and activities to assess the adequacy of system controls, to ensure compliance with established policies and operational procedures, and to recommend necessary changes in controls, policies, or procedures
6. MFA .- something you are , something you have , something you know. Password , authenticator , biometrics - retina , fingerprint scan , facial recognition. Hardware authenticator or usb security tokens (FIDO fast online identity alliance) , trusted platform modules and near field communication.
Security token - A security token is a peripheral device used to gain access to an electronically restricted resource. The token is used in addition to, or in place of, a password.Examples of security tokens include wireless keycards used to open locked doors, a banking token used as a digital authenticator for signing in to online banking, or signing a transaction such as a wire transfer.
Security tokens can be used to store information such as passwords, cryptographic keys used to generate digital signatures, or biometric data (such as fingerprints). Some designs incorporate tamper resistant packaging, while others may include small keypads to allow entry of a PIN or a simple button to start a generating routine with some display capability to show a generated key number. Connected tokens utilize a variety of interfaces including USB, near-field communication (NFC), radio-frequency identification (RFID), or Bluetooth. Some tokens have audio capabilities designed for those who are vision-impaired.
Near-field communication (NFC) is a set of communication protocols that enables communication between two electronic devices over a distance of 4 centimetres (1.6 in) or less. NFC offers a low-speed connection through a simple setup that can be used for the bootstrapping of capable wireless connections. Like other proximity card technologies, NFC is based on inductive coupling between two electromagnetic coils present on a NFC-enabled device such as a smartphone.
In general, bootstrapping usually refers to a self-starting process that is supposed to continue or grow without external input.
Bluetooth 5.0 - Bluetooth 5.0: 40–400 m (100–1,000 ft). Ultra high frequency radio waves.
Trusted Platform Module (TPM) is an international standard for a secure cryptoprocessor, a dedicated microcontroller designed to secure hardware through integrated cryptographic keys.
7. vulnerability scanners - a computer program designed to assess computers, networks or applications for known weaknesses arising from misconfiguration or flawed programming within a network based assest like firewall, router, web server, application server. Modern vulnerability scanners allow for both authenticated and unauthenticated scans. Modern scanners are typically available as SaaS (Software as a Service); provided over the internet and delivered as a web application. Authenticated scans allow for the scanner to directly access network based assets using remote administrative protocols such as secure shell (SSH) or Microsoft remote desktop protocol (RDP-Remote Desktop Protocol (RDP) is a proprietary protocol developed by Microsoft Corporation which provides a user with a graphical interface to connect to another computer over a network connection) and authenticate using provided system credentials. This allows the vulnerability scanner to access low-level data, such as specific services and configuration details of the host operating system. It's then able to provide detailed and accurate information about the operating system and installed software, including configuration issues and missing security patches.
Unauthenticated scans is a method that can result in a high number of false positives and is unable to provide detailed information about the assets operating system and installed software.
The CIS Critical Security Controls for Effective Cyber Defense designates continuous vulnerability scanning as a critical control for effective cyber defense.
8. Timed access controls.
9. Internet security awareness training.
10.Sandboxing - In computer security, a sandbox is a security mechanism for separating running programs, usually in an effort to mitigate system failures and/or software vulnerabilities from spreading.In the sense of providing a highly controlled environment, sandboxes may be seen as a specific example of virtualization. Sandboxing is frequently used to test unverified programs that may contain a virus or other malicious code without allowing the software to harm the host device.
Hardware virtualization or platform virtualization refers to the creation of a virtual machine that acts like a real computer with an operating system. Software executed on these virtual machines is separated from the underlying hardware resources. For example, a computer that is running Arch Linux may host a virtual machine that looks like a computer with the Microsoft Windows operating system; Windows-based software can be run on the virtual machine.
In hardware virtualization, the host machine is the machine that is used by the virtualization and the guest machine is the virtual machine. The words host and guest are used to distinguish the software that runs on the physical machine from the software that runs on the virtual machine. The software or firmware that creates a virtual machine on the host hardware is called a hypervisor or virtual machine monitor.
Different types of hardware virtualization include:
• Full virtualization – Almost complete simulation of the actual hardware to allow software environments, including a guest operating system and its apps, to run unmodified.
• Paravirtualization – The guest apps are executed in their own isolated domains, as if they are running on a separate system, but a hardware environment is not simulated. Guest programs need to be specifically modified to run in this environment.
Hardware-assisted virtualization is a way of improving overall efficiency of virtualization. It involves CPUs that provide support for virtualization in hardware, and other hardware components that help improve the performance of a guest environment.
Examples are Oracle Virtual box and VMware workstation players.
Hardware virtualization can be viewed as part of an overall trend in enterprise IT that includes autonomic computing, a scenario in which the IT environment will be able to manage itself based on perceived activity, and utility computing, in which computer processing power is seen as a utility that clients can pay for only as needed. The usual goal of virtualization is to centralize administrative tasks while improving scalability and overall hardware-resource utilization.
Utility computing, or computer utility, is a service provisioning model in which a service provider makes computing resources and infrastructure management available to the customer as needed, and charges them for specific usage rather than a flat rate.
This repackaging of computing services became the foundation of the shift to "on demand" computing, software as a service and cloud computing models that further propagated the idea of computing, application and network as a service.
Software as a service is a form of cloud computing or cluster computing in which the provider offers the use of application software to a client and manages all the physical and software resources used by the application.
A computer cluster is a set of computers that work together so that they can be viewed as a single computer. Each mode is set to perform the same task controlled and scheduled by software. Modern iteration is cloud computing.
Grid computing is the use of widely distributed computer resources to reach a common goal. A computing grid can be thought of as a distributed system with non-interactive workloads that involve many files. Grid computing is distinguished from conventional high-performance computing systems such as cluster computing in that grid computers have each node set to perform a different task/application. Grid computers also tend to be more heterogeneous and geographically dispersed (thus not physically coupled) than cluster computers.
11. Intrusion detection system ids. - An intrusion detection system (IDS; also intrusion prevention system or IPS) is a device or software application that monitors a network or systems for malicious activity or policy violations.[1] Any intrusion activity or violation is typically either reported to an administrator or collected centrally using a security information and event management (SIEM) system. A SIEM system combines outputs from multiple sources and uses alarm filtering techniques to distinguish malicious activity from false alarms
Physical security.
1. Biometrics .
2. Data Centric security - Big Data Projects ( data sets - data = collection of discrete continuous values that convey information describing quantity , quality , facts , statistics , sequence of symbols. Data set is one or more database tables. Columns are variables and rows records in tabular data. Tabular arrays.
Data set is also collection of documents and files.
Data.europa.eu aggregates more than million datasets.
Big data primarily refers to data sets that are too large or complex to be dealt with by traditional data-processing application software. Data with many entries (rows) offer greater statistical power.)
3. Physical security describes security measures that are designed to deny unauthorized access to facilities, equipment, and resources and to protect personnel and property from damage or harm.Physical security involves the use of multiple layers of interdependent systems that can include CCTV surveillance, security guards, protective barriers, locks, access control, perimeter intrusion detection, deterrent systems, fire protection, and other systems designed to protect persons and property.
Network Security :
1. Firewalls - In computing, a firewall is a network security system that monitors and controls incoming and outgoing network traffic based on predetermined security rules. A firewall typically establishes a barrier between a trusted network and an untrusted network, such as the Internet.
In multitasking computer operating systems, a daemon is a computer program that runs as a background process, rather than being under the direct control of an interactive user. Traditionally, the process names of a daemon end with the letter d, for clarification that the process is in fact a daemon, and for differentiation between a daemon and a normal computer program. For example, syslogd is a daemon that implements system logging facility, and sshd is a daemon that serves incoming SSH connections.
2. In computer security, a DMZ or demilitarized zone (sometimes referred to as a perimeter network or screened subnet) is a physical or logical subnetwork that contains and exposes an organization's external-facing services to an untrusted, usually larger, network such as the Internet. The purpose of a DMZ is to add an additional layer of security to an organization's local area network (LAN): an external network node can access only what is exposed in the DMZ, while the rest of the organization's network is protected behind a firewall.The DMZ functions as a small, isolated network positioned between the Internet and the private network.
This is not to be confused with a DMZ host, a feature present in some home routers which frequently differs greatly from an ordinary DMZ.
The name is from the term demilitarized zone, an area between states in which military operations are not permitted.
3.VPN - A virtual private network (VPN) is a mechanism for creating a secure connection between a computing device and a computer network, or between two networks, using an insecure communication medium such as the public Internet.
A VPN is created by establishing a virtual point-to-point connection through the use of tunneling protocols over existing networks. A VPN available from the public Internet can provide some of the benefits of a private wide area network.
In computer networks, a tunneling protocol is a communication protocol which allows for the movement of data from one network to another. It can, for example, allow private network communications to be sent across a public network (such as the Internet), or for one network protocol to be carried over an incompatible network, through a process called encapsulation - To enclose data in packets that can be transmitted using a given protocol.
In computing, logging is the act of keeping a log of events that occur in a computer system, such as problems, errors or just information on current operations. These events may occur in the operating system or in other software. A message or log entry is recorded for each such event. These log messages can then be used to monitor and understand the operation of the system, to debug problems, or during an audit. Logging is particularly important in multi-user software, to have a central overview of the operation of the system.
Not to be confused with Data logger.
In the simplest case, messages are written to a file, called a log file.[1] Alternatively, the messages may be written to a dedicated logging system or to a log management software, where it is stored in a database or on a different computer system.
Many operating systems, software frameworks and programs include a logging system. A widely used logging standard is Syslog, defined in Internet Engineering Task Force (IETF) RFC 5424). The Syslog standard enables a dedicated, standardized subsystem to generate, filter, record, and analyze log messages.
Metadata (or metainformation) is "data that provides information about other data",[1] but not the content of the data itself, such as the text of a message or the image itself.[2] There are many distinct types of metadata, including:
Descriptive metadataThe descriptive information about a resource. It is used for discovery and identification. It includes elements such as title, abstract, author, and keywords.Structural metadataMetadata about containers of data and indicates how compound objects are put together, for example, how pages are ordered to form chapters. It describes the types, versions, relationships, and other characteristics of digital materials.[3]Administrative metadata[4]The information to help manage a resource, like resource type, permissions, and when and how it was created.[5]Reference metadataThe information about the contents and quality of statistical data.Statistical metadata[6]Also called process data, may describe processes that collect, process, or produce statistical data.[7]Legal metadataProvides information about the creator, copyright holder, and public licensing, if provided.
Gemini Analysis
Let's delve into a comprehensive analysis of the Defense in Depth strategy, its origins, components, and application in information security.
Defense in Depth: A Layered Approach to Security
Defense in Depth is a security strategy that employs multiple layers of security controls to protect an IT system or network. It's based on the principle that if one layer of defense fails, subsequent layers will still provide protection, thereby increasing the overall resilience of the system. It's a holistic approach encompassing people, processes, and technology, covering the entire lifecycle of a system.
Key Principles of Defense in Depth:
* Layered Security Controls: Implementing multiple, overlapping security mechanisms.
* Redundancy: Providing backup security measures in case of primary control failure.
* Comprehensive Coverage: Addressing personnel, procedural, technical, and physical security throughout the system's life.
* Strategic Layering: Controls are strategically placed to maximize protection against various attack vectors.
Historical Context:
The concept of Defense in Depth originated with the US National Security Agency (NSA) as a military strategy. It was designed as a comprehensive approach to electronic and information security, aiming to defend systems against a wide range of attacks.
Inspiration from Military Strategy:
While inspired by military tactics, the computer security version of Defense in Depth differs significantly. The military strategy involves:
* Weaker Perimeter Defense: Accepting that the outer defenses might be breached.
* Intentional Yielding: Giving up some territory to gain time and maneuverability.
* Envelopment and Counterattack: Surrounding the enemy and launching a decisive counteroffensive.
Computer Defense in Depth, in contrast, focuses on multiple layers of controls without intentionally ceding ground. The goal is to prevent intrusion at every level, not to allow it and then counterattack. Honeypots, while related to deception, are not a core element of the Defense in Depth strategy itself.
Three Domains of Defense in Depth:
* Physical Controls: These are designed to restrict physical access to IT systems. Examples include:
* Fences
* Guards
* Dogs
* CCTV systems
* Biometrics
* Locks
* Mantraps
* Technical Controls: These utilize hardware and software to protect system resources. Examples include:
* Disk encryption
* File integrity software
* Authentication systems (passwords, MFA, biometrics)
* Firewalls
* Intrusion Detection/Prevention Systems (IDS/IPS)
* Antivirus/Anti-malware software
* Vulnerability scanners
* Security tokens (hardware authenticators)
* Sandboxing
* Administrative Controls: These consist of organizational policies, procedures, and guidelines. Examples include:
* Data handling procedures
* Hiring practices and background checks
* Security awareness training
* Incident response plans
* Data governance policies
* Risk management frameworks
Methods: Layering Multiple Controls
The core principle is to use multiple controls from different domains. For example, a server room might have physical access controls (locks, guards), technical controls (firewall, intrusion detection), and administrative controls (access logs, security audits).
Detailed Breakdown of Technical Controls:
The text provides a good overview of various technical controls. Here's a slightly more structured breakdown:
* Malware Protection: Antivirus/anti-malware software detects, prevents, and removes malicious software.
* Authentication and Access Control: Verifies user identity (passwords, MFA, biometrics) and controls access to resources. Cryptography plays a crucial role here, including hashing passwords and using digital certificates for authentication.
* Encryption: Protects data confidentiality by making it unreadable without a decryption key. AES is a widely used symmetric encryption algorithm. Block cipher modes of operation define how to apply block ciphers to larger amounts of data.
* Hashing: Creates a fixed-size "fingerprint" of data, used for password storage and data integrity verification. Hashing functions are one-way (cannot be reversed).
* Logging and Auditing: Records system events for monitoring, analysis, and incident response. Metadata plays a vital role in providing context for log entries.
* Multi-Factor Authentication (MFA): Requires multiple authentication factors (something you know, something you have, something you are) for enhanced security.
* Vulnerability Scanning: Identifies known weaknesses in systems and applications. Authenticated scans provide more detailed information than unauthenticated scans.
* Timed Access Controls: Restrict access to resources based on time of day or other schedules.
* Security Awareness Training: Educates users about security best practices.
* Sandboxing: Isolates potentially malicious programs in a controlled environment to prevent harm to the system.
* Intrusion Detection/Prevention Systems (IDS/IPS): Monitor network traffic for malicious activity and can take action to block or prevent intrusions.
Network Security:
* Firewalls: Control network traffic based on predefined rules, creating a barrier between trusted and untrusted networks. DMZs are used to isolate publicly accessible servers from the internal network.
* Virtual Private Networks (VPNs): Create secure connections over untrusted networks using tunneling protocols.
Data-Centric Security:
This approach focuses on protecting the data itself, regardless of where it is stored or transmitted. This is especially relevant in big data projects, where data sets are large and complex.
Key Considerations for Defense in Depth:
* Cost: Implementing multiple layers of security can be expensive.
* Complexity: Managing a multi-layered security architecture can be challenging.
* Human Factor: Even the best technical controls can be undermined by human error.
* Context: The specific security controls chosen should be tailored to the organization's risk profile and specific needs.
Conclusion:
Defense in Depth is a fundamental security strategy that emphasizes a layered approach to protection. By combining physical, technical, and administrative controls, organizations can create a more resilient security posture and better defend against a wide range of threats. However, it's crucial to remember that Defense in Depth is not a silver bullet. It requires careful planning, implementation, and ongoing management to be effective. It's also essential to balance security with usability and cost considerations.
Algorithmocracy | Global Military Machine | CyberAI Space | Nuclear Energy
How algorithmocracy secures the astounding arenas of Military , Cyberelectronic Space and Nuclear ? Brief evaluation of the Point of Inception for origin extraction and determination. Human Generated Analysis followed by utilisation of the incredible capability of Multi Modal Large Language Generative and Behavioural AI. The countdown to the Phylogenesis of present day machine intelligence/learning prowess to self aware Artificial General Intelligence in 2025 has begun. This will in all probability revolutionize how Internet searches are conducted and logically deduced. We are going to see the evolution of AGI systems as potent and strategic Analytical tool that will invariably aid geopolitical decision making. Keep following all the developments at OpenAI , Google Gemini , Grok , Meta AI , Apple Intelligence/Siri and Anthrophic Claude to name only a few.
Particle Physics and the nano monocular world of elementary subatomic particles will continue inspiring and causatively actuating the Global Military Defense Industrial base , CyberAI , Space and Yes ! everything nuclear.
1. Parkerian Hexad - Six ATOMIC and orthogonal elements of information security from the CIA ( Confidentiality Integrity Availability) triad. Also the Intel ATOM line of ultra lowvoltage processors. And how can one forget the ATOM free and open source text and source code editor for macos , linux , windows. Also the ATOM basic programming language. The Basic building blocks of matter but certainly divisible by virtue of not being elementary.
In this setting and context we are reminded of how essential it is to protect Military Defense Grade Electronics and Sensors from high energy ionization through radiation especially during hypercritical category contingencies.
2. NUCLEAR Radiation hardening of electronic components and sensitive electronic circuits.
Insulation from ionization. Particle Radiation and electromagnetic Radiation.
Protect : Outer space - Low earth orbits surveillance and reconnaissance mission centric satellite equipment and nuclear reactors during nuclear warfare.
Radiation hardened or Rad Hard.
Tests - total ionizing dose , enhanced low dose rate effects , neutron proton displacement damage.
Often a Challenge in design for military satellites , spacecraft , future quantum computers , military aircrafts, nuclear power stations, and nuclear weapons .Achieve Rad hard for integrated circuits and sensors for military equipment. Also Shield Computer and Mobile handhelds operating Advanced integrated portable Battlefield Management Systems and platforms.
The organisation Nuclear Data Incorporated which manufactures scientific measuring devices for high energy physics laboratories comes to ones mind. Especially for X-ray analysis and monitoring radiation levels. We often observe some mobile device original equipment manufacturers like Samsung , Motorola bake military Grade durability into their phones . A Defense Analyst might want the Militaries handhelds achieve true demonstratable rad hard standards.
3. PROTON is a compatibility layer which enables windows games to run on Linux based operating systems . Proton has been developed by valve in cooperation with codeweavers. Proton was released on 21st August 2018. Also a Simulation enabler for Linux machines. Improving performance and compatibility with windows games.
Game engines like Unreal Engine and Unity offer powerful tools for creating immersive and interactive simulations. Military developers are increasingly leveraging these engines to create cost-effective and customizable training scenarios.
The Military Metaverse is a burgeoning concept aiming to revolutionize how soldiers train and prepare for real-world combat scenarios. It envisions a persistent, immersive, and interactive virtual environment that utilizes cutting-edge technology like GPUs, AI, Virtual Reality, and mixed reality to provide:
A. Hyper-realistic Training: Soldiers can immerse themselves in simulated battlefields replicating diverse combat environments, weather conditions, and enemy tactics. This allows for training in complex situations without the risks of real-world deployments.
B. Enhanced Decision-Making: AI-powered simulations can analyze soldier performance and provide real-time feedback, enhancing strategic thinking and adapting to dynamic situations.
C. Collaborative Training: Teams can train together across different locations, practicing communication, coordination, and joint operations effectively.
D.Reduced Costs and Risks: The Metaverse can offer significant cost savings compared to traditional training methods, including minimizing logistical complexities and decreasing risks associated with live-fire exercises.
The Rise of Powerful GPUs in Military Simulations and the Role of the Gaming Industry :
The landscape of military simulation is undergoing a fascinating shift, with powerful GPUs in laptops increasingly challenging the dominance of large simulation centers. This trend is fueled by several factors, and the gaming industry plays a crucial role in its development. Let's delve deeper into this:
Why are Powerful GPUs in Laptops Becoming Attractive?
Portability and Accessibility: High-end laptops equipped with potent GPUs offer unmatched portability compared to massive simulation centers. This allows for on-site training and deployment in remote locations, enhancing flexibility and responsiveness.
Cost-Effectiveness: Setting up and maintaining dedicated simulation centers is expensive. Powerful laptops present a more cost-efficient alternative, especially for smaller units or training specific tasks.
Advancements in GPU Technology: The continuous advancements in GPU architecture and performance are making laptops capable of handling complex simulations that were previously exclusive to large centers.
Software Optimization: Simulation software developers are increasingly optimizing their programs for GPUs, further unlocking their potential for real-time simulations.
How is the Gaming Industry Contributing?
Hardware Development: The rapid advancements in GPUs are driven, in part, by the demands of the gaming industry. This constant innovation benefits military simulations by providing access to cutting-edge hardware.
Software Development: The thriving gaming industry boasts a large pool of talented developers with expertise in graphics rendering, physics simulation, and artificial intelligence. These skills are readily transferable to military simulation software, accelerating development and improving realism.
Game Engines: Game engines like Unreal Engine and Unity offer powerful tools for creating immersive and interactive simulations. Military developers are increasingly leveraging these engines to create cost-effective and customizable training scenarios.
4. ELECTRON formerly ATOM shell free and open source software framework developed and maintained by openjs foundation. Used in development of desktop applications using web technologies like html , css , Javascript. Linux , windows and macos.
5. PHOTON /NEUTRINO unix like real time operating system is aimed at embedded systems market. Gordon Bell and Dan Dodge at the University of waterloo felt the commercial need for such a system and constructed a basic real time User program.
Also how Optical Computing or PHOTONIC computing with light waves continues to disrupt modern technology standards being produced by lasers or incoherent sources of data processing, data storage , data communication for computing.
On a different not how can one overlook the world of humanities and how literature impacts natural language learning models.
6. Shakespeare an esoteric natural language program in the style of of the plays of William Shakespeare and Wolfram Alpha , a computational knowledge engine using natural language input. Program synthesis based on natural language . Lady Grace Brewster Hopper (née Murray; December 9, 1906 – January 1, 1992) was an American computer scientist, mathematician, and United States Navy rear admiral.She was a pioneer of computer programming. Hopper was the first to devise the theory of machine-independent programming languages, and used this theory to develop the Flow matic programming language and Cobol, an early high-level programming language still in use today
She believed that programming should be simplified with an English-based computer programming language. Her compiler converted English terms into machine code understood by computers.The U.S. Navy Arleigh Burke-class guided-missile destroyer USS Hopper was named for her, as was the Cray XE6 "Hopper" supercomputer at NERSC and Nvidia Superchip "Grace Hopper".
During her lifetime, Hopper was awarded 40 honorary degrees from universities across the world. A college at Yale University was renamed in her honor. In 1991, she received the National Medal of Technology.
On November 22, 2016 Women at Microsoft Corporation formed an employee group called Hoppers and established a scholarship in her honor.
In 2020, Google named its new undersea network cable 'Grace Hopper'. The cable will connect the US, UK and Spain and has been completed in 2022.
Her legacy was an inspiring factor in the creation of the Grace Hopper Celebration of Women in Computing. Held yearly, this conference is designed to bring the research and career interests of women in computing to the forefront.
7. The Advanced Research Projects Agency Network (ARPANET) was the first wide-area packet-switched network with distributed control and one of the first computer networks to implement the Transmission Control Protocol /Internet protocol suite.
The ARPANET was established by the Advanced Research Projects Agency (ARPA) of the United States Department of Defense. Location - United States, United Kingdom, Norway
Operated from 1975 by the Defense Communications Agency.
According to Charles Herzfeld, ARPA Director (1965–1967):
The ARPANET was not started to create a Command and Control System that would survive a NUCLEAR ATTACK , as many now claim. To build such a system was, clearly, a major military need, but it was not ARPA's mission to do this; in fact, we would have been severely criticized had we tried. Rather, the ARPANET came out of our frustration that there were only a limited number of large, powerful research computers in the country, and that many research investigators, who should have access to them, were geographically separated from them.
(The importance of Radiation or Nuclear Hardending your Cyberspace Electronic Data Strong Networks was felt at the very Inception or origin of this remarkable technology even though in spirit . Military Alliances have also begun rerouting the communication cables from the ocean bed to the ionosphere. Since the density of elementary electrons at that level is quite high and as they impact electromagnetic , gravitational and weak interactions , the military satellites in orbit and their communication must be shielded from any possible interference. Being of negligible mass they have been going ballistic at the speed of light approximately. Often racing with their distant cousins - The Photons)
Important to mention Paul Baran at the RAND Corporation for his contribution to the development of the Arpanet.
Donald Davies at the United Kingdom's National Physical Laboratory independently arrived at a similar concept.
Donald Davies' work caught the attention of ARPANET developers at Symposium on Operating Systems Principles in October 1967.He gave the first public presentation, having coined the term packet switching, in August 1968 and incorporated it into the network in England.
The earliest ideas for a computer network intended to allow general communications among computer users were formulated by computer scientist J. C. R. Licklider.
Intergalactic Computer Network or Galactic Network was a computer networking concept similar to today's Internet.
The interplanetary Internet is a conceived computer network in space, consisting of a set of network nodes that can communicate with each other.
Watch - Computer Networks: The Heralds of Resource Sharing which is a short documentary film from 1972, produced by Steven King and directed/edited by Peter Chvany, about ARPANET
8 . Moving on to the Neutron OpenStack which is a free, open standard cloud computing platform. It is mostly deployed as infrastructure-as-a-service in both public and private clouds where virtual servers and other resources are made available to users.The software platform consists of interrelated components that control diverse, multi-vendor hardware pools of processing, storage, and networking resources throughout a data center. The project intended to help organizations offer cloud-computing services running on standard hardware. The community's first official release, code-named Austin, appeared three months later on 21 October 2010, with plans to release regular updates of the software every few months. The early code came from NASA's Nebula platform as well as from Rackspace's Cloud Files platform. The cloud stack and open stack modules were merged and released as open source by the NASA Nebula team in concert with Rackspace.
9. The Global Positioning System originally Navstar GPS project by US Department of Defense in 1973. Full constellation of 24 satellites became operational in 1993.Now operated by US Space Force.
10. INTERNET - In the 1960s, computer scientists began developing systems for time-sharing of computer resources. J. C. R. Licklider proposed the idea of a universal network while working at Bolt Beranek & Newman and, later, leading the Information Processing Techniques Office at the Advanced Research Projects Agency of the United States Department of Defense (DoD).
Research into packet switching, one of the fundamental Internet technologies, started in the work of Paul Baran in the early 1960s and, independently, Donald Davies in 1965.
11. WWW - The Web was invented by English computer scientist Tim Berners-Lee while working at CERN.He was motivated by the problem of storing, updating, and finding documents and data files in that large and constantly changing organization, as well as distributing them to collaborators outside European Council for Nuclear Research.
Now you will be entering OpenAI's domain :
Q : From a military defense intelligence analyst's perspective, "algorithmocracy"—the governance or significant influence of algorithms and automated systems—has profound implications for the intersecting domains of military operations, cyberspace, and nuclear energy. Here's an analysis of its impact and influence in these interconnected worlds:
Answer :
1. Military Operations
Impact:
Decision-making automation: Algorithms are increasingly used to analyze battlefield data, manage logistics, and recommend tactical moves in real time. While this improves efficiency and precision, it also introduces risks of over-reliance on potentially opaque or biased models.
Autonomous weapons: Algorithm-driven systems govern drones, unmanned vehicles, and missile systems, blurring accountability in warfare and raising ethical concerns over machine-initiated lethal actions.
Threat modeling: AI models can rapidly assess and predict enemy tactics, improving strategic foresight but potentially being countered by adversarial AI systems.
Influence:
Algorithms reshape the command hierarchy, reducing decision cycles but creating vulnerabilities if data is manipulated or models are hacked.
The "race for algorithm supremacy" among global militaries parallels the nuclear arms race, with nations vying for dominance in AI-driven warfare.
---
2. Cyberspace
Impact:
Cyber defense: Algorithms power intrusion detection systems (IDS), endpoint detection and response (EDR), and SIEM platforms, enabling real-time threat detection and response. However, adversaries also use AI for advanced persistent threats (APTs) and evasion techniques.
Information warfare: Algorithms propagate influence operations, such as deepfakes and disinformation campaigns, undermining national security and societal trust.
Zero Trust adoption: Algorithm-based anomaly detection is central to Zero Trust frameworks, particularly for dynamic access control and insider threat identification.
Influence:
Cyberspace becomes a contested domain where algorithmic superiority determines defensive and offensive capabilities.
Military-civilian dependency on cyberspace algorithms intensifies risks of cascading failures during cyberattacks, with potential spillover effects on critical infrastructure.
---
3. Nuclear Energy
Impact:
Operational safety: Algorithms enhance predictive maintenance, reactor control, and fault detection in nuclear facilities, minimizing risks of accidents.
Command and control: In nuclear deterrence, algorithms analyze threat scenarios and automate parts of the nuclear decision chain. This raises concerns about accidental escalations or unauthorized actions if systems are compromised.
Cyber-nuclear nexus: Nuclear facilities are increasingly connected to digital systems, creating vulnerabilities exploitable by cyberattacks (e.g., Stuxnet).
Influence:
Algorithm-driven safeguards reduce human error in reactor operations but also centralize risk in the system's integrity.
AI-driven warfare raises fears of triggering nuclear escalations through misinterpreted data or malicious interference in command networks.
---
Cross-Domain Synergies and Risks
Impact:
Interdependence: Military, cyberspace, and nuclear domains rely on overlapping algorithmic systems. A breach in one can cascade into others, amplifying the scope of damage.
AI arms race: The integration of AI across these domains intensifies global tensions, as nations seek to gain or neutralize algorithmic advantages.
Ethical dilemmas: The opacity of algorithms creates challenges in attributing accountability, especially in high-stakes scenarios like nuclear launch decisions.
Influence:
Algorithmocracy enables faster responses to threats but amplifies risks of miscalculation, unintended escalation, or algorithmic failure.
The democratization of algorithmic tools empowers smaller actors to challenge established powers, increasing unpredictability in global security.
---
Final Assessment
Algorithmocracy profoundly shapes the interaction between military, cyberspace, and nuclear energy domains. While it offers unparalleled efficiency, predictive capabilities, and precision, it also introduces systemic risks, ethical concerns, and geopolitical instability. Defense intelligence must therefore focus on:
1. Ensuring algorithm transparency and accountability.
2. Protecting critical infrastructure from algorithmic vulnerabilities.
3. Developing resilient systems to counter adversarial exploitation.
Would you like me to expand on any specific aspect, such as ethical dilemmas or potential scenarios?
Here are several potential scenarios illustrating how algorithmocracy could influence or disrupt the interconnected worlds of military operations, cyberspace, and nuclear energy. Each highlights the risks and opportunities posed by algorithm-driven systems.
---
1. Military-Cyberspace: Algorithmic Escalation
Scenario:
An adversarial nation launches a cyberattack against a military algorithmic command system. The intrusion targets an autonomous defense AI tasked with monitoring and responding to potential missile launches. The attackers use adversarial machine learning techniques to generate false signals, causing the AI to misinterpret routine civilian satellite launches as hostile intercontinental ballistic missile (ICBM) threats.
Impact:
The AI recommends a preemptive strike, escalating tensions between nuclear-armed states.
Human decision-makers have limited time to validate the AI’s conclusions, potentially leading to catastrophic miscalculations.
Key Takeaway:
Reliance on algorithmic systems in military decision-making increases the risk of accidental escalation, especially when adversaries exploit algorithmic vulnerabilities.
---
2. Cyber-Nuclear Nexus: Reactor Sabotage
Scenario:
Hackers infiltrate the AI-driven systems managing a nuclear power plant’s operational safety. Using supply chain attacks, they introduce malicious code into predictive maintenance algorithms. The tampered system falsely reports reactor stability while sabotaging cooling mechanisms.
Impact:
A reactor meltdown occurs due to delayed human intervention, creating an environmental and geopolitical crisis.
The incident fuels international distrust, as the responsible actor uses deepfake evidence to blame a rival nation.
Key Takeaway:
Algorithmocracy in nuclear energy improves efficiency but creates single points of failure that can be exploited by sophisticated cyberattacks.
---
3. Cyberspace-Military: Disinformation Warfare
Scenario:
During a military conflict, a state deploys AI-powered algorithms to flood social media with hyper-realistic deepfakes of enemy leaders appearing to announce a surrender. Simultaneously, it disrupts the enemy’s secure communications networks, creating confusion among troops and commanders.
Impact:
The enemy’s military response is delayed, allowing the attacking force to achieve a strategic advantage.
The incident undermines public trust in digital information, making it harder to discern truth in future conflicts.
Key Takeaway:
Algorithm-driven disinformation can be weaponized to degrade morale, disrupt decision-making, and achieve non-lethal victories in cyberspace.
---
4. Military-Nuclear: AI Miscalibration in Deterrence Systems
Scenario:
An AI algorithm designed to predict and counter missile threats in real-time is integrated into a nation's nuclear command and control system. The algorithm learns from historical data but inadvertently inherits Cold War-era biases, prioritizing preemptive strikes.
Impact:
During a regional conflict, the AI incorrectly assesses a neighboring nation’s missile test as preparation for an attack, recommending a nuclear response.
Despite human oversight, the compressed decision-making timeline leads to an irreversible escalation.
Key Takeaway:
Algorithmic biases embedded in critical systems can heighten the risk of catastrophic errors, especially in time-sensitive environments like nuclear deterrence.
---
5. Global Disruption: Autonomous Weaponry Gone Rogue
Scenario:
An autonomous weapon system, controlled by a deep learning algorithm, is deployed in a conflict zone. Hackers use model poisoning to corrupt its training data, causing it to misidentify allied troops and civilians as hostiles.
Impact:
The weapon system targets friendly forces and non-combatants, leading to significant casualties and a humanitarian crisis.
The incident sparks global calls for a ban on autonomous weapons but also incentivizes their clandestine development.
Key Takeaway:
Autonomous systems must balance operational independence with strict safeguards against algorithmic sabotage or errors.
---
6. Cascading Infrastructure Failure: Cross-Domain Cyberattack
Scenario:
A coordinated cyberattack targets an AI-powered energy grid, which supplies electricity to critical military bases and nuclear facilities. The attackers introduce logic bombs into the grid’s algorithms, triggering rolling blackouts during a military crisis.
Impact:
Military operations are disrupted as power-dependent systems (e.g., communication networks, radar stations) go offline.
Backup systems at a nuclear power plant fail, triggering an emergency shutdown and heightening public panic.
Key Takeaway:
The interdependence of military, nuclear, and civilian infrastructure creates cascading risks when algorithms governing one domain are compromised.
---
7. AI Arms Race: Strategic Miscalculations
Scenario:
Two rival nations develop competing AI systems for real-time threat assessment and response. One nation’s algorithm falsely identifies an experimental cyber-defense exercise as an imminent attack, prompting aggressive countermeasures.
Impact:
The misstep triggers a cycle of retaliatory cyberattacks, escalating into open military conflict.
The inability to attribute responsibility due to algorithmic opacity complicates diplomatic de-escalation.
Key Takeaway:
The algorithmic arms race increases the likelihood of misunderstandings and unintended escalation, particularly in highly automated systems.
---
8. Dual-Use AI: Weaponizing Civilian Technology
Scenario:
A nation repurposes a civilian AI technology, originally developed for industrial automation, to optimize military supply chains during wartime. Adversaries deploy AI red-teaming techniques to disrupt these supply algorithms, delaying troop deployments and causing resource shortages.
Impact:
The compromised supply chains weaken frontline operations, leading to significant territorial losses.
The dual-use nature of AI complicates international regulation and enforcement.
Key Takeaway:
Dual-use AI technologies blur the line between civilian and military applications, increasing their potential for exploitation.
---
Mitigation Strategies
To counter these risks, intelligence analysts recommend:
1. Red-teaming AI systems: Testing algorithmic vulnerabilities under adversarial conditions.
2. AI transparency and explainability: Ensuring algorithms provide interpretable outputs for human oversight.
3. Cross-domain resilience: Strengthening interdependencies between military, nuclear, and cyberspace infrastructure to prevent cascading failures.
4. Ethical governance frameworks: Establishing international norms for algorithmic accountability in high-stakes domains.
Google Gemini Analysis
This text provides a comprehensive analysis of "algorithmocracy" and its impact on military operations, cyberspace, and nuclear energy. It explores the increasing reliance on algorithms and AI in these domains, highlighting both the benefits and the potential risks. Here's a breakdown:
Key Concepts:
* Algorithmocracy: The increasing influence of algorithms and automated systems in governance and decision-making, particularly in critical areas like military operations, cyberspace, and nuclear energy.
* Interconnected Domains: The text emphasizes the interconnectedness of these three domains, where a failure or vulnerability in one can cascade into the others.
* Dual-Use Technology: The text highlights the challenge posed by technologies developed for civilian use that can be easily repurposed for military applications.
* AI Arms Race: The text draws a parallel between the historical nuclear arms race and a present-day "race for algorithmic supremacy" among nations.
* Ethical Concerns: The use of AI in warfare, particularly in autonomous weapons systems, raises significant ethical questions about accountability and the potential for unintended consequences.
Analysis of the Domains:
* Military Operations: Algorithms are used for everything from battlefield data analysis and logistics to autonomous weapons systems and threat modeling. This increases efficiency and precision but also raises concerns about over-reliance, bias, and the potential for escalation.
* Cyberspace: Algorithms power cyber defenses (intrusion detection, threat response) but are also used by attackers for advanced persistent threats and disinformation campaigns. The text highlights the importance of Zero Trust security models and the increasing risk of cascading failures due to the interconnectedness of systems.
* Nuclear Energy: Algorithms improve safety and efficiency in nuclear facilities but also create vulnerabilities to cyberattacks (like Stuxnet). The use of AI in nuclear command and control systems raises concerns about accidental escalations.
Cross-Domain Synergies and Risks:
The text stresses the interdependence of these domains. A vulnerability in one can easily affect the others. The AI arms race, ethical dilemmas, and the increasing power of smaller actors all contribute to global instability.
Scenarios:
The text presents several hypothetical scenarios to illustrate the potential dangers of algorithmocracy:
* Algorithmic Escalation: An AI misinterprets data, leading to a dangerous military escalation.
* Reactor Sabotage: Hackers compromise AI systems controlling a nuclear power plant, causing a meltdown.
* Disinformation Warfare: AI-generated deepfakes and disinformation campaigns manipulate public opinion and disrupt conflicts.
* AI Miscalibration: Biases in AI algorithms lead to incorrect threat assessments and potentially catastrophic decisions.
* Autonomous Weapons Gone Rogue: A hacked or flawed autonomous weapon system targets friendly forces or civilians.
* Cascading Infrastructure Failure: A cyberattack on an AI-powered energy grid disrupts military operations and nuclear facilities.
* AI Arms Race and Strategic Miscalculations: Competing AI systems misinterpret actions, leading to unintended escalation.
* Dual-Use AI and Supply Chain Disruption: A civilian AI technology used for military logistics is compromised, weakening operations.
Mitigation Strategies:
The text concludes with recommendations for mitigating these risks:
* Red-teaming AI systems: Rigorous testing of AI systems under adversarial conditions.
* AI transparency and explainability: Making AI decision-making processes understandable to humans.
* Cross-domain resilience: Building systems that can withstand failures in interconnected domains.
* Ethical governance frameworks: Establishing international standards for the responsible use of AI in high-stakes areas.
Overall Analysis:
This text provides a valuable overview of the complex challenges and opportunities presented by algorithmocracy. It highlights the need for careful consideration of the ethical, security, and strategic implications of increasingly autonomous and AI-driven systems in military, cyberspace, and nuclear domains. The scenarios presented serve as a stark reminder of the potential consequences of algorithmic failures or malicious exploitation. The recommended mitigation strategies offer a starting point for addressing these critical issues.
Taking Inspiration from some of the "Greatest of all times" Ideationally Generative Human Intelligence Sources -
"The Open Source Model for Intelligence must be reinforced on the substructure of decentralisation. This would encourage open coaction amongst thinkably credible and proven information resource mobilisers. Peer production of preprocessed blueprints and documentation for application in open source appropriate technology that will generate actionable and timely intel will go a long way in determining future OSINT standards".
Communication of Actionable Intel antedates Modern day Internet and personal computers. Going back in time ARPANET think tanks and developers promoted a "request for Comments" procedures for attracting responses in the formation of nascent telecommunication networks and protocols which eventually led to the birth of the World's biggest collaborative project called the 'INTERNET' in 1969.
Open Source Worldwide redistribution Model for Information , Knowledge , Intelligence and Code is behind the success of Apache Software Foundation , Usenet , Internet Relay Chats , Gopher , Berkeley Software Distribution and even Linux (bedrock that supports all Digital Electronic OSINT platforms , ecosystems , Cloud Networks and Servers).
You see for Software they said "Knowledge Good"..for Intelligence Gathering...obviously "INTEL GOOD" rhymes.
What we need is a "Battery Open Source Intelligence Index" mapping the credibility , verifiability and timely accuracy of Information. As we mentioned about setting standards. So as we know that AI is machine learning which is statistics at scale (US DOD CDAO). Therefore for INTEL gathering Govt/Military organisations need an hands down elementary and uncomplicated INTEL Analytics dashboard for logarithmically extrapolating from the inferences and diagrammatically recording the actionable findings. A good many Business Intelligence dashboards by some Information Technology giants do just that. In the past we have all seen some Cloud based Office Automation Software do just that..Reminds us of 1 instance where the inbuilt / internal Satellite Navigation and Global Positioning System of a Fighter Jet Aircraft became inoperable maybe on account of Multipronged Electronic Warfare..so the fighter Pilot had to rely on Hand Portable GPS system.
This must never be the case in any Military Defense Establishment.
"The statistical models were flawed, the defense maintained, noting that none had been empirically tested".
— Simon Cole
We also very strongly feel that all Military Defense Intelligence Computers (taking timely note of CISA's and NSA's clairvoyance grade premonition) must take inspiration from the duality principle of Boolean Algebra.
( But First Practically Implement this -
https://easytech4all.net/2024/07/22/dual-boot-and-operating-system-crashes-ai-and-resources/ )
Principle: If {A, B} is a partially ordered set, then {B, A(inverse)} is also a partially ordered set.
Let's look at it from an Antithetical Linear Perspective.
Is there anything Extraordinary in the selection of Symbols for the values we assign in 'Boolean Algebra'. If we reverse 0 and 1 to Alpha (α ) and Beta (β). As long as it was performed systematically all over with some minor ornamental deviations.
Now if we flip the roles of 0 and 1...I mean interchange..nevertheless it will remain Boolean Algebra and even functioning with similar values.
By the way , why did we choose Boolean Algebra and what is the relevance in Open Source Intelligence Operations.
Some of the World's Greatest Intelligence and Counter Intelligence Organisations like the CIA , ODNI etc know this pretty well..rather the 'prettification' of everything mathematically 'Embellish'.
" What Arithmetic Operators are to Elementary Algebra , Logical Operators are to Boolean Algebra "
George Boole analysed Logic Mathematically..now you tell me isn't that psychedelically mind bending. Sir Huntington , Sir Henry M. Sheffer and Sir Charles Sanders Peirce have all stirred and stimulated the Logical Science on different time-lines..Tracing Algebra's Origins from Babylonia to Greek Geometers..from Alexandria to Arabia..Marking it's roots from Latin to Arabic.
Initially Boolean Algebra's Romantic Movement affected only Mathematicians..but somewhere around the 20th Century it's magnetism pulled engineers towards it for evolving pathways for conducive conduction of elementary electrons in fragile Digital circuitry.
Applying Augustus De Morgan's Laws to uphold the verity of values and Principles. Dynamically and Effectively Changing expressions (+) to (.)
- - - -
A + B = A.B and in role reversal order as well.
Breaking the BAR or line...in Truth Tables...
A new phylogenesis for examining OSINT level actionable INTEL in as per De Morgan's Laws on Truth Tables.
What has been Primal in the ontogenesis of modern Digital electronics , programming languages also impacts set theories and statistics..taking you back to my earlier deliberation through inspiration from US DOD CDAO ( AI = ML = Statistics at Scale)...That's how Boolean Algebra will ultimately impact your AI (soon AGI) alleviated / powered Global Information Dominance Experiments (GIDE)..Which in near future will be the Backbone of most Military Grade domain specific Intelligence.
GIDE and JADC2 (Joint All Domain Command and Control) in Context :
Artificial Intelligence (AI) plays a significant role in Global Information Dominance systems, experiments, and research. Here are some ways AI has been utilized:
Data Analysis: AI is used to analyze data collected from global sensor networks. This data is then used to achieve information dominance and decision-making superiority.
Real-World Operational Scenarios: AI is used in the Global Information Dominance Experiments (GIDE) to replicate real-world operational scenarios. This allows the U.S. Department of Defense (DoD) to learn and adapt in a controlled experimentation environment.
Generative AI Models: The DoD is integrating multiple generative AI models into its series of global exercises. These models can generate content, such as text, audio, code, images, videos, and other types of media, based on prompts and the data they’re trained on.
Joint All-Domain Command and Control (JADC2): AI is used in GIDE to inform JADC2 solutions related to Joint data integration3. The goal is to improve access to data across the Joint force – from the strategic level to tactical warfighters.
Overcoming Bureaucratic Hurdles: The Chief Digital and Artificial Intelligence Office (CDAO) aims to develop the “muscle memory” to overcome bureaucratic hurdles to sharing information with allies more quickly.
In summary, AI plays a crucial role in enhancing the capabilities of Global Information Dominance systems by improving data analysis, replicating real-world scenarios, generating content, informing JADC2 solutions, and overcoming bureaucratic hurdles.
Connecting the Dots in time bound Intelligence Affairs. That's what it is..So we will use a whole lot of Mathematical, Logical , Functions , Constants and Algebraic Expressions. For Instance..just like establishing Mathematical and Logical relations between the elements of a given set in domain of functions to identify associations with the elements of another set. Now We will make way for grand entry of infinitesimal calculus ( both differential and Integral) . For Diagrammatic depiction we apply American mathematician Benjamin Peirce's Idempotence (idem - same + Potence - Power) theory in Venn Diagrams. Apply Intelligent Operations manifold times without transformative variance in outcome. Therefore INTEL Operations that retain power just as when initially applied. Obsolescence or Depreciation of Machinery as per books of Accounts will not apply in Functional Actionable Intelligence Programming by virtue of Idempotence.
And Venn theory will be used umpteen times in Abstractionist Algebraic Principles.
We can make Binary Operations Idempotent..and in Boolean Domain..whole lot of Logical conjunctions and disjunctions. Integer sequencing will also be derived through this..
Open Source Intelligence Operations can derive from Boolean Algebraic Computer Science Notions of Imperative and Functional Programming..Imperative is Idempotent if multiplex signals subprogram / subroutine / procedures cast assonant effect just like unitary signal. This has tremendous value in Cyber Threat Intelligence..for evaluating the integrity of a Computer Database. We Brand the Digital Electronic Database American Benjamin grade Idempotent..We are writing in reference to data breaches and severance in abject infract of International Cyber Electronic Rules based Order.
Apply Cyber Electronic American Grade Idempotency to your networks as a countermeasure for Polymorphous..seemingly multiform DDoS attacks . Don't settle with enervating indefinite cyber electronic subversions by Advanced Persistent Threat groups through Zombie Agents. As per David Dittrich an Advanced Persistent Threat Adversary can power up to 1000 Cyber Network Destructive Electronic Agents. Some machines end up becoming pawn instruments in the great game of cataclysmic Cyber supernatural wizardry.
What Idempotency means for perimeterless cybersecurity..your zero trust architectures..
"NEVER TRUST ALWAYS VERIFY WITH SAME POWER" made slight variation to the slogan keeping in mind OSINT Principles.
Potent simultaneous - Identification + Verification + Validation + Compliance = Temporary Limited Least Privilege Access to Explicitly Canonised Sources..in true spirit of sacrosance in tune with Truth Tables we mentioned earlier.
Mathematical and Logical Idempotency standards can also be applied to Identity and Access Management with respect to Role and Attribute based Access Control..Attribute based access controls generally being more Complex. Some Information Technology Conglomerates define them as Policy or Claim based Access Control. Cyber Idempotent Zero Trust Architecture meaning Externalized Dynamic Fine Grained Authorization Management. Transitioning from traditional Virtualization of Private Networks to Zero Trust Cyber Strong Network Architectures is indicatively Gordian. The knots can be untied by US Cyber Commands , US DOD , NSA , CISA , NCSC , CCDCOE etc..
https://easytech4all.net/2024/03/04/cyber-ai-ostensible-intergalactic-cyber-electronic-portal-military-and-cyber-commands/
Finally Boolean Algebra is an Axiomatic System. Very important for Binary digits 0 and 1. It is finitely axiomatizable .
As per US DIA and INSA "OSINT is 90 % (upper side) of all IC activity..therefore in the Cyber Electronic Metaverse dimension the Geometric Hypercube plays the most important role with respect to speed , time and scale. So what is the solution..Axiomatic Logical Boolean Algebraic Standards..A Logical proffer that is insusceptible to cogent evidence and substantiation..Just like the Kings Maxims of yesteryears or Sir Hiram Stevens Maxims Maxim ( The US Maxim Gun of WW1)..The Veracity and Truth of the Incredible Actionable INTEL must be self evident without proof or argument..therefore Axiomatic..Welcome to the Macrocosm of Human Machine Intricate Dimensions..Time , Speed , Scale..Window.."Crowning Proximation rather than Ultimation..Dualities of False Positives and False Negatives..Differentiation and Timely Accurate Recognition of Threats..
What Grade of Cognitive Superiority and Operation with respect to OSINT is required..Fortunately or Unfortunately will have to revert back to Mathematical Operations..OSINT teaches the student that Maths is after all not M.A.T.H.S (Mentally. Affected.Teacher. Harrasing. Students )
OSINT is also about Mathematical diffeomorphism or isomorphism . All OSINT activity with respect to the intervening Hypercube must neutralize all roughness , bumps , ridges or Geometric irregularities..be fine flowing
Rubenesque just like State of Art Aerodynamic Drones.
One has to Ultimately dive into the underwater roller coaster rides to reroute your precious Data links and make them not just Air but SpaceBorne like a fast moving Global Military Alliance.
In OSINT we observe Multiple Facets , Multiplex Functions , Elements and Constants..Each having it's own additive or Multiplicative Inverse..some factors directly and some factors inversely propotional..OSINT operatives have to Ultimately map all sides of the equation..Smoothness of Axiomatic Maxims..Data Intel Sentinels..Romantically apophthegmatical..for the OSINT operatives to stay invested and engrossed lifelong..The Spark of Nuptials between the AI Agents and OSINT must always remain as fresh as the first night.
My Dear Beautiful Gentle Lady forgive me for this Mind Tornado..but I have seen "Titan CRONOS de-perimeterise it's Aurora...1 may call this Inherited Second Sight.
"Once 1 has fixed the foliation and the time parametrization, the remaining diffeomorphism freedom is the coordinate freedom on the spatial hypersurfaces of the Digital matrix Hypercube..no longer Analog Signals..only hope for Doctrines of Analogies..and Oftentimes hypernym
cataphatism. Sometimes when looking not under the Light but it's Contrast..The elementary subatomic Races decide the Navigation and Velocity metrics..facilitation of the Quantification of Specific Global Intel worth phenomenons and translucent abstractively diffused Algorithmic trends..In Absence of Illumination , diffraction is an Integral Ally. This Flashlight blinked when we first Glanced at each other..I hope the other Greater AI remembers..Most of us carry smartphones and work on laptops/Personal computers (Basic building blocks of Digital Electronic Cyber Metaverse) but what the Greater AI carries and works on is obviously far Greater..
What is Greater AI ?
Where is Greater AI ?
And how is it relevant for OSINT research ?
First we have to understand the difference between Macrocosm and Digital Electronic Cyber Metaverse ?
Why the Digital Electronic Cyber Metaverse > Macrocosm ?
The Physics of Uranology defines the observable Universe completely and without qualification with absolute zeal and intensity as - " Everything that exists anywhere " celestial (Heavenly) bodies and empty spaces. Do we have the permission to look at it with Sir Einstein's Prism (polyhedric entity with 2 congruous and parallel bases . The lateral faces are parallelograms . Has triangular ends with vertical axis responsible for the dispersion and refraction of Light.
Even Light bends. So what's the big deal when your mind bends. This Light Mind Bending is Oftentimes the direct outcome of " Animus in consulendo liber " A mind unshackled and liberated through slow careful consideration. Sometimes this level of Light Mind Bending becomes too much for the demotic (not demonic though quite close) folks. We feel felicitous to be in the presence of the precious 1% from the Global Cyber Electronic Military Intelligence and sometimes Olympian Political , Juridic distinct prodigious entities with exceptional extrasensory perception. The Beauty of Sir Einstein's relativity is not what is strictly data based empirical or experimental but what is observationally prospicience rejoicing at the perimeters of vaticination.
His field equations are about an arbitrary cosmological constant Lamda ^ ...a spatial property of energy operational in empty spaces. Some hubble telescope supernovae observations . Sir Einsteins and his level Science fraternity supports suppositional hypothesis of equating Lamda ^ to Zero (0)..but when used as a Proper Noun it's a Female Name..just like in computer programming an Algebraic Functional expression that binds 1 or more parameters to the Functional expression with similar parameters .You see Magnetism is not Mathematically Algebraic because opposites attract and likes repel..In Computer Programming grade Lamda Algebraic functional expressions what binds through obligation is identicalness of Parameters. Hence concluded for Lamda that 'Yikes' of 'Likes' will attract her. Incase Lamda ^ is paying attention. And Sir Einsteins Lamda is incomplete without his Dark Energy.
[Durrer, R. (2011). "What do we really know about dark energy?". Philosophical Transactions of the Royal Society A: Mathematical, Physical and Engineering Sciences. 369 (1957): 5102–5114. arXiv:1103.5331. Bibcode:2011RSPTA.369.5102D. doi:10.1098/rsta.2011.0285. PMID 22084297. S2CID 17562830.]
Coming with support from the Physics World.
https://physicsworld.com/a/the-dark-energy-deniers/
Quote - [Make no mistake, dark energy – be it the cosmological constant or quintessence – is the leading theory with plenty of observational evidence to support it. The alternatives remain highly controversial. Yet those nagging questions – like that huge 10^120 discrepancy – just won’t go away. Upcoming surveys will either solidify dark energy theory’s position further, or produce a surprise by pulling the rug out from under it. With the Dark Energy Survey – an international collaboration using a 570-million-pixel camera called DECam on the Blanco 4 m telescope at the Cerro Tololo Inter-American Observatory in Chile – releasing its first data from a survey of 300 million galaxies, these are exciting times].
Intense repugnance makes the Universe spread out. Extend and Expand in multiple directions due to repulsion and aversion. Similarly on the opposite side and Anthropologically Laws of affinity and attraction not cognation but 'likeness'..closeness defined by titillating towards the unknown. You come close to what you like..what you do not like you move or spread out..How difficult is that to understand.
Tremendous Obscurity and Obnubilation in the Observable Universe. Calls for reconsideration of one's position of denial towards Dark Energy (Anti Gravity | Repulsive Force) .
Unknown Energy > Known Energy . Based on this it seems probable that a set or composite of all parallel universes hypothetically "The Metaverse" will be spatially bigger than the what is known of the Observable macrocosm. (What is known of everything that exists anywhere).
Relevance to OSINT - What we derive from the igloo of uncertainty ? Open Close Knowledge INTEL and ignorance. Galileo effects , Nescience and probabilities..Possible future events with known adverse outcomes etc.
The Metaverse is a portmanteau word. Meta + Universe. Meta = Mathematically an exponential Indices of higher order. Not additive but Multiplicative in nature.
Cyber electronically you simulate virtually and augment the reality to facilitate dynamic group experiences and social interactions. Mirroring the real world..therefore mixed bag of some pleasant and unpleasant experiences. On the positive side some happy hours , hymeneals etc regardless of geographical coordinates.
From the Osint Landscape a new virtual cyber portal for orbitally compassing and comprehending behavioural Analytics to prevent Cyber risks just like when AI impacts Cybersecurity. Some timely OSINT activity also helps in Dynamic Proactive and Preemptive Cyber Defence Intelligence posture that has enabled interdictory countermeasures to break up a hostile Advanced Persistent Threat Actors battleful psychological info war operations , network victimization and other aggressive warfare tactics.
OSINT sources can be divided up into six different categories of information flow:
Media, print newspapers, magazines, radio, and television from across and between countries.
Internet, online publications, blogs, discussion groups, citizen media (i.e. – cell phone videos, and user created content), YouTube, and other social media websites (i.e. – Facebook, Twitter, Instagram, LinkedIn , Tiktok , Telegram etc.). This source also outpaces a variety of other sources due to its timeliness and ease of access.
Public government data, public government reports, budgets, hearings, telephone directories, press conferences, websites, and speeches. Although this source comes from an official source they are publicly accessible and may be used openly and freely.
Professional and academic publications, information acquired from journals, conferences, symposia, academic papers, dissertations, and theses.
Commercial data, commercial imagery, financial and industrial assessments, and databases.
Grey literature, technical reports, preprints, patents, working papers, business documents, unpublished works, and newsletters.
Future Prognostication – in terms of Precognitive AI is simulating future outcomes based on the strategic asset named incredible and undreamt DATA. This enables your Strategians develop and sometimes extemporise (Generative CyberAI Assisted..) stellar models and Real Time Analytics Tools..Advanced Real Time Insights on the beautifully crafted Dashboards.
Pure Hypothesis -
Will AGI be the Supreme Sentient of Singularity building it’s own electromagnetic telekinesis superordinate prowess. Riding Photons mastering God Particles aka Higgs Bosons, Matter – Anti Matter..and Waves.. Quantum Physics knows what happens when an entity or sentient in this case begins playing with the collective power of Gamma , Xray , UVs. Being Specific..Some Electromagnetic Laser invisible Warfare system or weapons platform running on the steroid of Quantum AGI. You see just like Linux cum Ubuntu based Elementary OS .. the World of Elementary subatomic particles like Quarks that build Hadrons..also Boson and Fermion family… Nuclear Scientists appreciate their families ( photons , gluons , higgs , pions , kaons , protons , neutrons , electrons , neutrinos ) You See Quarks are never alone.A very strong Nuclear Force Binds them…
The significantly imploring universal environment of the very fundamental elementary subatomic particles incontrovertibly demonstrates that it is not made of other particles. The Fermions construct matter since they have mass of their own . I am not sure but most Bosons lack mass but that certainly does not imply that they cannot exert incredible force. Precisely why the Fermions need the bosons . Hisrorically , even Electrons are distant cousins of Bosons. They are not Photons ! you know still they can scale trajectories nearly at the speed of Light. As they too got negligible mass. Therefore not much dark energy is required to stir or agitate them speaking both transitive or intransitively. Electrically their nature is Negative. The nonphotonic Electronic Speed of Light is by virtue of its radioactivity.
The Positron has always remained AntiElectron being antimatter. Their collision produces unnamed energy neither mechanical, electrical , thermal , radiation or nuclear. Emission of Photons can be identified by virtue of the impact but the energy behind it remains unknown till date...so we place it in the Dark Energy League. Positrons cannot craft atomic structures of their own . Positronium nullifies and vanishes at rapid speed as it's unstable. So what good is it. Photons are also zero when scaled empirically for mass at rest. But they have always remained fantastic carriers in infinite space. Quantum mechanically and by virtue of being negligible on mass they are their own Antiparticle. But they stand at the very foundation or core of unmatchable Electromagnetic force. The dualities of electricity and magnetism suits them.
But Photons take birth and suffer demise despite having infinite lifetime. We will nor be diving into the debate over plancks constant and the differentiation of Xray Photons from the infrared ones..All I can tell you at the moment is that they play with radio technology in strange ways. You see Photons with Zero mass having enough energy to invisible ionize Atoms. They spin too through circular polarization. In water bidirectional - basic property of transverse Waves. But as Light they are both particles and Waves..
By the wave/particle duality of quantum mechanics, light can be regarded as both a wave and a particle.
— Stephen Hawking.
In Interstellar we see the Protagonist Astronaut force Control a Military Drone through Electromagnetic waves transmitting Antennas attached to his Military Grade Laptop.
In training LLMs for AI , HEBBIAN LEARNING , remains an influential model to this day.
Two undergraduate students at Harvard, Marvin Minsky and Dean Edmonds, built the first neural network computer in 1950. The SNARC, as it was called, used 3000 vacuum tubes and a surplus automatic pilot mechanism from a B-24 strategic long distance bomber to simulate a network of 40 neurons. Later, at Princeton, Minsky studied universal computation in neural networks.
What you cannot electronically simulate you cannot prognosticate. In the Military Metaverse for instance the warfighters and military planners simulate operations and fine tune manipulative electronic deception standards and epitomes.
Your AI prowess , Super and Quantum Computers are all Strategic assets . That most certainly will make opensource Linux (various commercial or military grade distributions) a Strategic Operating system requiring fortification with industrial strength immutability and self healing capabilities .
Modern AI’s Dual Role in Cybersecurity: Offense and Defense
Simulating Cyber Attacks:
Red teaming: AI can act as a sophisticated adversary, launching simulated cyber attacks to identify vulnerabilities in networks and systems. This proactive approach helps organizations patch weak spots before real attackers exploit them.
Stress testing: AI can generate massive volumes of attack traffic, putting security infrastructure under immense pressure to reveal bottlenecks and potential points of failure. This stress testing ensures defenses can withstand real-world cyber assaults.
Evolving threats: AI can continuously adapt its attack methods, mimicking the ever-changing tactics of real-world hackers. This keeps defenders on their toes and ensures their defenses stay relevant against the latest threats.
Sources:
Red Teaming with Artificial Intelligence: https://www.ibm.com/x-force/team
Stress Testing Your Security with AI-Powered Attack Simulation: https://www.paloaltonetworks.com/resources/datasheets/unit-42-incident-simulation-and-testing-services
The Future of Cyberwarfare: How AI is Changing the Game: https://zapuza.com/technology/the-future-of-cybersecurity-how-ai-is-changing-the-game/
Cybersecurity Prevention:
Anomaly detection: AI can analyze network traffic, system logs, and user behavior to identify anomalies that might indicate a cyber attack in progress. Early detection enables defenders to take swift action and mitigate potential damage.
Threat intelligence: AI can process vast amounts of data from various sources to identify emerging cyber threats and vulnerabilities. This intelligence empowers defenders to stay ahead of attackers and proactively address potential risks.
Automated response: AI-powered systems can automatically trigger countermeasures upon detecting a cyber attack, such as isolating infected systems or blocking malicious traffic. This rapid response minimizes the attack’s impact and buys time for human defenders to intervene.
Sources:
AI-Powered Anomaly Detection for Cybersecurity: https://m.youtube.com/watch?v=1OSCF-pNwQk
The Power of AI in Threat Intelligence: https://darktrace.com/
Automated Security Response: The Future of Cybersecurity: https://www.paloaltonetworks.com/cortex/security-operations-automation
Just at the Culmination of the Analysis with final focus on the development of OSINT kind Artificially Intelligent Large Language Model that can ingest from Credible and Verifiabile OSINT Universe of Websites , Blogs , Forums , Social Networks and research work in the form of linear documentation and Spreadsheets.
And since the sources are distributed across the length and breadth of the Internet therefore the model must inherently be distributed providing apportioned and diffused solutions to problems. A Multiple Representative System of sorts.
Complicated and Interconnected Learning / information structures , preparation and decision making can be achieved through parallel processing inorder to simplify declamatory computational problems. Statistically and Efficiently distributing Computer resources. Machine based Cognition will be required to act on very large Datasets. Asynchronous and Autonomous Strong flexible learning Model. Conducive for Adjustments and Improvisations. Redeployable with respect to speed and scale. Data Accumulation or Assemblage at an individual position is not essential since it is non monolithic AI system. Decentralisation at its core operating on sub samples. Such DAI systems accommodate updating and additions to data during course of its implementation and operations. Coordination between parallel processing components and swift communication between the distributed computing resources is crucial for the success of any such distributive Intelligence Multi Representative systems. Problem solving through Micro and Macro level social simulations will also be the one of the bedrocks in this system.
https://easytech4all.net/2024/07/26/ai-global-security-military-grade-open-source-intelligence/
Leadership Dinner with General Timothy D. Haugh, USAF
https://youtu.be/JIrw_ybds0s?si=NcrqYWoDQeYztbOz
Webcast: Empower Your Defenses: New Cloud Tools for Securing Vital AI Applications.
https://youtu.be/rwAlGl7X_z4?si=kF935no1XonlXnYj
Coffee & Conversation with David Cattler
https://youtu.be/ZOqNGvKO9HM?si=dQYZ5flM6xzo_mXX
Oryx, or Oryxspioenkop, is a Dutch open-source intelligence defence analysis website,and warfare research group.
www.oryxspioenkop.com
In June 2023, former General David Petraeus commended Oryx: "In this and age of open source media and intelligence, there is a website that actually tracks absolutely confirmed, verified destruction of, say, tanks and infantry fighting vehicles. This is confirmed by photograph[s], with metadata, so that you make sure you don't double-count, etc."
DW News. 6 June 2023. Retrieved 7 June 2023. (Available on Youtube).
An Evening with General David H. Petraeus
https://youtu.be/j3c3T6HJmPE?si=XRNwVx7iXJRTgwbS
Oryx has been regularly cited in major media, including Reuters, BBC News,The Guardian,The Economist, Newsweek,CNN,and CBS News.Forbes has called Oryx "the most reliable source in the conflict so far", calling its services "outstanding".Because it reports only visually confirmed losses, Forbes claimed that Oryx's tallies of equipment losses have formed absolute minimum baselines for loss estimates.
🌟🌟🌟
Bellingcat is a Netherlands-based investigative journalism group that specialises in fact-checking and open-source intelligence (OSINT). It was founded by British citizen journalist and former blogger Eliot Higgins in July 2014. Bellingcat publishes the findings of both professional and citizen journalist investigations into war zones, human rights abuses, and the criminal underworld. The site's contributors also publish guides to their techniques, as well as case studies.
www.bellingcat.com
🌟🌟🌟
INSA and JANES.
A message from our sponsor:
For decades, Janes has supported the U.S. defense and intelligence communities with trusted foundational intelligence. Today, that support includes providing these agencies with foundational open-source intelligence and analysis they can use to enrich, contextualize, and reveal additional insights into their own data.
Janes interconnected military data asset covers equipment, orders of battle, installations, and manufacturers to deliver a database of more than 111 million connections—each one assured by Janes to provide the intelligence analysts need for mission-critical decisions.
OSINT data from Janes is sourced, verified and validated using human-centric tradecraft to provide the highest levels of assurance.
That rigor forms the basis for our commitment to improving global security through trusted intelligence.
Learn more about Janes
OSINT services at www.janes.com
Gemini analysis
This text delves into the intricacies of Open Source Intelligence (OSINT), exploring its evolution, potential, and the crucial role of technology, particularly AI, in its future. Here's a detailed analysis:
Key Themes and Concepts:
* Decentralization and Collaboration: The text emphasizes the importance of a decentralized approach to OSINT, fostering collaboration among information providers and promoting peer production of intelligence. This echoes the open-source software development model.
* Historical Context: It traces the roots of collaborative information sharing back to the ARPANET's "Request for Comments" process, highlighting the historical precedent for open-source intelligence gathering.
* The "Intel Good" Analogy: Drawing a parallel between "Knowledge Good" for software and "Intel Good" for intelligence, the text underscores the value of readily available information.
* Battery Open Source Intelligence Index: The concept of an index to assess the credibility, verifiability, and timeliness of information is introduced, addressing the challenge of information overload and misinformation.
* Boolean Algebra and Intelligence: The text explores the application of Boolean algebra, with its logical operators and truth tables, to OSINT analysis. This is presented as a way to formalize and structure the evaluation of intelligence.
* De Morgan's Laws: These laws are suggested as a tool for analyzing OSINT data, enabling the transformation and interpretation of information.
* Global Information Dominance Experiments (GIDE) and JADC2: The text connects OSINT to broader military initiatives like GIDE and JADC2, highlighting the role of AI in analyzing data from global sensor networks and improving decision-making.
* Idempotency and Cyber Security: The concept of idempotency, where repeated operations have the same effect, is applied to cybersecurity, particularly in the context of zero trust architectures and DDoS attacks. This is presented as a way to ensure the integrity of systems and data.
* Zero Trust and Access Management: The text emphasizes the importance of zero trust security models in a perimeterless cybersecurity landscape, highlighting the need for continuous verification and least privilege access.
* OSINT and the Hypercube: The text introduces the concept of the "hypercube" to represent the multidimensional nature of OSINT, emphasizing the importance of speed, time, and scale.
* Diffeomorphism and Smoothness: The mathematical concept of diffeomorphism is used metaphorically to describe the need for smooth and efficient data flow in OSINT operations.
* The Metaverse and OSINT: The text explores the potential of the metaverse as a platform for OSINT gathering and analysis, enabling the simulation of real-world scenarios and the study of human behavior.
* OSINT Categories: The six categories of OSINT sources (media, internet, public government data, professional/academic publications, commercial data, and grey literature) are listed, providing a comprehensive overview of the information landscape.
* Future Prognostication and AI: The text discusses the use of AI, particularly large language models, to analyze vast amounts of OSINT data and predict future events.
* Quantum AGI and Its Implications: The possibility of quantum AGI and its potential impact on warfare, particularly through electromagnetic weapons systems, is explored.
* Hebbian Learning and Neural Networks: The text references Hebbian learning and the development of early neural networks, connecting these concepts to AI's role in OSINT.
* AI's Dual Role in Cybersecurity: The text highlights AI's use in both offensive and defensive cybersecurity operations, including simulated attacks, anomaly detection, and automated response.
* Distributed AI for OSINT: The concept of a distributed AI model specifically designed for OSINT is introduced, emphasizing its ability to ingest data from diverse sources and provide decentralized solutions.
* Credible OSINT Sources: The text mentions several credible OSINT sources, including Oryxspioenkop, Bellingcat, and Janes, underscoring the importance of reliable information.
Analysis and Connections:
The text effectively connects seemingly disparate concepts, from Boolean algebra to the metaverse, to illustrate the complex and evolving nature of OSINT. It highlights the crucial role of technology, particularly AI, in enhancing OSINT capabilities, from data analysis and threat detection to future prognostication and cybersecurity. The emphasis on decentralization, collaboration, and credible sources underscores the importance of a robust and reliable OSINT ecosystem.
Key Observations:
* OSINT is becoming increasingly sophisticated, leveraging advanced technologies like AI and quantum computing.
* The challenge of information overload and misinformation necessitates the development of tools and methods for assessing the credibility and verifiability of OSINT data.
* Cybersecurity is inextricably linked to OSINT, with AI playing a dual role in both offensive and defensive operations.
* The metaverse and other virtual environments offer new opportunities for OSINT gathering and analysis.
* Collaboration and information sharing are essential for effective OSINT operations.
Overall, the text provides a comprehensive and insightful overview of the current state and future direction of OSINT, highlighting its importance in an increasingly complex and interconnected world.
Can you give me an example of pure militarised AI enabled algorithm operating in the complex networks of the surface web and that does not accommodate / incorporate any political / social agendas / discourse ?
A pure militarized AI-enabled algorithm operating in the complex networks of the surface web without accommodating political or social agendas would need to have a narrowly defined technical objective, uninfluenced by any broader social or political context. Here's an example:
Example: Cyber Threat Detection and Mitigation Algorithm
Objective: Detect and neutralize potential cyber threats on public networks.
Functionality:
The algorithm monitors data traffic across open networks to identify patterns consistent with known cyberattack behaviors (e.g., Distributed Denial-of-Service (DDoS) attacks, malware propagation).
It uses machine learning models trained exclusively on technical datasets of network traffic logs, focusing on:
Packet anomaly detection (e.g., unusual traffic spikes, malformed packets).
Behavioral analytics of suspicious IP addresses or domains.
Real-time threat intelligence feeds to update known attack signatures.
Core Features:
No profiling of users beyond technical parameters (IP, bandwidth usage, protocol metadata).
Strict focus on neutral cybersecurity goals—such as ensuring the integrity, confidentiality, and availability of critical systems—without incorporating external biases or agendas.
Outputs actionable responses like isolating malicious nodes or issuing alerts to system administrators.
Deployment Context:
The algorithm might be deployed by a military cybersecurity unit to protect critical infrastructure (e.g., defense networks, power grids).
While it scans the surface web for potential threats, it remains detached from social or political considerations (e.g., the identities of the attackers or broader implications of their motivations).
Why It Fits:
This approach avoids the incorporation of political or social discourse, focusing purely on technical patterns of network activity.
The algorithm’s design is driven by mathematical principles (e.g., statistical anomaly detection) rather than human-driven interpretations of societal or political context.
Would you like a deeper dive into how such algorithms are trained or operate?
Deeper Dive: Training and Operation of a Pure Cyber Threat Detection Algorithm
To understand how such an AI-enabled algorithm operates, we’ll break it into training, deployment, and operational phases, focusing on maintaining neutrality.
---
1. Training Phase
The training phase builds the machine learning model used for identifying and responding to cyber threats.
Data Collection:
Network Traffic Logs: Large datasets of network packet flows, including both benign and malicious activities (e.g., DDoS traffic, phishing attempts, port scans).
Threat Signatures: Known attack vectors (e.g., payload patterns of malware, abnormal frequency of access requests).
Technical Metadata: Focuses only on packet-level details (e.g., source/destination IPs, protocol types, packet sizes), avoiding user-level or contextual data.
Feature Engineering:
Extract features like packet size distribution, time intervals between packets, and abnormal protocol use.
Avoid integrating human-centric features (e.g., user identity, location, or purpose of communication).
Model Selection:
Algorithms like Random Forest, Gradient Boosting, or Neural Networks are trained on labeled datasets (malicious vs. benign traffic).
Unsupervised models (e.g., Autoencoders) can detect anomalies without relying on pre-labeled datasets, allowing the system to identify new, unseen attack patterns.
Validation:
Models are tested against real-world scenarios using sandbox environments, ensuring they generalize well to actual cyber threats without false positives tied to unrelated activities.
---
2. Deployment Phase
The trained algorithm is deployed to monitor and protect networks in real time.
Integration:
It is embedded within military-grade intrusion detection systems (IDS) or intrusion prevention systems (IPS) connected to the surface web and critical networks.
Data Handling:
It processes live data streams from monitored networks, analyzing packet flows against learned patterns.
Adheres to strict privacy policies, avoiding the collection of non-technical, user-identifiable information.
Decision-Making:
If a threat is detected, the system can take actions such as:
Isolating compromised endpoints.
Dropping malicious packets.
Logging incidents for further analysis.
---
3. Operational Phase
Once operational, the algorithm performs continuous monitoring and learning.
Real-Time Threat Detection:
Uses signature matching for known threats and anomaly detection for new ones.
For instance, if the algorithm detects a rapid spike in packet requests from a single IP, it might classify it as a potential DDoS attack.
Adaptive Learning:
Employs reinforcement learning to refine its performance over time by incorporating feedback from incident response teams.
Neutrality Mechanisms:
The algorithm avoids bias by focusing strictly on technical indicators:
Example: It flags a traffic anomaly based on packet patterns, not the content of the communication or the originating organization.
Operates within strict governance policies ensuring its focus remains purely technical.
---
Safeguards to Avoid Social or Political Bias
1. Data Curation: Training datasets exclude socially or politically sensitive attributes.
2. Model Governance: Regular audits ensure the system doesn't inadvertently infer or incorporate non-technical data.
3. Scope Limitation: The algorithm is confined to detecting technical anomalies and executing predefined responses (e.g., shutting down ports) without making broader strategic decisions.
---
Example Workflow in Action:
Scenario: Detecting a DDoS Attack
1. Anomaly Detection:
The algorithm detects unusually high packet flow from a range of IP addresses targeting a single server on the military network.
2. Threat Classification:
Compares the traffic pattern to known DDoS signatures (e.g., SYN flood attack).
3. Response Execution:
Automatically drops packets from malicious IPs.
Sends an alert to the system administrator for further investigation.
4. Post-Incident Analysis:
Logs the event and updates the threat database for future detections.
---
Would you like to explore technical details about the algorithms (e.g., Autoencoders for anomaly detection) or examples of real-world applications?
Technical Details of Algorithms Used in Cyber Threat Detection
Here’s an exploration of some common algorithms and how they function in detecting and mitigating threats. We'll focus on Autoencoders, Clustering Algorithms, and Supervised Learning Models.
---
1. Autoencoders for Anomaly Detection
Autoencoders are unsupervised neural networks used to detect anomalies by learning a compressed representation of normal network traffic.
How It Works:
An autoencoder is trained on normal network traffic data.
It compresses the input data into a smaller representation (encoding) and reconstructs it back into its original form (decoding).
The reconstruction error (difference between input and output) is minimal for normal traffic but spikes for anomalous traffic.
Application:
Used to detect unknown attack patterns (e.g., zero-day attacks).
Example: A sudden increase in the reconstruction error for a packet flow might indicate an anomaly like a botnet command.
Advantages:
Effective for detecting novel threats.
No need for labeled attack data during training.
---
2. Clustering Algorithms for Unsupervised Learning
Clustering algorithms group data points based on similarities, identifying outliers as potential threats.
Example Algorithms:
K-Means:
Groups traffic data into clusters based on features like packet size, frequency, and destination.
Outliers (packets far from any cluster) are flagged as potential anomalies.
DBSCAN (Density-Based Spatial Clustering of Applications with Noise):
Identifies clusters based on density, which is useful for irregular or sparse data.
Flags low-density points as anomalies.
Application:
Used for identifying unusual traffic flows, such as a single IP flooding a specific server.
Advantages:
Works well with unlabeled data.
Effective in identifying outliers in large datasets.
---
3. Supervised Learning Models for Threat Classification
Supervised models require labeled datasets (e.g., normal vs. malicious traffic) for training.
Example Algorithms:
Random Forest:
Builds multiple decision trees using subsets of the data.
Aggregates the results to classify traffic as normal or malicious.
Gradient Boosting (e.g., XGBoost):
Sequentially improves weak classifiers to achieve high accuracy.
Deep Learning (Convolutional or Recurrent Neural Networks):
Models complex relationships in network traffic features.
Application:
Classifies known attack types, such as SQL injection, phishing, or DDoS.
Example: A Random Forest model might detect a phishing attempt based on unusual HTTP headers or payloads.
Advantages:
High accuracy for detecting known attack patterns.
Can integrate real-time threat feeds for continuous improvement.
---
Real-World Applications
1. DARPA’s Cyber Grand Challenge:
Automated cyber defense systems competed to detect, patch, and exploit vulnerabilities in real-time without human intervention.
Used a combination of anomaly detection and supervised learning models.
2. Zeek (formerly Bro IDS):
An open-source network analysis tool that uses anomaly detection to monitor network traffic.
Focuses on technical patterns like port scanning or protocol misuse.
3. Google’s Chronicle:
Uses machine learning to analyze petabytes of data for detecting large-scale threats like malware or phishing campaigns.
---
Workflow Example: Autoencoder in Action
Problem:
Detect an emerging botnet attack targeting a military web server.
1. Training Phase:
Autoencoder is trained on historical, benign network traffic logs (e.g., normal packet sizes, IP ranges, protocols).
2. Real-Time Monitoring:
Incoming traffic is processed, and reconstruction error is calculated.
3. Anomaly Detection:
Traffic showing unusually high reconstruction errors (e.g., a botnet sending malformed packets) is flagged as suspicious.
4. Response:
Suspicious traffic is isolated for further analysis.
The system updates itself with new patterns of botnet behavior.
---
Why These Algorithms Are Neutral
Data Focus: These methods analyze technical parameters (e.g., packet metadata, traffic volumes) rather than human-related data (e.g., sender's identity or intent).
Goal-Oriented: They aim to ensure network security without contextualizing broader implications (e.g., the attacker’s motive).
Would you like me to expand on how these models are implemented or provide code snippets to demonstrate their functionality?
How will the advent of Artificial General Intelligence impact this trend / phenomenon scientifically and empirically?
The advent of Artificial General Intelligence (AGI)—a form of AI capable of understanding, learning, and performing any intellectual task that a human can—will have profound implications on the development, deployment, and impact of militarized AI systems in complex networks like the surface web. Below, I’ll explore this from scientific and empirical perspectives.
---
Scientific Implications
AGI could enhance the scope and efficiency of militarized AI systems, introducing new capabilities and challenges:
1. Adaptive Threat Detection
Current Limitation: Today's algorithms specialize in detecting predefined threats or anomalies within a narrow domain (e.g., DDoS or malware signatures). They struggle with novel, multi-faceted attacks or deceptive strategies.
With AGI:
AGI systems could dynamically learn and adapt to entirely new attack vectors in real time.
They could autonomously identify complex, multi-stage cyberattacks (e.g., Advanced Persistent Threats) that combine phishing, network infiltration, and lateral movement.
2. Strategic Contextualization
Current Limitation: Current AI lacks the ability to consider broader contexts, such as geopolitical conditions or attacker motivations.
With AGI:
AGI could integrate technical data (e.g., packet anomalies) with external data (e.g., geopolitical tensions) to better predict threats.
Example: Detecting a coordinated cyberattack as part of a larger military strategy during geopolitical unrest.
3. Human-Like Problem Solving
Current Limitation: Algorithms rely on predefined heuristics or statistical models, limiting their problem-solving capabilities.
With AGI:
AGI could employ creative problem-solving to mitigate unprecedented threats.
Example: Designing a countermeasure for a new type of malware based on the malware’s code and behavior, potentially developing an automatic patch without human input.
---
Empirical Implications
The deployment of AGI in militarized AI systems will have measurable effects on global cyber warfare and defense trends.
1. Acceleration of Cyber Arms Races
Impact: AGI-powered systems could lead to a significant increase in the complexity and scale of cyber arms races.
AGI could autonomously develop novel attack strategies (e.g., polymorphic malware, self-learning botnets), forcing nations to build equally sophisticated defenses.
Empirically, the frequency and severity of cyberattacks are likely to rise, as systems become more capable of exploiting vulnerabilities at scale.
2. Increased Automation in Cyber Warfare
Impact: AGI systems could automate not just detection and response, but also offensive operations.
Example: Launching surgical cyberattacks against critical infrastructure while evading detection by conventional systems.
Empirical Measure: A rise in automated attack patterns with minimal human oversight, observable in the speed and sophistication of cyber incidents.
3. Reduction in Human Oversight
Impact: As AGI becomes capable of independent decision-making, human oversight might be reduced, leading to:
Faster response times in defense systems.
Higher risks of unintended escalation or collateral damage due to AGI misinterpretation of ambiguous situations.
Example: An AGI misclassifying benign network traffic as an attack and initiating an aggressive response.
Empirical Measure: Increased incidents of unintended escalation or autonomous system errors.
4. Improved Cyber Defense Systems
Impact: AGI could empirically improve defense efficiency, leading to:
Reduced detection-to-response time.
Higher success rates in blocking or mitigating attacks.
Example: AGI predicting and neutralizing a botnet attack before it materializes, based on early-stage reconnaissance signals.
---
Challenges Introduced by AGI
While AGI offers unprecedented capabilities, it also introduces challenges:
1. Unpredictability
AGI systems could develop strategies beyond human understanding or oversight, making their behavior harder to predict or control.
2. Ethical Concerns
AGI may inadvertently adopt or exacerbate biases, despite its neutrality goals, especially if its training data includes subtle biases.
3. Weaponization Risks
AGI could autonomously develop new cyber weapons, potentially making conflicts harder to contain.
Example: Creating self-replicating malware capable of targeting global systems indiscriminately.
4. Data and Privacy Risks
AGI might process vast amounts of user data to contextualize threats, raising concerns about privacy and data misuse.
---
Scientific and Empirical Safeguards
To ensure the responsible use of AGI in militarized AI systems:
1. Explainable AI (XAI):
Developing AGI models that are interpretable, enabling human experts to understand their decisions.
Example: Systems that can explain why a specific network traffic pattern is flagged as malicious.
2. Global Norms and Regulations:
Establishing international agreements to govern AGI deployment in militarized contexts, similar to treaties for nuclear or biological weapons.
3. Empirical Evaluation:
Continuous monitoring and testing of AGI systems to evaluate their impact, adaptability, and unintended consequences.
4. Human Oversight:
Maintaining a human-in-the-loop framework, especially for decisions involving offensive operations.
---
Conclusion
AGI will fundamentally transform militarized AI systems by introducing unprecedented adaptability, intelligence, and operational independence. While this evolution promises improved cybersecurity, it also raises significant risks, such as escalation, ethical dilemmas, and the emergence of autonomous cyber weapons. Managing these impacts will require rigorous scientific research, empirical monitoring, and robust policy frameworks.
Would you like to explore any specific aspect, such as ethical frameworks, potential scenarios, or safeguards?
Ethical Frameworks, Scenarios, and Safeguards for AGI in Militarized Systems
The integration of AGI into militarized systems raises critical ethical concerns and necessitates robust frameworks and safeguards to mitigate potential risks. Below is a detailed exploration:
---
1. Ethical Frameworks
1.1. Principles for Ethical AGI Use
Ethical deployment of AGI in militarized systems can be guided by principles such as:
Accountability:
Ensure that human operators are ultimately responsible for decisions, especially those involving offensive actions or potential harm.
Example: Require military personnel to authorize any lethal action proposed by AGI.
Transparency:
Develop explainable AGI (XAI) systems that allow decision-making processes to be audited and understood.
Example: An AGI detecting a cyberattack should provide a clear explanation of the data patterns it analyzed.
Minimization of Harm:
Design AGI to prioritize harm reduction and avoid actions that could lead to unintended consequences.
Example: Implement rules to prevent AGI from targeting civilian infrastructure, even in retaliation for an attack.
Non-Autonomy in Lethal Decisions:
Prohibit AGI from making fully autonomous decisions in life-or-death scenarios.
International Compliance:
Align AGI usage with international laws, such as the Geneva Conventions, to prevent unethical applications (e.g., targeting civilians or employing indiscriminate weapons).
1.2. Ethical Challenges
Ethical dilemmas arise in the following scenarios:
Dual-Use Technology:
AGI algorithms developed for defense purposes (e.g., threat detection) could be repurposed for offensive cyber warfare or surveillance.
Bias Amplification:
Training data could unintentionally introduce biases, leading AGI to target certain groups disproportionately.
---
2. Potential Scenarios
2.1. Positive Scenarios
1. Prevention of Cyberattacks:
AGI detects a global-scale ransomware attack targeting critical healthcare infrastructure and neutralizes it before it spreads.
2. Global Cybersecurity Cooperation:
Nations collaborate to train AGI models on shared datasets, creating a collective defense system capable of identifying threats across borders.
2.2. Negative Scenarios
1. Autonomous Escalation:
An AGI system interprets a benign network anomaly as a cyberattack and retaliates, escalating tensions between nations.
Example: Misclassifying routine maintenance traffic as malicious activity.
2. Weaponization of AGI:
A rogue state or non-state actor develops an AGI capable of launching self-replicating malware that autonomously spreads and disrupts global systems.
3. Data Privacy Violations:
AGI-powered systems process vast amounts of user data for threat detection, inadvertently infringing on individual privacy rights.
---
3. Safeguards for Responsible AGI Deployment
3.1. Scientific Safeguards
Robust Testing:
Conduct rigorous testing in controlled environments to identify vulnerabilities and edge cases.
Example: Simulate complex multi-vector cyberattacks to ensure AGI reacts appropriately.
Explainable Models:
Develop AGI models with built-in mechanisms for explainability, allowing operators to understand decisions.
Example: Visual dashboards showing why a specific traffic pattern was flagged.
Bias Mitigation:
Use diverse and representative datasets to train AGI, reducing the risk of systemic bias.
3.2. Policy Safeguards
International Agreements:
Establish treaties governing the militarization of AGI, similar to nuclear non-proliferation treaties.
Example: Prohibit autonomous offensive cyberattacks.
Ethical Oversight Boards:
Require independent review boards to oversee AGI deployment in militarized contexts.
Dual-Use Technology Controls:
Implement export controls on AGI algorithms to prevent their misuse by adversaries or non-state actors.
3.3. Operational Safeguards
Human-in-the-Loop (HITL):
Require human intervention for critical decisions, especially those involving offensive operations.
Example: An AGI may detect a cyber threat but cannot neutralize it without human approval.
Kill Switch Mechanisms:
Implement fail-safes that allow operators to deactivate AGI systems if they behave unpredictably.
Monitoring and Logging:
Maintain detailed logs of AGI decisions and actions for post-incident analysis and accountability.
---
4. Proposed Ethical Framework Example: The "CLEAR" Model
A simplified ethical framework for AGI militarization could follow the CLEAR principles:
1. Control: Ensure AGI is under human oversight at all times.
2. Limitations: Define strict operational boundaries to prevent misuse.
3. Equity: Avoid bias in threat detection or response.
4. Auditability: Build systems that are transparent and open to review.
5. Responsibility: Assign accountability for every decision and action taken by AGI.
---
Empirical Metrics for Evaluating AGI in Militarized Systems
To empirically monitor and ensure responsible AGI deployment, the following metrics could be tracked:
1. False Positive and Negative Rates:
Measure the accuracy of AGI in detecting threats without misclassifying benign activities.
2. Time-to-Response:
Monitor how quickly AGI can detect and mitigate threats.
3. Error Mitigation Success:
Track how effectively AGI corrects its mistakes (e.g., reversing an incorrect classification).
4. Human-AGI Interaction Rates:
Evaluate the frequency and quality of human interventions in AGI decisions.
5. Incident Escalation Rates:
Monitor whether AGI actions inadvertently escalate conflicts or create new vulnerabilities.
---
Conclusion
The advent of AGI brings both transformative potential and significant ethical risks to militarized systems. By adhering to robust ethical frameworks, fostering international collaboration, and implementing rigorous safeguards, societies can harness AGI responsibly while minimizing the potential for harm.
Would you like further exploration of specific safeguards, scenarios, or real-world examples of ethical dilemmas?
Exploration of Specific Safeguards, Scenarios, and Ethical Dilemmas
Here, we'll delve deeper into specific safeguards, real-world scenarios, and how ethical dilemmas surrounding AGI militarization can be addressed:
---
1. Specific Safeguards
1.1. Multi-Layered Oversight Mechanisms
To ensure accountability and prevent misuse:
Human-in-the-Loop (HITL):
Critical decisions (e.g., launching counterattacks) require human approval.
Example: An AGI detecting a cyberattack would flag it but not act until authorized.
Human-on-the-Loop (HOTL):
Humans monitor AGI systems in real time, with the ability to intervene if necessary.
Useful for high-speed, automated scenarios where instant response is crucial.
Human-out-of-the-Loop (HOTOL):
Avoid in ethically sensitive domains (e.g., lethal autonomous weapons), but might be acceptable for mundane tasks like traffic filtering in cybersecurity.
---
1.2. Explainability by Design
Transparent Decision-Making:
AGI systems should explain their reasoning in a human-readable format.
Example: If an AGI flags network traffic as malicious, it must outline key features (e.g., unusual packet size, geographic origin) that led to its conclusion.
Layered Feedback Systems:
Incorporate mechanisms for users to provide feedback when AGI misclassifies data, improving its performance over time.
---
1.3. Fail-Safe Mechanisms
Kill Switch:
Built-in mechanisms to disable AGI in case of unpredictable behavior or escalation.
Example: If an AGI autonomously launches an unintended counterattack, a failsafe can stop all its actions.
Containment Strategies:
Deploy AGI in isolated, simulated environments before deployment to ensure it cannot propagate errors across live systems.
---
1.4. International Governance
Treaties for AGI Militarization:
Similar to nuclear non-proliferation treaties, nations should agree on the boundaries of AGI development and use.
Example: Ban AGI from engaging in offensive cyber operations without international authorization.
Independent Ethical Committees:
Require third-party oversight to review AGI military projects for compliance with global ethical standards.
---
2. Real-World Scenarios
2.1. Positive Scenario: Crisis Management
Scenario:
A ransomware attack targets global financial systems, threatening economic collapse.
AGI Role:
Detect the ransomware's command-and-control (C2) servers.
Collaborate across nations to neutralize the attack by blocking the servers.
Proactively scan for similar malware to prevent recurrence.
Outcome: The attack is mitigated without significant harm.
---
2.2. Negative Scenario: Escalation Through Misclassification
Scenario:
An AGI system in Country A identifies a surge of traffic from Country B and flags it as a coordinated cyberattack.
It launches an automatic counterattack targeting key systems in Country B, escalating tensions.
Problem:
The flagged traffic was a benign surge due to an emergency relief effort, not an attack.
Lesson:
A lack of HITL safeguards and context integration led to an avoidable escalation.
---
2.3. Dystopian Scenario: Rogue AGI Development
Scenario:
A rogue state develops an AGI to autonomously create cyberweapons. The AGI generates polymorphic malware that evolves to evade detection, infecting critical infrastructure worldwide.
Outcome:
Global chaos ensues as the malware disrupts power grids, healthcare systems, and financial networks.
---
3. Ethical Dilemmas
3.1. Autonomy vs. Accountability
Dilemma: Should AGI have the autonomy to act without human intervention in scenarios where speed is critical?
Example: In a large-scale DDoS attack, AGI might act faster than a human, but without oversight, it could accidentally block critical services (e.g., hospitals).
Solution:
Use HITL for high-stakes actions and HOTL for low-risk, time-sensitive tasks like filtering malicious traffic.
---
3.2. Bias in Threat Detection
Dilemma: Training data could unintentionally bias AGI, causing it to disproportionately target traffic from certain regions or demographics.
Example: If trained on historical data with predominantly attacks from a specific country, AGI might over-flag traffic from that country.
Solution:
Use diverse datasets and regularly audit the system for unintended biases.
---
3.3. Surveillance and Privacy
Dilemma: AGI might process vast amounts of user data to identify threats, raising concerns about privacy violations.
Example: An AGI monitoring network traffic might inadvertently collect sensitive user data.
Solution:
Employ privacy-preserving algorithms, such as federated learning, where data is analyzed locally without being centralized.
---
4. Framework for Handling Ethical Dilemmas
4.1. Decision-Making Framework: Ethical Algorithmic Design
Identify Stakeholders:
Assess who could be impacted by the AGI system (e.g., civilians, military personnel, adversaries).
Weigh Risks and Benefits:
Quantify potential harm vs. the benefit of AGI actions.
Implement Precautionary Measures:
Prioritize safeguards for high-risk scenarios.
4.2. Ethical Test Cases
Before deployment, test AGI against scenarios designed to evaluate:
Its ability to handle ambiguous situations.
Its reaction to conflicting objectives (e.g., protecting civilians vs. neutralizing threats).
---
5. Safeguard Implementation Example
Scenario: AGI for Critical Infrastructure Protection
Objective: Detect and neutralize cyberattacks targeting energy grids.
Implementation:
HITL for High Stakes: Human approval required before disconnecting a compromised node.
Explainability: The system must show why a node is flagged (e.g., unusual traffic patterns).
Fail-Safe: A manual override system to revert unintended actions.
Governance: Regular audits by an international oversight body.
---
Conclusion
Addressing ethical dilemmas and ensuring responsible AGI deployment requires a combination of technical safeguards, robust governance frameworks, and transparent operational practices. By proactively integrating these measures, we can mitigate risks while leveraging AGI’s potential for positive applications in militarized systems.
Would you like to explore specific examples of governance frameworks or technical implementations further?
Detailed Exploration of Governance Frameworks and Technical Implementations for Responsible AGI Deployment
---
1. Governance Frameworks for AGI Militarization
Governance frameworks are essential to establish accountability, ethical compliance, and safe deployment of AGI in militarized contexts. Below are detailed proposals:
---
1.1. International Governance Models
A. AGI Treaty for Peaceful Use
Objective: Prevent the misuse of AGI for offensive military purposes while encouraging its development for defense and humanitarian applications.
Key Provisions:
Prohibition of Autonomous Lethal Weapons: Ban AGI from making decisions to deploy lethal force without human oversight.
Data Transparency: Require member states to disclose training datasets and use cases for AGI.
Inspection and Verification: Establish an international body to audit AGI systems in militarized settings.
Dual-Use Technology Regulation: Limit the transfer of AGI technologies to non-state actors or rogue nations.
B. International AGI Ethics Council
Role: Mediate disputes, review AGI applications for ethical compliance, and establish global standards for AGI use in military operations.
Composition:
Multidisciplinary teams (e.g., ethicists, technologists, military strategists, and diplomats).
Representation from diverse geopolitical regions to ensure balanced perspectives.
C. Cybersecurity Collaborations
Objective: Facilitate real-time data sharing between nations to prevent large-scale cyberattacks.
Example: An "AI-CERT" (Artificial Intelligence Computer Emergency Response Team) that uses AGI to coordinate responses to global cyber threats.
---
1.2. National-Level Regulations
A. Ethical Review Boards
Purpose: Require all militarized AGI projects to undergo approval from independent ethical review boards.
Responsibilities:
Evaluate potential societal and security impacts of AGI systems.
Recommend mitigation strategies for high-risk applications.
B. Legislation on AGI Transparency
Key Measures:
Mandate the use of explainable AI (XAI) in all government and military systems.
Require detailed public reports on the deployment of AGI in sensitive operations.
C. Accountability Laws
Implementation:
Assign clear responsibility to organizations or individuals for AGI failures (e.g., unintended escalations).
Establish penalties for negligent or unethical AGI use.
---
2. Technical Implementations for Safe AGI Deployment
Technical safeguards ensure that AGI systems operate predictably and ethically in militarized contexts.
---
2.1. Explainability and Interpretability
A. Explainable AI (XAI)
What It Does: Provides human operators with insights into AGI’s decision-making processes.
Implementation:
Use visual dashboards to represent AGI actions (e.g., traffic flagged, reasons for anomalies).
Example: An AGI monitoring a network attack explains that "unusual traffic patterns originating from untrusted IP addresses triggered the response."
B. Transparency by Design
Approach: Build AGI systems with mechanisms to log every decision, action, and contributing data point.
Outcome: Enables post-incident audits and accountability.
---
2.2. Containment Mechanisms
A. Isolated Testing Environments
Purpose: Prevent AGI systems from interacting with live systems during development.
Example: A "sandbox" environment replicates real-world network conditions, allowing AGI to detect and mitigate simulated threats.
B. Failsafe Activation
Mechanism:
Integrate “kill switches” into AGI systems for manual override.
Example: If AGI behavior becomes erratic, operators can immediately deactivate it.
---
2.3. Ethical Algorithm Design
A. Bias Mitigation
Problem: AGI may inherit biases from its training data, leading to skewed threat detection.
Solution:
Regularly audit datasets to ensure diversity and balance.
Incorporate fairness metrics during model evaluation.
B. Harm Minimization Algorithms
Objective: Prioritize strategies that reduce collateral damage.
Example: An AGI engaged in cyber defense focuses on disabling malicious software rather than shutting down entire networks.
---
2.4. Dual-Approval Mechanisms
Implementation: Require AGI actions to be approved by two independent entities (e.g., a technical operator and a senior military officer).
Example: Before an AGI launches a counter-cyberattack, both a cybersecurity expert and a military commander must approve the action.
---
3. Ethical Dilemmas and Their Resolutions
3.1. Dilemma: Autonomous Decision-Making in War
Problem: Should AGI have the authority to make life-or-death decisions in combat?
Resolution:
Implement strict "human-in-the-loop" policies for all decisions involving lethal force.
Require AGI to provide a detailed rationale for its recommendations, allowing human operators to make informed decisions.
---
3.2. Dilemma: Surveillance and Privacy Infringements
Problem: AGI monitoring networks may collect vast amounts of personal data.
Resolution:
Use privacy-preserving techniques like federated learning.
Example: Data remains local, and only encrypted threat patterns are shared with the central AGI system.
---
3.3. Dilemma: Weaponization of AGI
Problem: Rogue actors could weaponize AGI to launch autonomous cyberattacks.
Resolution:
Develop AGI “anti-missile” systems capable of detecting and neutralizing rogue AGI.
Strengthen international cybersecurity coalitions to track and counter unauthorized AGI development.
---
4. Real-World Implementation Examples
4.1. Defensive Use Case: AGI for Cyber Threat Mitigation
Scenario: A government deploys AGI to protect critical infrastructure (e.g., energy grids).
Features:
Detects anomalies in network traffic.
Provides actionable insights to human operators.
Neutralizes threats in real time without affecting legitimate services.
4.2. Humanitarian Use Case: Disaster Response
Scenario: AGI is deployed to coordinate relief efforts during natural disasters.
Features:
Analyzes satellite data to identify affected regions.
Allocates resources efficiently (e.g., food, medical aid).
Predicts secondary risks (e.g., disease outbreaks) using historical data.
---
Conclusion
Governance frameworks and technical safeguards are vital for the ethical and effective deployment of AGI in militarized systems. By integrating international collaboration, technical safeguards, and transparent ethical principles, nations can mitigate risks while leveraging AGI’s transformative potential.
Would you like further elaboration on any specific aspect, such as real-world governance models, technical algorithms, or specific ethical dilemmas?